If you’ve built a small, successful business but left your software vulnerable to cyber threats, the chances that your business will face irreversible losses will be high too.
This is where software engineering security comes into play. It involves measures to protect software systems from vulnerabilities, threats, and unauthorized access.
State of Application Security report by Synopsys revealed that 78% of organizations experiences a security incident due to vulnerabilities in their software applications.
As software becomes progressively integral to business operations and daily life, it is crucial to address security from the ground up. Effective software engineering security encompasses implementing practices and measures that protect against vulnerabilities, cyber threats, and unauthorized access. This blog post will cover some of the most important insights and strategies for software development security in securing your applications. Dive in!
What is Software Security?
Software engineering security refers to the countermeasures to protect applications from attacks, vulnerabilities, and unauthorized access. It makes sure that all your systems are secure, reliable, and resilient against new threats.
Enterprises look toward how much software they can use for operations, critical data storage, and customer relations. This reliance makes security for software development not only necessary but also core to the integrity of the business and customer trust. The key is to provide software engineering security at each step of SDLC (Software Development Life Cycle).
Security for software development is crucial for the future of every business. Both require proactive measures to ensure long-term security and success.
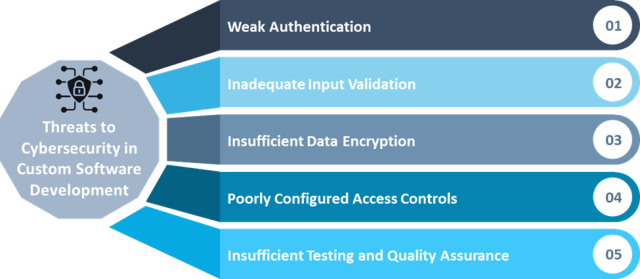
Major Concerns and Threats in Software Security
Weak authentication, poor data encryption, inadequate input validation, and poorly configured access controls are major cybersecurity risks in software development. Additionally, insufficient testing and quality assurance can leave software with exploitable defects, increasing its susceptibility to cyberattacks. Addressing these issues is crucial for maintaining robust cybersecurity in software development.
Ensuring software engineering security is a highly knotty path, coupled with hurdles and odds against it. With the best of intentions, numerous challenges can creep up in the making of an application that is truly secure.
Here’s a glimpse into the common difficulties faced with software engineering security.
- Rapid Technological Changes: The fast-paced evolution of technologies often leads to emerging threats such as zero-day vulnerabilities, advanced persistent threats (APTs), and sophisticated ransomware attacks.
- Constraint of Resources: Budgets and workforce for software engineering security measures fall short.
- Integration Complexity: Seamless embedding of security within existing workflows.
- Human Error: Mistakes made in the process of coding or configuration introduce vulnerabilities.
- Compliance Management: Getting through the maze of regulatory and industry standards.
Why is Software Engineering Security Important?
Software engineering security is pertinent to your software in the digital age. Cyber threats are very sophisticated and require the best development security to ensure the protection of data for compliance and customer trust.
Poor software engineering security brings in severe consequences including financial losses from data breaches, theft of sensitive data, operational disruptions, and potential legal penalties. Companies risk damaging their reputation, losing customer trust, and facing competitive disadvantages. In extreme cases, the cumulative impact may even lead to business closure. Understanding these risks highlights the importance of prioritizing security in software development to secure assets and ensure long-term success.
Efficient software engineering security safeguards your brand’s image and is essential for achieving success in today’s technology-driven marketplace. Time to see why integrating software engineering security into your software development lifecycle means business success.
- Ensures your business continuity: Ensures smooth operation without any disruption of activities due to cyber-attacks.
- Maintains your customer trust: Protection of customer data and privacy to build and maintain their confidence.
- Ensures your compliance with regulations: Meets legal and industry standards, avoiding hefty fines and legal consequences.
- Prevents your financial losses: Lowers the risk of breaches which means no paying hefty recovery and remediation costs.
- Protects your reputation: This protects your brand in case there are published security incidents, including data breaches or ransomware attacks.
- Enhances your competitive advantage: Demonstrates a commitment to security, enhancing the appeal of your business to security-conscious clients.
- Mitigates your risks: Identifies and addresses potential security vulnerabilities before they can be exploited.
- Supports your innovation: Allows for security software development and deployment of new features and technologies without compromising security.
- Strengthens your overall security posture: It enhances your overall security posture through security embedded in every phase of the software development life cycle, enabling resolute defenses against threats.
Understanding why software engineering security will now help you see the difference between security in software development, IT, and cybersecurity.
Software Security vs Cybersecurity vs and IT Security
While the digital threats scanning across the cyber world continue to vary in nature, distinguishing the 3 main security types becomes a very important task.
IT Security is the overarching discipline that encompasses various specialized areas. Within IT Security, Cybersecurity focuses on protecting digital environments from online threats, while Software Security focuses on securing applications and their code.
Here’s a breakdown to help you understand their unique functions and priorities.
| Aspect | Software Security | Cyber Security | IT Security |
| Definition | Protects software applications from vulnerabilities. | Protects digital environments and networks. | Protects IT infrastructure and data. |
| Scope | Software applications and coding practices. | Broad, including networks and systems. | Hardware, software, networks, and data. |
| Focus Area | Secure coding and application vulnerabilities. | Threat detection and response. | Overall IT environment protection. |
| Objective | Secure software from vulnerabilities. | Safeguard against digital attacks. | Secure IT systems and infrastructure. |
| Common Practices | Code reviews and vulnerability assessments. | Firewalls, encryption, network monitoring. | Access control network security measures. |
With a clear understanding of how IT Security encompasses cyber and software engineering security, now look at the four key types of IT security.
What are the 4 types of IT Security?
IT security refers to the procedure for protecting all the data of a given entity, whether electronic or physical. Quite often, IT security and software engineering security are taken to be very close to one another.
While this might be true, IT security is a bit broader and may not always focus on the raining level of criminal activity online with the view of inflicting damage.
Four major kinds of IT software development and security are important in understanding matters of software security.
| Security Type | Description | Key Points |
| Network Security | Protects communication between devices within the same network. |
|
| Endpoint Security | Focuses on securing individual devices like laptops, phones, and tablets. |
|
| Internet Security | Deals with the transit and use of information to prevent cyber-attacks. |
|
| Cloud Security | Reduces security for software risks in the cloud, securing data transfers and devices on the network. |
|
Now that you’ve covered the four types of IT security, check out the key principles for ensuring software engineering security.
Also read Software Security Practices
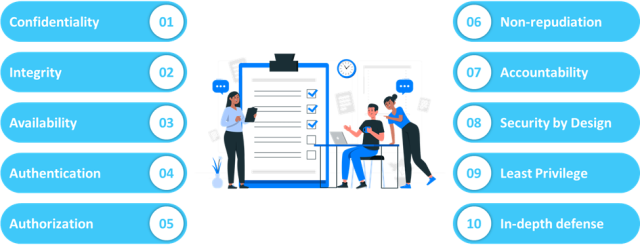
10 Key Principles of Software Engineering Security
Software needs a comprehensive security strategy. This includes various layers of protection to ensure your system is safe from threats. Look into the key principles regarding software engineering security to keep your digital assets safe.
1. Confidentiality
It ensures high confidentiality by making sensitive information available only to authorized viewers. This is a very important principle in ensuring private data is not infiltrated or compromised.
Some of the important practices to uphold confidentiality in security for software include encryption methods, access controls, and secure communication channels.
2. Integrity
Integrity refers to the principle under which data remains valid and intact throughout its entire processing. This ensures that information remains unchanged, intact, and reliable from the time it is created until it is destroyed.
Hashing, checksums, and digital signatures are among the other common techniques implemented in support of data integrity and for detecting changes unauthorized by an organization.
3. Availability
The tenet of availability ensures that at any time, all information or resources become accessible to an authorized entity. This tenet is fundamental in ensuring that a system or data is always up and usable when needed.
Strategies to enhance availability include redundancy, failover mechanisms, and routine maintenance.
4. Authentication
Authentication verifies users, devices, or systems before granting access. This principle establishes a foundation of trust and guarantees that no unwanted entity has any access. Some common modes of authentication include passwords, biometrics, and multi-factor authentication, which involves more than one factor.
5. Authorization
Authorization ensures that proper access to resources is either granted or denied based on user roles and their permissions. This allows users to perform certain actions and view data strictly within their scope of responsibility. RBAC and ABAC are highly applied authorization models.
Here’s a quick comparison of both models.
| Model | Description |
| RBAC (Role-Based Access Control) |
|
| ABAC (Attribute-Based Access Control) |
|
6. Non-Repudiation
Non-repudiation, meaning the assurance that events and transactions cannot be denied after they have occurred, ensures accountability and legal compliance. This aspect is crucial for proving the origin and integrity of data. Digital signatures and audit logs are tools that assist in non-repudiation.
7. Accountability
It maintains a record of user activities in a log, which supports monitoring and auditing security-relevant actions. This principle is very instrumental in detecting and effectively responding to security incidents.
Compliance with organizational policies or regulatory requirements is also possible via this principle. Detailed logging and monitoring systems make accountability possible.
8. Security by Design
Security by Design refers to the philosophy whereby considerations of security are integrated right at the beginning into the software development life cycle.
It represents a proactive way of ensuring that security features form an integral part of the design and development process. This also includes threat modeling, secure coding standards, and security testing, among others.
9. Least Privilege
This ensures that you have only the least possible set of privileges that enable you to perform your tasks. After that, the possibility that the privileges will be misused, either by accident or intention, is diminished. The principle of least privilege is maintained through periodic review and updating of access rights.
10. Robust Defense
Software engineering security in depth refers to the exercise of multiple layers of security controls against different forms of threats. This principle seeks to provide complete security through the combination of physical, technical, and administrative controls in place.
Examples may include firewalls, intrusion detection systems, and security policies sanded up as defenses.
Integrating Security into the Software Development Life Cycle (SDLC)
Skipping security in the software development life cycle means leaving your applications open. It is about integrating security right from the word go, just like the state-of-the-art security system before laying the foundation.
Security implemented at every phase of the SDLC, from planning to design, development, testing, and deployment, constructs a truly resilient defense against cyber threats. These practices are injected into all phases not only to protect your software but to make it reliable against newly emerging threats.
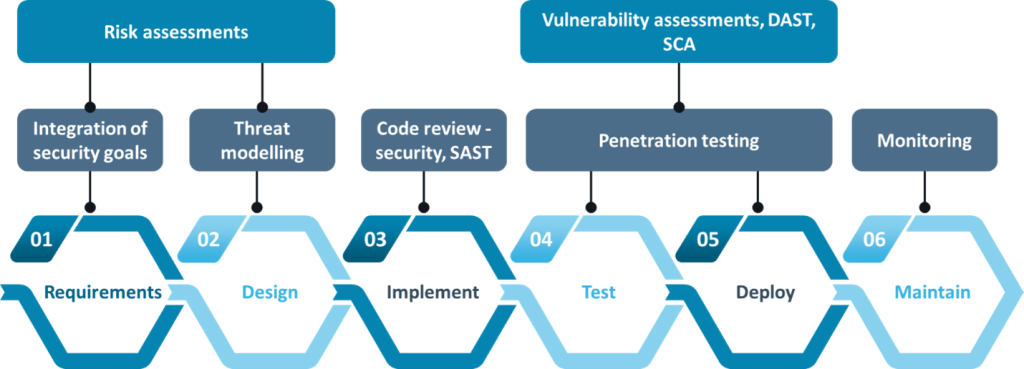
Look at how security can be implemented in the SDLC seamlessly to have robust and secure software.
| Phase | Key Action |
| Planning | Define security needs and assess risks |
| Design | Apply secure design principles |
| Development | Follow secure coding practices |
| Testing | Perform security testing |
| Deployment | Secure configurations and access |
| Maintenance | Monitor continuously and update regularly |
| Training and Awareness | Provide ongoing security training |
Planning
Start with software engineering security requirements and objectives so that, at the outset, they correspond to the regulatory and industry standards. Perform an elaborate risk assessment to identify any vulnerabilities which may impact the project.
This proactive approach ensures that considerations of security are factored in from the outset and set the base for a strong, compliant development process.
Design
Design your software on secure principles such as least privilege, depth in defense, and secure defaults for a good base. Use threat modeling to understand how your software might be attacked and design mitigations accordingly.
Provide data protection through encryption and secure handling mechanisms throughout the whole lifecycle of this system.
Development
During development, follow secure coding practices to avoid common vulnerabilities like SQL injection and cross-site scripting. The code is reviewed regularly for security with an intent to catch the issues early on. There are peer audits.
Run static code analysis tools over source code to catch vulnerabilities before they hit production.
Testing
Put in place a security test strategy that includes the management of penetration testing and vulnerability scanning to identify any security issues present within an application. Dynamic analysis refers to the testing of applications during runtime against security threats.
All security vulnerabilities found in the testing process should be addressed, mitigated, and invalidated.
Deployment
Configure deployment environments securely and harden them against unauthorized access. Implement proper access control to the deployment and production environment, ensuring that access is granted only to authorized persons.
Develop a patch management program to perform updates regularly to counter new vulnerabilities and to keep security up to date.
Maintenance
Keep monitoring your software and deployment environments to ensure that security incidents are detected in real-time so that action can be taken against those incidents.
Design an incident response plan for potential security breaches and manage it. Check up on the security measures from time to time and update them to keep pace with evolving threats to maintain a strong defense posture.
Training and Awareness
Provide training in security and awareness programs to your development teams. Keep them current on the most recent threats and best practices. Moreover, all members of your team should be aware of new vulnerabilities emerging and evolving security trends. This awareness enables them to design and maintain secure software.
Following is the best practice to build strong defenses and help ensure your software is secure against today’s threats.
- Threat Modeling: Software architecture is analyzed for any potential security threats or vulnerabilities, and the design is made with a security mindset in place with controls implemented accordingly.
- Secure Software Coding: Ensure that all software developed is secure by following secure coding practices, input validation, secure data storage, and proper communication protocols. This will prevent the risks of SQL injection and cross-site scripting.
- Code Reviews: These are reviews done on the code to detect and correct security issues early in the development process.
- Security Testing: Conduct regular security testing to identify and fix weaknesses before any deployment is done. This includes testing such as penetration testing and vulnerability scanning.
- Secure Configuration Management: Software systems should be deployed in such a way that they are securely configured. This comprises access controls and network configurations. Customers can have access to the services offered by the utilities.
- Access Control: Ensure a user authentication and authorization mechanism is in place to ensure access is restricted to only authorized personnel.
- Regular Updates and Patches: Apply software updates and security patches against identified vulnerabilities to limit the exposure, thereby further reducing the chance of a breach.
- Security Training: Impart regular security training to developers and other associated individuals in the SDLC process to make them aware of the best practices in security.
- Incident Response: A well-defined incident-response plan for effective identification, containment, and recovery from security incidents.
- Continuous Monitoring: It involves the real-time analysis of logs from systems, network traffic, and user behavior for incident detection and response.
With best practices in place, it’s important to understand how to balance security with development efficiency to maintain both protection and productivity.
Techniques and Resources for Enhancing Software Security
By using the right techniques and resources, you will be able to protect your software against extremely expensive breaches.
Here is a brief on some of the key software engineering security tools and resources that would go a long way in enhancing your software’s defenses.
| Software Engineering Security Tools | Description |
| Static Application Security Testing (SAST) | Analyze source code for vulnerabilities. |
| Dynamic Application Security Testing (DAST) | Tests running applications for software engineering security flaws. |
| Software Composition Analysis (SCA) | Identifies vulnerabilities in third-party components. |
| Mobile Application Security Testing | Assesses software engineering security for mobile apps. |
| Popular Security Frameworks |
|
Parting Thoughts
Understanding the importance of software engineering security is vital for securing software applications from cyber threats and attacks. By employing robust security practices throughout the software development lifecycle, organizations can safeguard sensitive data, prevent breaches, and ensure the integrity of their software. Prioritizing security mitigates risks enhances customer trust, fulfills regulatory requirements, and improves overall operational resilience. As software continues to evolve and become progressively integral to business operations, investing in security measures is essential for maintaining a competitive edge and ensuring long-term success. Adopting a proactive security posture is vital for mitigating potential threats and protecting digital assets.
Calsoft’s security specialist consultants help customers with not just evaluating ‘detect and respond’ capabilities but also AI/ML-based cybersecurity prevention solutions. Calsoft assess security policies and infrastructure by running cyberattack simulations with a wide range of penetration tests to expose and eradicate vulnerabilities and provide a secure foundation for growth.