In today’s digital synopsis, network security management is the backbone of any modern venture. With cyber threats developing swiftly, you need powerful strategies to safeguard your assets. The main purpose of the security strategy in enterprises is to continuously monitor and secure the network from cyber-attacks and threats which could potentially interrupt the business operations and reputation. Hence network security management is critical and certainly very mandatory for all enterprises.
You will learn the significance of network security management from this guide, with clear, applicable steps to improve your security stance. So, let’s dive in!
What Is Network Security Management?
When you think about Network Security Management, you know about the art of administering who gets access to your network resources. This is not just about keeping the bad guys out; it’s about ensuring the right people have the right access at the right times. Managing access efficiently is critical for maintaining a safe and effective network environment.
Network security management is the act of managing access to network resources and monitoring the access to these resources by both internal and external parties.
Network security management is the process of securing network infrastructure by employing security procedures, policies, and tools against threats as shown in the image below. This comprises software-defined perimeter defenses, which protect both physical and virtual devices.
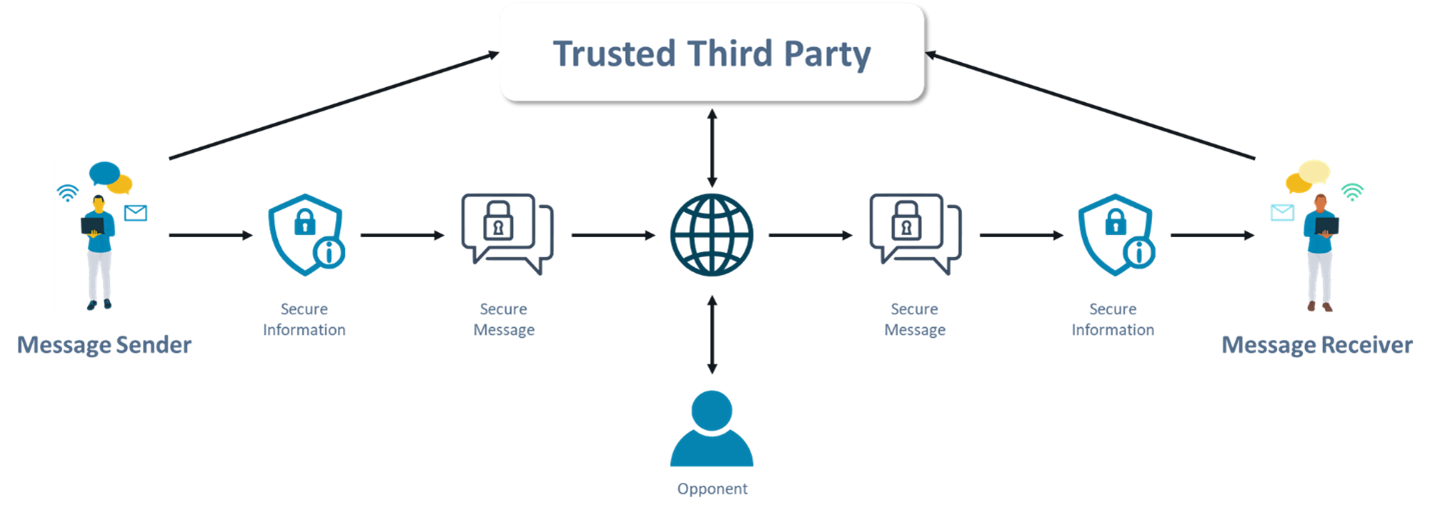
What is and Why Asset Management is Key to Network Security
Efficient security begins with knowing what you have. Asset management in security ensures you have a consummate inventory of all your network resources. It is the systematic process of developing, operating, maintaining, and selling assets in a cost-effective manner. This step is integral because you can’t safeguard unknown assets. By managing your assets, you can prioritize security efforts, reduce susceptibilities, and respond quickly to potential threats.
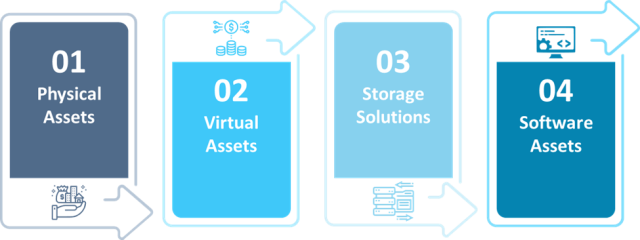
Understanding the Types of Assets in Network Security
Management network security involves a variety of assets, each playing a vital role. Here’s a breakdown of what you’re managing:
- Physical Assets: These are the noticeable parts of your network, including servers, printers, and mobile devices. Keeping these assets safe involves physical gauges such as locks and monitoring, as well as network gauges like firewalls and anti-virus software.
- Virtual Assets: These assets exist only in the cloud which includes cloud-based services and security software. Managing these assets requires ensuring powerful cloud security gauges and frequent updates to your software.
- Storage Solutions: Whether physical or virtual, storage is a crucial element. You must frequently overhaul and safeguard physical backups like hard drives and virtual solutions like cloud storage against illicit access.
- Software Assets: Your network depends on numerous software, from open-source programs to proprietary applications. Susceptibilities and licensing needs accompany each. Efficient management involves frequent updates and compliance with license agreements.
By comprehending and managing these distinct types of assets, you improve your network’s overall security stance. This dynamic approach helps you stay ahead of potential threats and ensures your network runs effortlessly and safely.
Now that we’ve got a handle on our assets let’s dive into the core components that make up a robust network security management strategy.
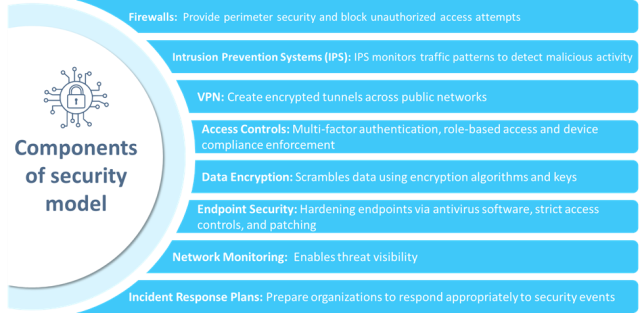
Essential Components of Network Security Model and Management
A robust network security model consists of layered components as shown in the image below, working together to protect the privacy, integrity and availability of systems and data. This layered model comprises people, methods and technology intended to timely detect and prevent threats or attacks.
Efficient management of network security ensures your information and resources are protected from probable threats. To achieve this, here are the key essentials or strategies you need to concentrate on:
- Manage Your Network Infrastructure Efficiently: A well-organized network infrastructure is the backbone of security. Keep your systems sleek and up to date to avert susceptibilities.
- Automate System Update Policies: You should rely on automation for overhauls. Set policies can involuntarily install up-to-date security patches and software updates to keep your network safeguarded.
- Limit Access to Security Resources: Control who can access sensitive data. Enforce strict access controls to ensure that only sanctioned personnel can access vital information.
- Manage Device Updates and Rollouts: Frequently overhauling devices is critical. Ensure all new and existing devices in your network are the latest with up-to-date security gauges.
- Control and Monitor Internet Access: Not all internet traffic is secure. Use tools to administer and observe internet access, blocking vicious sites and managing bandwidth efficiently.
- Detecting Security Threats Proactively: Don’t wait for risks to become infringement. Employ expanded threat detection systems that determine and outweigh probable security problems before they cause detriment.
- Manage Endpoint Security Effectively: Every device connected to your network is a probable entry point for threats. Nourish endpoint security by using thorough security software and frequent monitoring.
- Generate Detailed Security Reports Regularly: Stay informed about your network’s security status. Frequently generate comprehensive reports to dissect security trends, detect anomalies, and strategize enhancements.
By concentrating on these components, you ensure powerful management of network security, safeguarding your information and maintaining trust in your system.
Compliance in Network Security Management
Ensuring management network security is vital for safeguarding your entity’s information and systems. Let’s dive into what this involves, why it’s advantageous, and where it’s most crucial.
Definition and Purpose of Network Security Policies
Network security policies are your organization’s blueprint for maintaining protected systems and information. These policies abstract the rules and practices to protect your network from illicit access, misuse, or theft. They help you ensure that every user and system assent to pioneered security conventions, thereby reducing susceptibilities and safeguarding sensitive data.
Benefits of Enforcing Compliance in Network Security
Implementing compliance in management network security provides several advantages. Firstly, it helps avert data infringement and cyber-attacks, which can save you from substantial financial losses and reputational detriment. Compliance also ensures that your entity follows legitimate and regulatory requirements, avoiding ponderous fines and legitimate entanglements. Moreover, a compliant network elevates trust among clients and investors, showing them that you prioritize their data’s safety.
Certain sectors need to implement compliance in network security more rigorously than others due to the nature of their information and operations. For instance, in healthcare sector, patient history is certainly sensitive. Compliance with regulations such as Health Insurance Portability and Accountability Act (HIPAA) ensures that this data remains confidential and protected. Similarly, government agencies handle crucial infrastructure and sensitive data, making compliance with numerous security standards necessary to national security.
Ensuring compliance in management network security is not just a best practice; it’s a requisite. By enforcing powerful network security policies and implementing them, you safeguard your entity, comply with laws, and build trust with your clients.
Speaking of policies, let’s talk about how to develop effective network security policies that your organization can enforce seamlessly.
Developing Network Security Policies
Network security policies are your blueprint to protecting your digital assets. They depict the rules and processes to safeguard your network from threats. Enforcing these policies is vital to managing network security efficiently, ensuring data incorporation, confidentiality and attainability.
Types of Policies Relevant to Network Security
- Clean Desk Policy: You know the exasperation of misplacing a document. Now, envision sensitive data falling into the wrong hands because of a chaotic desk. A Clean Desk Policy ensures that all confidential data is stored safely, reducing the threat of data infringement.
- Email Policy: Emails are a common entry point for cyber threats. By pioneering an Email Policy, you guide your team on how to manage email communications safely, including determining phishing attempts and avoiding dubious attachments.
- Password Policy: Strong passwords are your first line of security. A powerful password policy authorizes the use of intricate passwords and regular updates. This policy helps avert illicit access to your network.
- Incident Response Policy: You need to respond promptly and effectively when a security incident takes place. Your Incident Response Policy outlines the steps to determine, manage, and alleviate security infringement, minimizing probable detriment.
- VPN Policy: Remote work is more common than ever, making a VPN policy is crucial. . It ensures protected remote access to your network, securing data transmission from external threats.
- Patch Management Policy: Keeping your software up to date is crucial. A Patch Management Policy ensures that all systems and applications receive timely updates, acknowledging susceptibilities before they can be manipulated.
- Software Patching Policy: Like Patch Management, a Software Patching Policy concentrates explicitly on frequent updates for all software applications. This policy helps you maintain the highest level of security across all platforms.
By enforcing these network security policies, you efficiently manage network security, creating a secure environment for your venture functioning.
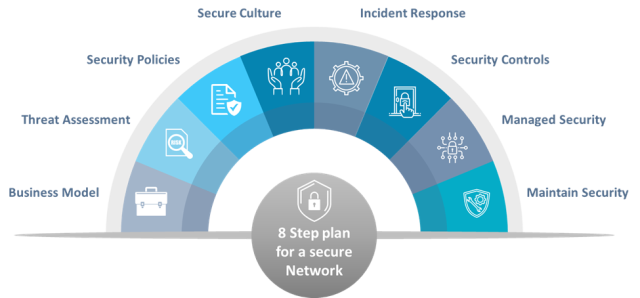
8 Steps to Improving Your Network Security
Looking to corroborate your network security? Let’s dive into eight comprehensive steps to help you manage network security efficiently and safeguard your venture from cyber threats.
Step 1: Be Organized
- Thorough Inventory and Documentation: Begin by creating a thorough inventory of all network assets, including hardware, software, and data. This inventory should be frequently overhauled to reflect any modifications.
- Clear Directions and Guidelines for IT Staff: Ensure that your IT staff has clear, written instructions and conventions to follow. This includes procedures for managing network assets, troubleshooting problems, and responding to security incidents.
Step 2: Develop and Enforce a Strong Password Policy
- Complex Password Requirements: Enforce a password policy that needs the use of intricate passwords. Embolden the use of a blend of upper- and lower-case letters, numbers, and special characters to create strong passwords.
- Recommendations for Effective Password Management: Educate your team on the significance of using eccentric passwords for distinct accounts and contemplate enforcing a password manager to help them manage their passwords safely.
Step 3: Build a Vulnerability Management Program
Regular Software Updates and Patch Management: Pioneer a program for frequently updating software and managing patches. This helps close security gaps that attackers could manipulate. Ensure that all systems and applications are kept latest with up-to-date security patches.
Step 4: Install Endpoint and Antivirus Protection
- Centralized Management of Endpoint Protections: Deploy endpoint protection software across all devices connected to your network and handle these protections from a central console. This ensures uniform security gauges are applied and makes it easier to observe and overhaul devices.
- Ensuring Comprehensive Antivirus Measures: Invest in powerful antivirus solutions that offer real-time protection and regular scans. This helps detect and prohibit malware before it can cause harm.
Step 5: Ensure Firewalls Are Properly Configured
- Strategically Placing and Maintaining Firewalls: Position firewalls at key points within your network to block illicit access. This includes the perimeter of the network and between different segments of your internal network.
- Regularly Reviewing and Updating Firewall Configurations: Schedule frequent retrospect of your firewall settings to ensure they are configured correctly and overhaul them as required to adjust to new threats.
Step 6: Set User Access Permissions
- Implementing Zero Trust or Least Privilege Principles: Assimilate a Zero Trust approach or implement the least prerogative principles by giving users only the access they need to perform their jobs. This minimizes the potential detriment of compromised accounts.
- Using Auditing and SIEM Systems: Enforce auditing and Security Information and Event Management (SIEM) systems to observe user activities and discover dubious behavior. Use these tools to determine and respond to potential security incidents in real-time.
Step 7: Develop Data Backup Solutions
- Selecting Appropriate Backup Tools and Technologies: Select dependable backup solutions that fit your organization’s requirements. This can include cloud-based services, physical backup devices, or an amalgamation of both.
- Defining Clear Scopes, Schedules, RPO, and RTO: Pioneer clear policies for what data requires to be backed up, how often backups should occur, and the adequate RPO (Recovery Point Objective) and RTO (Recovery Time Objective). Frequently test your backups to ensure they can be replenished rapidly and precisely.
Step 8: Don’t Forget Spam and Email Security
Providing Professional Training and Ongoing Security Awareness Programs: Administer frequent training sessions to educate your staff on the dangers of phishing and how to determine dubious emails. Enforce sustained security awareness programs to keep security practices top of mind.
By following these thorough steps, can substantially enhance the network security management. Also read the blog Network Security with SASE to gain more insights on how Secure Access Service Edge (SASE) enhance network security.
Conclusion
The implementation of best practices and certain strategies can enhance the network security and ensure that the digital assets remain protected. Enforcing these strategies today can build a powerful security structure that adapts to developing threats, building trust with your clients and partners.
Calsoft offers unified network security solutions using advanced software as well as hardware technologies to protect the network integrity and data confidentiality of your systems.