As businesses increasingly adopt multi-cloud strategies, understanding the complexities of multi-cloud network architecture patterns and their security implications becomes vital. Multi-cloud environments involve using multiple cloud service providers, each with unique tools and systems, which can create challenges in managing security, data transfer, and infrastructure.
Each cloud provider comes with its own tools, security measures, and management systems, which can quickly become overwhelming. Ignoring these complexities may expose an organization to serious risks, including security breaches, data loss, and operational inefficiencies. With increasing reliance on cloud services, safeguarding the multi-cloud infrastructure becomes essential to maintain security and operational efficiency.
In fact, as per Google Cloud’s survey, business and IT leaders are leaning heavily on cloud strategies. The results are precise:
- 41.4% of companies plan to increase investment in cloud-based services and products.
- 33.4% of companies intend to migrate from legacy software to cloud-based tools.
- 32.8% of companies focus on moving on-premises workloads to the cloud.
These numbers highlight a strong trend: companies are doubling down on cloud adoption to build resilience and maintain a competitive edge. This makes understanding and managing your multi-cloud network architecture more crucial than ever.
Read the blog to get a clear understanding of what multi-cloud network architecture entails. It explores common architectural patterns, examines the core layers, and delves into the security challenges that arise in managing multi-cloud environments.
What is Multi-Cloud Network Architecture?
Before getting into the specifics, it’s essential to understand what multi-cloud network architecture involves.
Multi-cloud network Architecture refers to the strategic deployment and integration of multiple cloud services from different service providers. Its goal is to create a cohesive network.
The setup makes sure that various cloud services operate together while using them independently. This cooperation improves performance, security, and reliability. Multiple clouds allow you to sidestep the risks often associated with depending on just one provider, such as outages or service disruptions.
Components of a Multi-Cloud Architecture
The success of a multi-cloud network architecture relies on several essential elements:
- Cloud Providers: These platforms include AWS, Google Cloud, and Microsoft Azure. Your organization requires the computing resources they supply. Since each provider has unique strengths and weaknesses, you must integrate and manage them effectively.
- Network Infrastructure: This includes physical and virtual networks, which link your different cloud environments. Elements like Virtual Private Clouds (VPCs) and Virtual Private Networks (VPNs) are crucial. They ensure secure and efficient data transfer between clouds.
- Data Management: Managing data across multiple clouds involves more than storing and retrieving it. You must ensure that it remains consistent. It also needs to be secure and compliant across all platforms. This approach helps prevent data silos. It also maintains the integrity of your information across different cloud environments.
Why You Should Choose Multi-Cloud
Unlock flexibility, resilience, and performance for your business with a multi-cloud approach.
- Distribute workloads across multiple providers to prevent dependency.
- Ensure business continuity with disaster recovery options across clouds.
- Leverage the strengths of different providers for specific tasks.
- Spread workloads to reduce the risk of breaches.
- Choose cost-efficient solutions tailored to your needs.
Having explored the components, it’s clear that a well-structured multi-cloud network architecture offers many advantages. Now, let’s look at some of the common Multi-Cloud Network Architecture Patterns. Also read our latest blog on Cloud Infrastructure Services
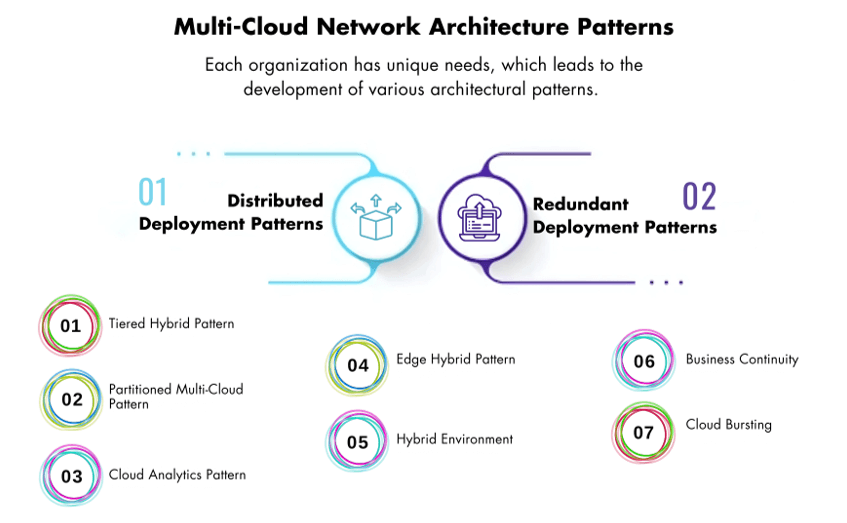
The Common Multi-Cloud Network Architecture Patterns
When working with multi-cloud network architecture, you must recognize that no solution fits every situation. Your organization has unique needs, which leads to the development of various architectural patterns. You can use each pattern to address specific challenges and leverage the strengths of a multi-cloud environment.
Multi-cloud patterns are broadly classified into two categories:
- Distributed Deployment Patterns: These patterns focus on spreading workloads across different clouds for flexibility and performance.
- Redundant Deployment Patterns: These patterns highlight resilience, ensuring high availability by duplicating services across clouds.
Patterns such as Hybrid Environments, Business Continuity, and Cloud Bursting fall under the redundant deployment pattern, which focuses on reliability and disaster recovery.
Let’s look into the most common multi-cloud patterns, highlighting where they fit within these categories.
1. Tiered Hybrid Pattern
The Tiered Hybrid Pattern spreads an application’s layers across multiple cloud environments. This pattern optimizes performance by aligning each application tier (user interface, business logic, and database) with the cloud resources that best suit its needs. The key application tiers are:
- User Interface (UI) Tier: You typically host this on a cloud that provides excellent front-end performance.
- Business Logic Tier: This tier runs on a cloud with strong processing capabilities.
- Database Tier: You store this tier on a cloud known for reliable and scalable storage solutions.
2. Partitioned Multi-Cloud Pattern
The Partitioned Multi-Cloud Pattern hosts different functional components of your IT infrastructure on separate clouds. Unlike the Tiered Hybrid Pattern, this approach does not split the tiers of a single application. Instead, you distribute entirely different services or applications across various clouds. The main benefits realized are:
- Flexibility: This pattern allows you to select the best cloud provider for each function.
- Reduced Risk: By spreading critical services across multiple providers, you minimize the chances of vendor lock-in and enhance disaster recovery.
3. Cloud Analytics Pattern
The Cloud Analytics Pattern handles extensive data analytics tasks. This pattern distributes analytics workloads across cloud providers based on their specific strengths.
- Real-Time Analytics: You run this on a cloud provider that excels in low-latency processing.
- Deep Learning Workloads: You host these on a cloud with powerful GPUs and specialized tools.
4. Edge Hybrid Pattern
The Edge Hybrid Pattern integrates edge computing with cloud resources. This pattern benefits applications requiring real-time data processing close to the source, such as IoT devices or autonomous systems.
- Key Elements:
- Edge Processing: This pattern processes data at the network’s edge, near where you generate it.
- Cloud Integration: The cloud handles more complex processing tasks, with additional resources and computational power available.
- Benefits:
- Low Latency: This pattern reduces the time it takes for data to travel, ensuring faster response times.
- Efficiency: It offloads more straightforward processing tasks to the edge, reserving cloud resources for more demanding workloads.
5. Hybrid Environment
The Hybrid Environment Pattern combines on-premises resources with cloud services. It’s a common strategy when specific systems must be maintained on-premises for regulatory reasons or because of performance requirements.
- Components:
- On-Premises Systems: These often include legacy systems or data that must remain within a specific location.
- Cloud Services: You use cloud services for applications that benefit from scalability and flexibility.
- Why Use This Pattern?
- Regulatory Compliance: You keep sensitive data on-premises while leveraging cloud benefits for other tasks.
- Performance: Critical applications remain on-premises, where you have direct control over performance and security.
6. Business Continuity
The Business Continuity Pattern ensures high availability and disaster recovery across multiple clouds. This pattern is crucial for maintaining operations during failures or outages.
- Key Strategies:
- Redundancy: You duplicate critical systems across multiple clouds.
- Automated Failover: If one fails, your system automatically shifts workloads to another cloud.
- Advantages:
- Resilience: This pattern provides a safety net, ensuring operations continue even during significant disruptions.
- Reliability: It enhances customer trust by reducing downtime.
7. Cloud Bursting
The Cloud Bursting Pattern is a dynamic strategy where you temporarily use additional cloud resources during peak demand.
- How It Works:
- Primary Cloud: This cloud handles your typical workloads.
- Secondary Cloud: This cloud kicks in during peak times, providing extra resources to manage the increased load.
Having seen the common patterns in multi-cloud network architecture, you must understand the foundational elements that support these patterns. Explore these core layers and see how they contribute to a successful multi-cloud strategy.
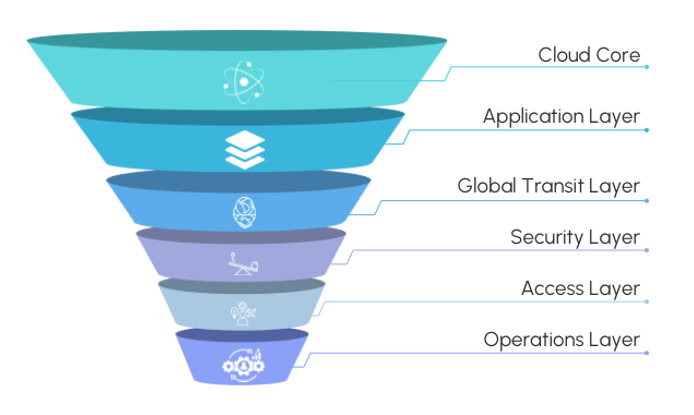
Core Layers of Multi-Cloud Network Architecture
The Core Layers of Multi-Cloud Network Architecture are essential components that ensure your multi-cloud setup runs smoothly and securely. These layers work together to support various multi-cloud patterns, even though their connection might not always be evident at first glance. Let’s go through these layers and their key features.
Cloud Core
The Cloud Core is the foundational layer providing essential services for integrating different cloud environments. This layer includes critical infrastructure components such as computing, storage, and networking. The key features are:
- Integration Tools: APIs and services enabling seamless communication between cloud providers.
- Foundational Services: Core cloud services like virtual machines, storage, and networking.
- Scalability Support: Ensures that the cloud infrastructure can scale to meet the demands of various applications.
Application Layer
The Application Layer is where your applications interact with the cloud infrastructure. It manages applications’ deployment, scaling, and operation across multiple cloud platforms.
- Deployment Management: Facilitates the deployment of applications across different cloud environments.
- Scalability: Allows applications to scale automatically based on demand.
- Orchestration: Coordinates applications’ operations across multiple cloud environments, ensuring they work together efficiently.
Global Transit Layer
The Global Transit Layer manages data connectivity and traffic flow between cloud environments. This layer ensures data moves smoothly and efficiently across clouds, minimizing latency and optimizing performance.
- Traffic Management: Controls data flow between clouds, optimizing routes to reduce latency.
- Connectivity: Creates and maintains secure connections between many cloud networks.
- Load Balancing: Distributes workloads evenly across various clouds to avoid bottlenecks and maintain high availability.
Security Layer
The Security Layer protects your multi-cloud network architecture by enforcing security measures and policies. This layer includes firewalls, encryption, and identity management systems to secure cloud data and applications.
- Firewalls: They protect cloud environments from illegal access and possible dangers.
- Encryption: It ensures that data at rest and in transit is securely encrypted to prevent unwanted access.
- Identity and Access Management (IAM): Controls user permissions and ensures only authorized users can access sensitive data.
Access Layer
The Access Layer focuses on securing access to cloud resources and managing who can interact with your cloud environments and how they do so. It includes authentication methods and user access controls.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring multiple verification forms before granting access.
- Single Sign-On (SSO): Allows users to log in once and gain access to multiple cloud services without needing to re-authenticate.
- User Access Controls: Defines and manages who can access specific resources and what actions they can perform.
Operations Layer
The Operations Layer is responsible for the ongoing management and maintenance of cloud services. It ensures you can efficiently monitor, manage, and maintain your cloud environments.
- Monitoring and Management: Continuously checks the performance and health of cloud environments, addressing issues before they impact operations.
- Automation: Implements automated processes for scaling, backups, and updates to improve efficiency and reduce manual errors.
- Backup and Recovery: Manages data backups and disaster recovery processes, ensuring you can quickly restore data.
Now that we’ve covered the fundamental layers of multi-cloud architecture, it’s critical to understand the security problems that these environments provide. Let’s look at how these problems impact your multi-cloud approach.
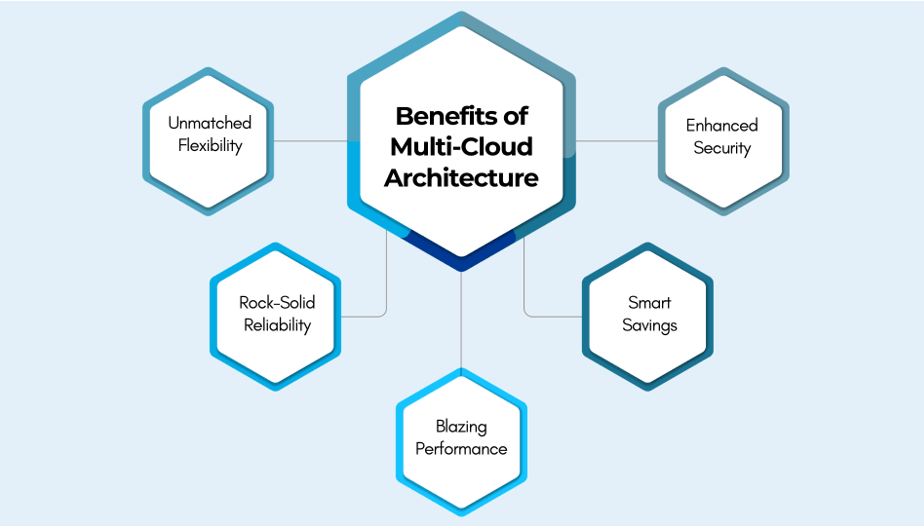
Benefits of Multi-Cloud Architecture
Imagine having the freedom to choose the best cloud providers for each part of your business. That’s the power of multi-cloud architecture! Here’s how it benefits you:
- Unmatched Flexibility: Pick the cloud service that best fits each workload and adapt as your needs evolve.
- Rock-Solid Reliability: Keep your systems up and running by spreading the risk—no more worrying about a single provider’s outage.
- Blazing Performance: Harness the strengths of multiple clouds to turbocharge different aspects of your operations.
- Smart Savings: Spend wisely by scaling resources based on real-time demand and using the most cost-efficient providers.
- Enhanced Security: Feel confident knowing your data and applications are distributed, reducing the chance of a full-scale breach.
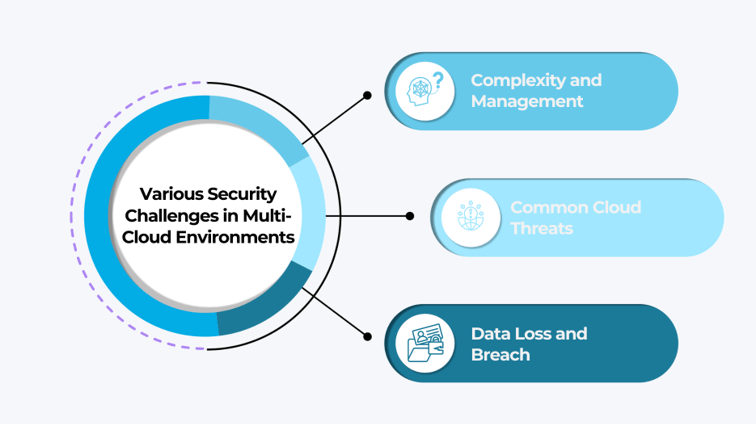
Various Security Challenges in Multi-Cloud Environments
Managing security in a multi-cloud network architecture poses several significant challenges, mainly due to cloud services’ increased complexity and diverse nature. Here’s a closer look at these challenges and what they mean for you.
Complexity and Management
Securing a multi-cloud environment is complex. Each cloud provider has its own security protocols, tools, and interfaces. This diversity makes it challenging to ensure that all security measures align perfectly. These differences can create security gaps, often turning into vulnerabilities that attackers can exploit. The increased burden on your IT teams only adds to the risk. Managing multiple environments increases the chance of errors, potentially compromising your security.
Common Cloud Threats
In a multi-cloud setup, you face a variety of cyber threats. These include:
- Botnets: Botnets can take control of your compromised resources to launch distributed denial-of-service (DDoS) attacks.
- Zero-Day Exploits: These exploits target vulnerabilities that cloud providers may not have patched yet, putting your systems at risk.
- Cryptomining: Cryptomining attacks hijack your cloud resources, draining computational power and increasing costs.
Data Loss and Breach
Data breaches across a multi-cloud network architecture can have substantial financial implications for your organization. Such breaches substantially hamper the organization’s reputation. Since securing data spread across multiple cloud platforms is complex, the risk increases, and consequently, breaches are more likely in a multi-cloud setup.
Insecure APIs
APIs are essential in multi-cloud network architecture but can also bring inherent security risks if not appropriately protected. Unsecured APIs can become entry points for an attacker to drive further attacks, which could be data breaches or unauthorized access. You face a crucial challenge in ensuring your APIs are consistently secured across various cloud services.
Conclusion
Securing a multi-cloud network architecture can be complex, but with the right strategies in place, it is achievable. This blog explored the fundamental layers of multi-cloud architecture, highlighting the various patterns and the security challenges associated with managing multiple cloud environments. A robust security approach is critical to safeguarding data, preventing breaches, and maintaining operational efficiency. Best practices, such as adopting a zero-trust security model, implementing end-to-end encryption, and continuously monitoring for vulnerabilities, are essential in reducing risk. Staying informed and proactive ensures the multi-cloud infrastructure remains resilient, scalable, and protected from cyber threats.
Calsoft leverages its 25 years of product engineering expertise and extensive domain experience to transform business operations through innovative cloud solutions. We ensure seamless connectivity, real-time analytics, and optimized operations, ensuring enhanced productivity and faster results.