Have you ever wondered how safe your smart home devices are? In our gradually digital field, everyday items are becoming smart and more connected. This advancement of digital footprints brings incredible convenience but also substantial security challenges.
Internet of Things (IoT) emerged as a business enabler to realise compelling use cases which brings operational and cost benefits across many vertical industries, such as automotive, healthcare, Industrial IoT (IIoT), retail, financial services, manufacturing, and more.
The rapid evolution and adoption of IoT technology has steered digital transformation in enterprise operations, with the prospective to drive up employees and business productivity and profitability.
Despite several advantages of IoT technology, the smart connectivity of massive number of devices presents a significant challenge to enterprises occurring from unsupervised and unsecured devices connected to the network.
So, what is security for IoT, and why does it matter? Continue reading the blog to explore more on IoT Technology and its security.
What is IoT Security?
IoT devices are any devices which connects to the internet and capable of gathering and transmitting data. IoT devices include a collection of industrial machines, sensors, actuators, smart devices, and more which help organizations to gather, and integrate data to steer efficiencies over automation and enable remote monitoring and operations.
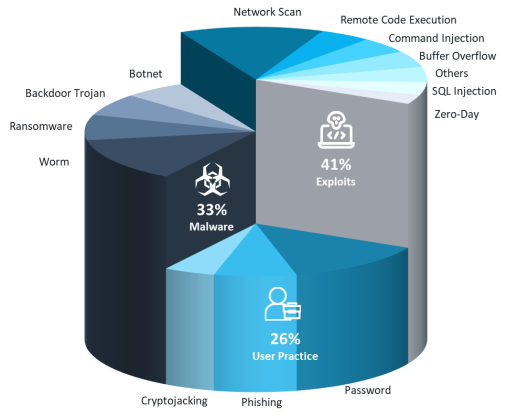
When you think about your smart thermostat, fitness tracker, or even your smart refrigerator, you’re thinking about IoT devices. These devices make life easier by connecting to the internet and each other. However, this convenience comes with a trade-off. IoT security refers to the measures that safeguard these gadgets from vicious attacks and unauthorized access. Ensuring security for IoT is vital because these gadgets gather and transmit sensitive information, making them prime targets for cybercriminals. The following image shows the breakdown of different security threats.
Key Components of IoT Security
An IoT security model can be seen in two views: (a) In a layered architecture, where the security layer spans the entire stack, from the connectivity layer at the bottom to the application layer at the top. (b) An end-to-end security solution, where security is implemented at all points, from end devices to network to cloud. To ensure end-to-end security, a holistic approach must be followed where the security should be implemented at all levels, ranging from end devices to the cloud.
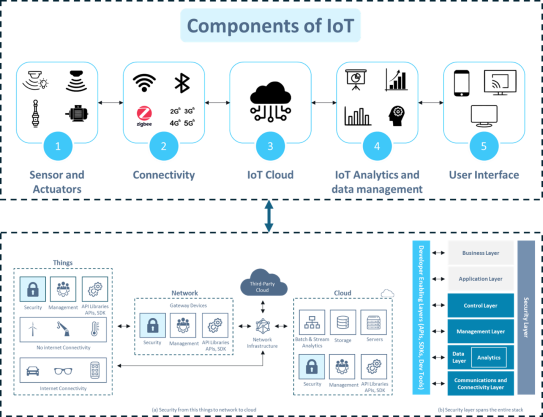
Let’s now learn about the key components of IoT security:
Transducers: Your Eyes and Ears of IoT
Transducers, including sensors and actuators, are the elemental components of security for IoT. Think of sensors as the eyes and ears of your IoT system. They collect vital information from the environment, such as temperature, humidity and motion. Actuators, on the contrary, are the muscles. They take the data from the sensors and execute actions based on it. For instance, when a motion sensor ascertains movements, an actuator can activate an alarm and turn on the lights.
Network Interfaces: The Communication Bridge
Network interfaces like Bluetooth and Wi-Fi are the communication bridges for your IoT devices. These interfaces enable your devices to communicate with each other and share information. Without safe network interfaces, your IoT devices resemble islands that are secluded and ineffective. Ensuring the safety of these interfaces prevents unauthorized access and data infringement. Always use robust encryption and safe interaction conventions to safeguard your network.
Cloud
The data collected from different devices are stored in the cloud. It is important to store and manage massive amounts of data collected from various IoT devices.
Analytics
The data collected needs to be processed and analysed to make real-time decisions. Data is analysed utilising various algorithms like machine learning, artificial intelligence, and more.
User Interface (UI)
User interface is the user-facing software, the visible and user interactive portion of the IoT device which facilitates the user to monitor and manipulate data. An efficient and properly designed UI is preferred to make users interact with the IoT devices easily, enhancing the User Experience (UX).
Examples of IoT Devices: Everyday Smart Tech
You confront IoT gadgets in your daily life more often than you might realize. Smart home gadgets such as thermostats, security cameras, and voice assistants are all part of the IoT ecosystem. Wearable gadgets like fitness trackers and smartwatches are also IoT gadgets, continuously gathering and transmitting information about your health and activities. Even industrial equipment and smart city infrastructures depend on IoT for effective functioning.
By understanding these key components, you can better safeguard your IoT ecosystem from potential risks. Speaking of risks, here’s why securing those smart gadgets is paramount.
Why is IoT Security Important?
What will you do if your smart device gets hacked overnight? To avert this, IoT security is very crucial. Let’s know why security for IoT is vital:
IoT Devices: Rising Influence and Security Challenges
In today’s connected globe, IoT devices are everywhere. From smart fridges to connected cars, these devices make our lives easier and more effective. However, with the progressing number of IoT gadgets comes a substantial rise in security challenges. You must stay ahead of these challenges to safeguard your information and seclusion.
According to a report by Palo Alto Networks, over 98% of all IoT gadget traffic is unencrypted. This frightening statistic indicates that cyberattacks can easily target most of your IoT gadgets. Unencrypted traffic means it is easy for hackers to interdict and manipulate your data. You need to ensure your IoT devices use robust encryption to protect your data.
Potential Access Points for Hackers
Every IoT gadget you connect to your network is a probable access point for hackers. They can manipulate susceptibilities in these gadgets to acquire access to your whole network. Once inside, they can steal sensitive information, launch attacks, or even take control of your connected gadgets. By safeguarding each IoT device, you minimize the threat of a security infringement.
Nowadays, IoT security is very intrinsic. You must take dynamic steps to safeguard your devices and information from potential risks. Now that we’ve covered why IoT security is crucial let’s dive into the common issues and challenges you might face
Common IoT Security Issues and Challenges
Let’s move on to the common IoT security and challenges:
- Remote Exposure and Large Attack Surfaces
Your IoT gadgets are often attainable from anywhere, which is great for convenience but opens a large attack surface. Cybercriminals can manipulate susceptibilities in these gadgets if they’re not adequately safeguarded. - Lack of Industry Foresight
The IoT industry is quickly progressing, and security gauges often lag behind. Without forward- thinking strategies, you risk being extemporaneous for emerging risks and susceptibilities. - Resource Constraints
Many IoT gadgets are small and have restricted refining power. This makes it difficult to enforce powerful security measures. The restraints on resources can leave your gadgets more susceptible to attacks. - Weak Default Passwords
It’s common to discover IoT gadgets with weak or default passwords. Many users don’t change these passwords, making it easy for predators to gain unauthorized access. - Multiple Connected Devices
With the increase of smart homes and offices, you might have several devices connected to your network. Each connected device represents a potential entry point for hackers, increasing your security threat.
Securing your IoT devices is vital to safeguard your personal and professional information. By acknowledging these common problems, you can reinforce your defenses and minimize probable risks. So, what can you do to secure your IoT devices? Let’s break down some effective strategies.
Strategies for Securing IoT Devices
Security of IoT devices is important for safeguarding your network. Let’s look at some pragmatic steps to ensure their security:
- Profile Every Device: Begin by creating a comprehensive profile for each IoT device. Knowing exactly what gadgets are on your network helps you keep track of probable susceptibilities.
- Segment Devices into Separate Network Components: Divide your devices into distinct network segments. This restricts the spread of probable risks and segregates sensitive information.
- Implement Zero-Trust Architectures: Assimilate a zero-trust approach where no device, whether inside or outside your network, is involuntarily trusted. Validate every device and user before sanctioning success.
- Limit Network Endpoints: Minimize the number of endpoints on your network. Fewer entry points mean modest opportunities for predators to acquire access.
- Routinely Monitor and Scan Communication Channels: Frequently monitor and scan your IoT communication channels for any dubious activity. Early discovery helps you acknowledge problems before they become tremendous issues.
- Enable Automatic Software Updates: Set your devices to overhaul recklessly. Keeping software up to date ensures you have the latest security patches and enhancements.
- Change Default Passwords: Always change default passwords on your IoT gadgets. Default passwords are easily assumable and a common entry point for predators.
The following image showcases the best practices to tackle the IoT security challenges, enabling a reliable IoT security posture from unknown threats. Also read Storage and Security in IoT

By following these strategies, you can significantly improve IoT security and safeguard your network from potential risks. Alongside these strategies, implementing strong authentication and authorization mechanisms can further solidify your IoT security.
Implementing Strong Authentication and Authorization Mechanisms
To corroborate security for IoT, you need to enforce powerful authentication and authorization mechanisms. Here are some techniques to contemplate:
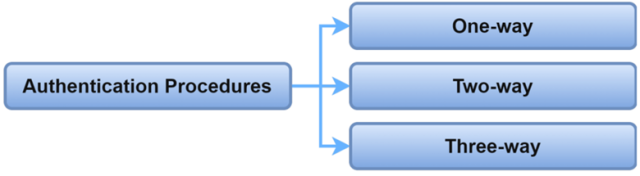
- One-way Authentication: This is where the server corroborates the client. It’s easy but not always the safest option.
- Two-way Authentication: Both the client and server corroborate each other. This technique is safer and extensively used in sensitive applications.
- Three-way Authentication: Adds another layer of security by gripping a third party for validation. This is the safest but also the most intricate.
In addition, IoT device certificates are critical. These digital certificates validate the identity of your devices, ensuring they are trusted and sanctioned. By using IoT device certificates, you improve the security of your IoT network, averting illicit access and probable infringement.
Ensuring Secure Encryption
Want to safeguard your IoT device? One vital step you can’t afford to skip is ensuring adequate encryption. Let’s know why this matters and how you can get it right. First and foremost, you want to safeguard the confidentiality of your information. Without decorous encryption, your data is susceptible to intrusive eyes. By encrypting your information, you ensure that only sanctioned parties can attain it, keeping your sensitive data secure.
Using powerful encryption offers several advantages:
- Confidentiality: Keeps your information exclusive and protected from illicit access.
- Authentication of Origin: Ensures that the information comes from a trusted source.
- Data Integrity: Safeguards your information from being modified during transmission.
- Sender Awareness: Assures that the sender is aware of the transmission, adding an auxiliary layer of security.
Key Management: The Backbone of Data Protection
Efficient key management is crucial for powerful data protection. It’s not enough to just encrypt your information; you must also manage your encryption keys safely. Poor key management can relinquish even the brawny encryption futile. So, pay attention to how you store, rotate and safeguard your keys.
The Role of Encryption
It’s crucial to remember that encryption alone is not a wizardry bullet. While it plays a crucial role in safe communication conventions, it’s not a supersede for other security controls. Ensure you have a thorough security strategy that indulges firewalls, intrusion detection systems, and frequent security audits.
By prioritizing encryption and comprehending its role in your overall security structure, you will be well on your way to protecting your IoT ecosystem. Stay alert and energetic; you will keep your data safe and your operations running smoothly.
Securing Firmware and Software Updates
Frequent firmware and software updates are very integral for your IoT devices. Keeping your gadgets overhauled isn’t just about getting new attributes. It’s about strengthening your security for IoT. Updates are your initial line of defense against cyber threats. When you update your gadgets, you fix susceptibilities that predators could manipulate. Think of it as closing a window that you didn’t know was open. Without these updates, your IoT gadgets remain vulnerable to attacks, putting your whole network at risk.
Intrusion Prevention Systems (IPS)
Not all gadgets can be easily updated. Some might have congenial problems or might no longer receive support from the manufacturer. In such cases, using Intrusion Prevention Systems (IPS) becomes necessary. An IPS acts as an alert guard, continuously monitoring your network traffic and blocking dubious activities. This ensures that even your unpatched gadgets are safeguarded against probable risks.
Remember, protecting your IoT environment involves more than just setting up passwords. Frequent updates and employing IPS where significant can keep your network safe and sound.
Network Access Control (NAC)
You need to enforce Network Access Control (NAC) to manage which gadgets can access your network. This helps you avert unauthorized gadgets from connecting and ensures that only trusted devices have access.
Segmentation of IoT Devices
Segmentation of IoT devices is vital. You should split your IoT devices into distinct network segments to reduce the threat of a single breach compromising your whole network.
Security Gateways
Use security gateways to refine and observe traffic between your IoT devices and the network. This adds an auxiliary layer of security, ensuring that only legal information passes through.
Machine Learning (ML)
Use Machine Learning to improve your security measures. ML can help you detect anomalies and probable risks in real-time, permitting you to answer rapidly and precisely. By integrating these advanced techniques, you can substantially enhance your IoT security and safeguard your network from developing risks.
Parting Thoughts
Safeguarding your IoT devices is not just about securing devices; it’s about protecting your data and seclusion. By comprehending the significance of security for IoT and enforcing powerful assessments, you can relish the advantages of smart gadgets without compromising your safety. Always stay informed and energetic about your IoT security to safeguard your digital life.
For over 25 years, Calsoft has been helping its customers solve their business challenges using technologies in Storage, virtualization, networking, security, cloud, AI/ML, IoT, and telecommunications domains.