In today’s information age, data is growing at an explosive pace and consequently storage requirements within enterprises are skyrocketing. This massive bulk of information is transferred through networks which tie end-users to storage and servers. Given the rate at which data is expanding, every organization needs to ensure efficient storage and management of information.
As interesting as the challenge is, what exactly is required to address it? This is where iSCSI comes into the picture. This blog provides an introduction to iSCSI and further explores the following topics:
- iSCSI architecture
- iSCSI benefits
- iSCSI PDU
- iSCSI components
- Configuration of iSCSI target
- Configuration of iSCSI initiator
- iSCSI Conformance Test Suite
Introduction
iSCSI is an industry standard protocol which allows sharing of block storage over Ethernet. It is a protocol for communicating with I/O devices, chiefly storage devices. iSCSI is an IP-based standard for connecting data storage devices over a network and moving data by carrying SCSI commands over IP networks. In simple words, iSCSI is an interface for communication between initiator and target.
One may ask why iSCSI is recommended over other protocols. iSCSI is very cost efficient and can be easily understood by any IT guy. iSCSI is a flexible protocol which can work within any environment. iSCSI does not require dedicated cabling, it can be run over existing IP infrastructure. It can be deployed on local or wide area networks through the use of Internet across distributed resources. Another reason iSCSI is widely used is because many operating systems support iSCSI configuration.
iSCSI Architecture:
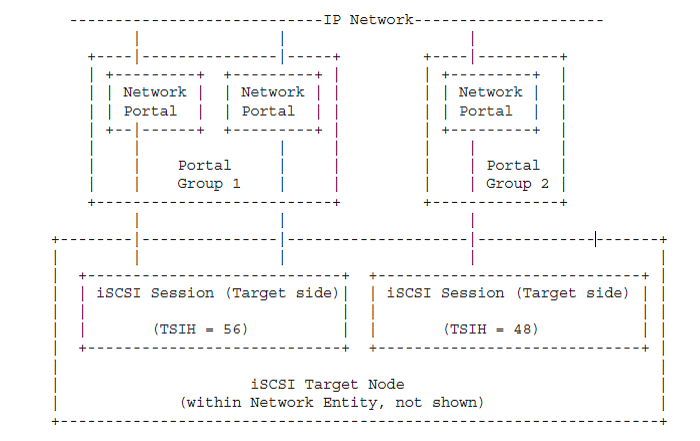
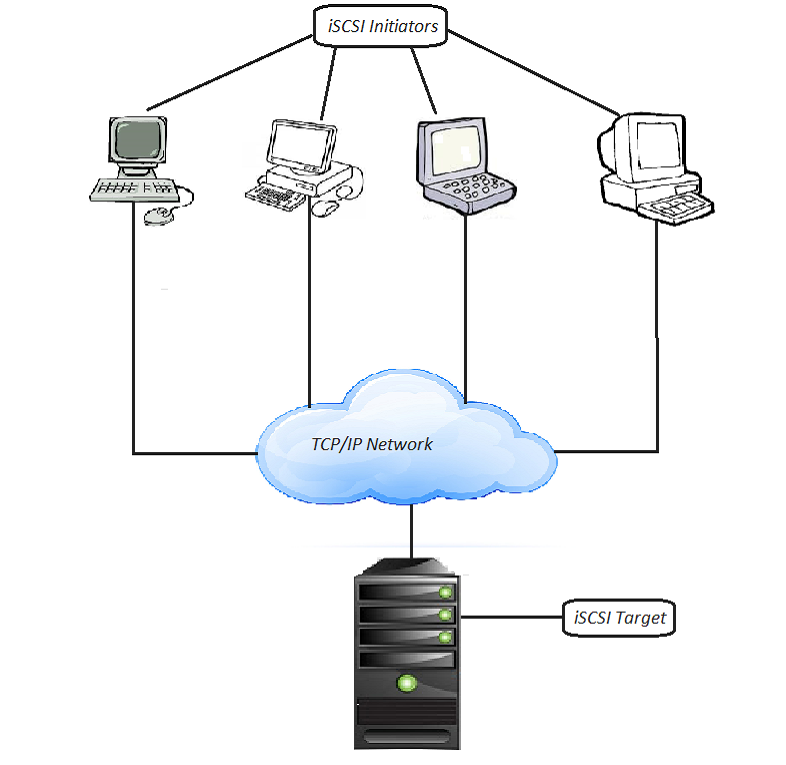
iSCSI operates through a client-server architecture. Clients of an iSCSI interface are called “initiators”. Servers of an iSCSI interface are called “targets”.
Source: RFC 3720
The server that shares storage is called iSCSI target. The server (machine) that consumes storage is
called iSCSI initiator. iSCSI resides on the transport layer of OSI Architecture. iSCSI uses TCP/IP protocol for sharing data.
Why TCP/IP ?
There is no packet loss while transferring data, if there is any loss, it is handled by the TCP/IP stack in the operating system.The iSCSI protocol is a mapping of the SCSI remote procedure invocation model over the TCP protocol. SCSI commands are carried by iSCSI requests and SCSI responses and status are carried by iSCSI responses. iSCSI makes use of the request response mechanism.
The initiator and target divide their communications into messages. The messages are transferred in terms of “iSCSI protocol data unit” (iSCSI PDU). Communication between the initiator and target takes place over one or multiple TCP connections. The TCP connection transports control messages, SCSI commands, data and parameters through iSCSI Protocol Data Units (iSCSI PDUs). The group of TCP connections that tie an initiator to a target form a session.
A session ID defines a session and consists of an initiator part and a target part. TCP connections can be added and deleted from a session. All connections in a session are identified through a connection ID (CID).
The figure below depicts the basic structure of iSCSI using TCP/IP network.
iSCSI Benefits
- iSCSI provides cheap connectivity as compared to FC.
- An existing network can be used for iSCSI implementation.
- As iSCSI is used for block storage, it is very fast.
- IT folks don’t need a lot of training on iSCSI storage since it is very easy to understand and implement.
- iSCSI is an IP-based protocol. It leverages the interoperability benefits of TCP/IP and Ethernet.
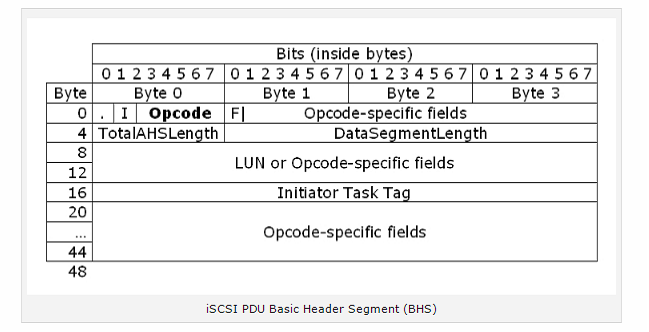
iSCSI Protocol Data Unit(Pdu)
iSCSI PDU is the information unit of iSCSI. PDU is used for communication between the initiator and the target. This communication includes detection of node, connecting and establishing sessions, transporting iSCSI commands and moving data.
The figure below depicts the basic structure of iSCSI PDU.
Operation codes for iSCSI initiators:
Observe that most of these codes are enlisted as “request” codes. The codes below are hexadecimal (hex) and contain the “0x” prefix.
- 0×00 – NOP-Out
- 0×01 – SCSI Command
- 0×02 – SCSI Task Management Function Request
- 0×03 – Login Request
- 0×04 – Text Request
- 0×05 – SCSI Data-Out
- 0×06 – Logout Request
- 0×10 – SNACK Request
- 0×1C-0×1E – Vendor specific codes
Operation codes for iSCSI targets:
- 0×20 – NOP-In
- 0×21 – SCSI Response
- 0×22 – SCSI Task Management function response
- 0×23 – Login Response
- 0×24 – Text Response
- 0×25 – SCSI Data-In
- 0×26 – Logout Response
- 0×31 – Ready To Transfer (R2T)
- 0×32 – Asynchronous Message
- 0×3C-0×3E – Vendor specific codes
- 0×3F – Reject
iSCSI Components
- iSCSI Initiator – The client machine within a storage network is an iSCSI Initiator. The initiator can connect to the target by forming a session among them and can send iSCSI commands.
- iSCSI Target – The server machine within a storage network is an iSCSI target. An iSCSI target is any machine that receives iSCSI commands from an initiator.
Configuration Of An iSCSITarget
iSCSI configuration can be performed on any platform. The configuration shown below is for a Linux environment with Fedora 20 operating system.
Prerequisites for iSCSI configuration include:
- Create two Virtual Machines using Virtual Box. One is for Target and the other is for Initiator. Ensure that both Target and Initiator can ping each other.
- Minimum RAM of 512MB and minimum disk size of 2GB for each VM.
Steps To Configure iSCSITarget
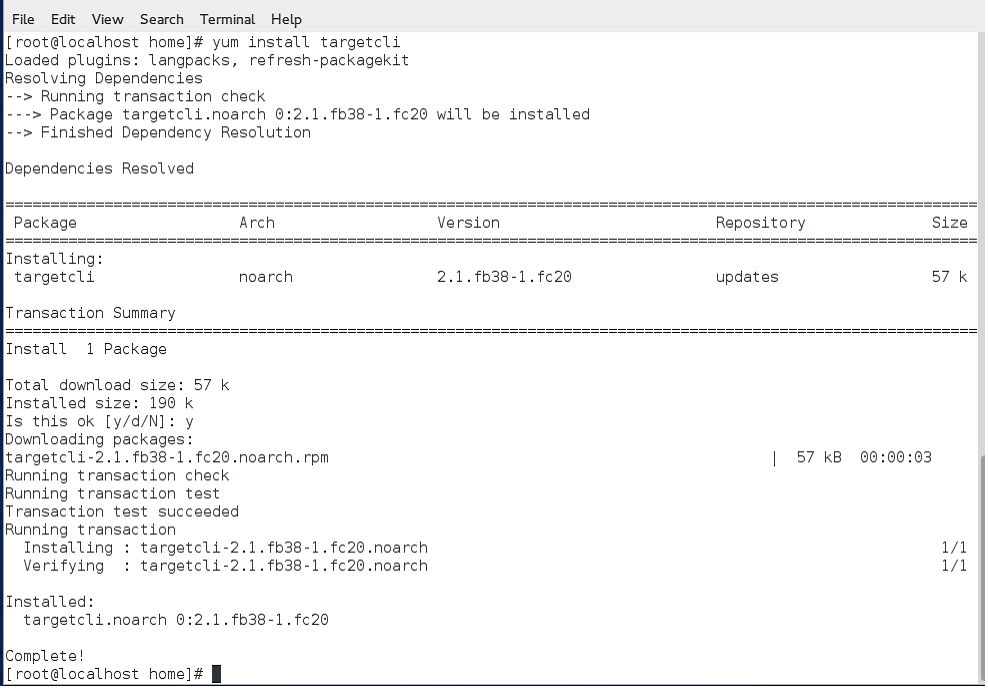
Step 1:- The very first step is to install the targetcli package. Targetcli package is used for configuring the iSCSI Target, to create a disk of the required size and to assign a port number. Targetcli is invoked as root from the command prompt.
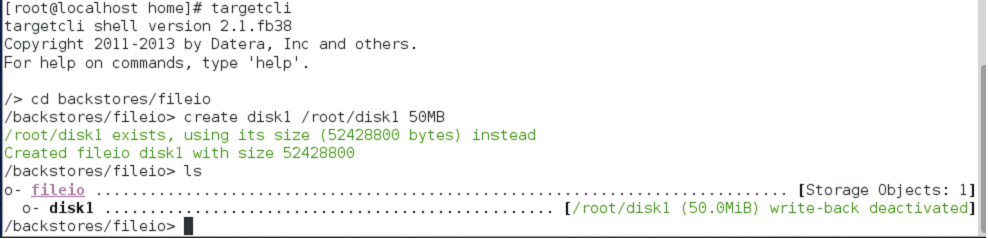
Step 2:- Create a disk of the required size in fileio with a specific name.
After creating a disk in fileio, that particular disk will be in a deactivated state, until the disk is created in a logical unit (LUN).
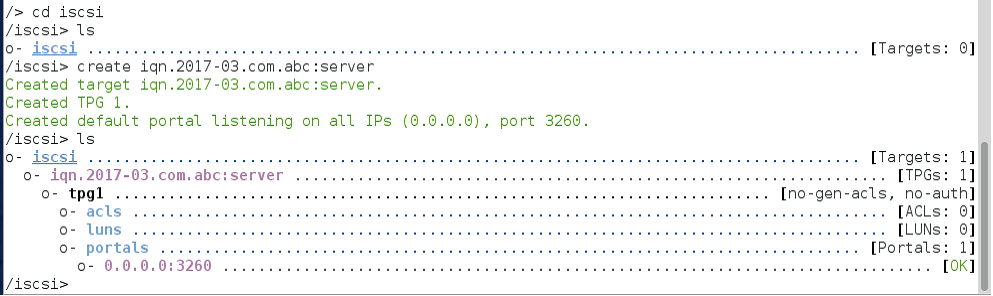
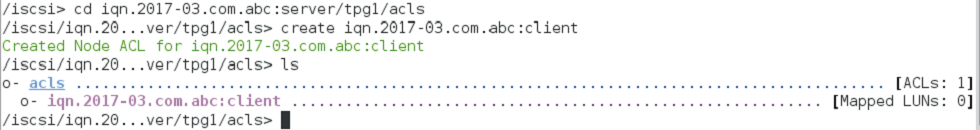
Step 3:- Create a server IQN address with a worldwide unique name used as an identifier. More than one IQN can be specified for it. IQN is created in the iSCSI path of targetcli.
Step 4:- Create client IQN address with the same unique name.
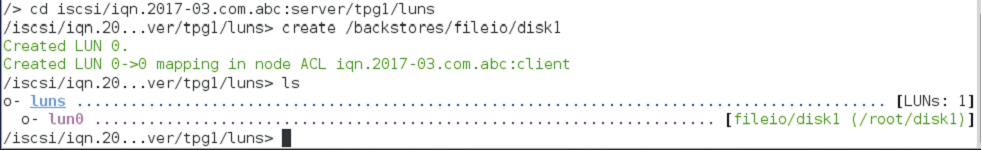
Step 5:- Form a Logical Unit for the created disk
After creating LUN for the disk, it will change to an activated state.
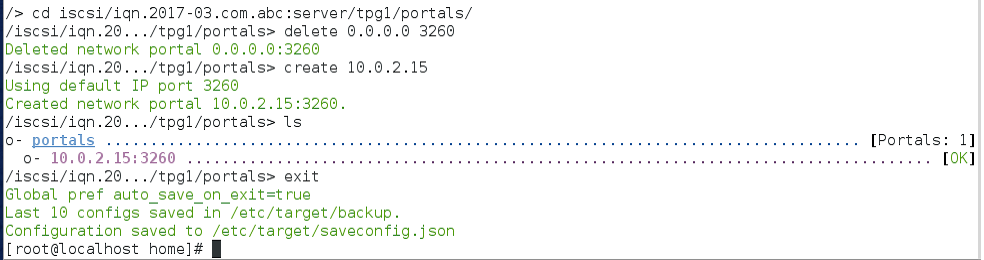
Step 6:- In the path of portals, a default IP is created. Delete that IP and assign an IP for the target.
Save and exit from targetcli.
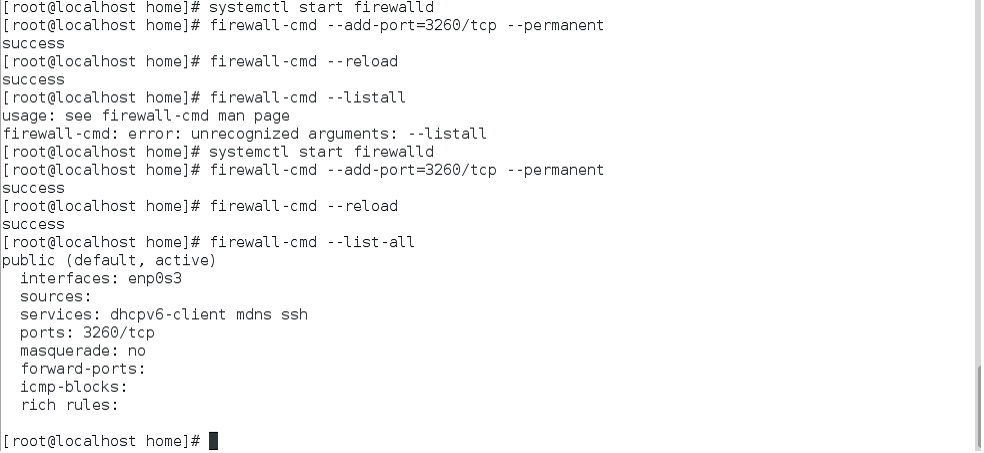
Step 7:- Start the firewall using the systemctl command and make the service permanent.
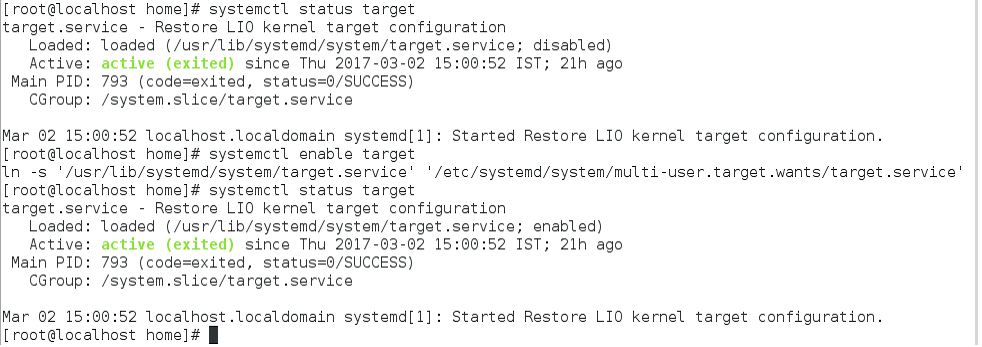
Step 8:- Finally check the status of the target. If it is disabled, enable it.
In the figure above the status of the target is enabled.
The configuration of the target is successful.
Configuration Of iSCSI Initiator
Steps To Configure iSCSITarget
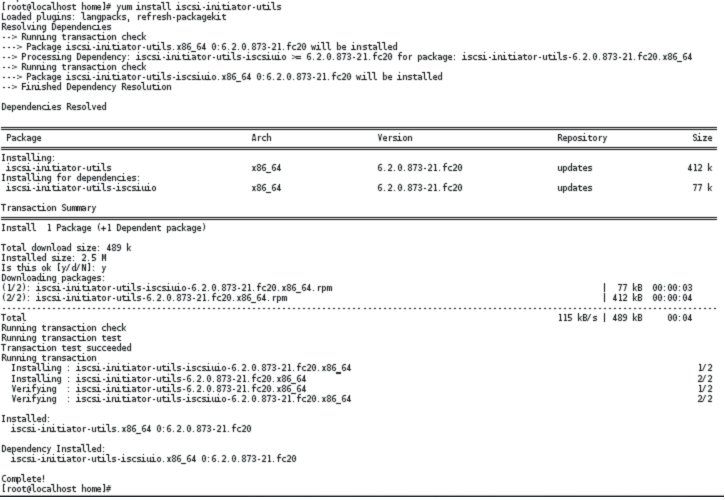
Step 1:- Install iSCSI-initiator-utils package to configure iSCSI initiator.
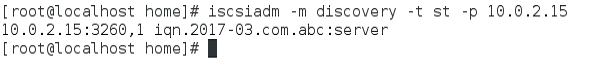
Step 2:- Discover the target using iscsiadm command.
Step 3:- Update the server IQN address in the Initiatorname.iSCSI file as shown in the figure below.
Step 4:- Login to the target using iscsiadm command.
The configuration of the initiator is successful.
iSCSI Conformance Test Suite
So far, we have learned what iSCSI is, where it is used,why it is used, and its pros and cons. Now, let us discuss the iSCSI conformance test suite.
iSCSI has its own standard which is RFC 3720. iSCSI with RFC 3720 can work within any environment.
What is iSCSI conformance testing?
Conformance testing is a non-functional testing method which is used to validate whether iSCSI meets the organization’s agreed standards. Conformance testing is performed to determine if iSCSI initiator and target meet iSCSI standards. This can be done through the iSCSI test suite.
Calsoft has developed its proprietary test suite to enable effortless iSCSI conformance testing. The suite is based on the standards of RFC 3720. For more information visit the following links:
[Tweet “iSCSI: Introduction and Steps to Configure iSCSI Initiator and Target ~ via @CalsoftInc”]
Want to know more about our test suite that enables effortless iSCSI conformance testing?