The Internet of Things (IoT) in the digital realm is envisioned as a transformative force, reforming industries, people, and daily life. The core enabler of this transformative technology is the IoT cloud architecture. The IoT cloud framework comprises the combination of large number of IoT devices, sensors, connectivity networks, and cloud-computing resources to realize seamless connectivity, data processing, and intelligent decision-making.
With the number of IoT devices rising so steeply, the networks become more vulnerable to cyber threats and attacks. According to Statista reports, the number of IoT devices will nearly quadruple from 15.9 billion in 2023 to 32.1 billion by 2030
This blog delves into the particulars of IoT cloud architecture, explaining its components, functionalities, and significance of security implementation in IoT cloud architecture to steer innovation across diverse industry verticals. IoT cloud security involves protecting information and devices linked to the IoT by using security measures based in the cloud.
But why do you need it to begin with? That’s because IoT devices frequently threaten networks and backend systems. They are susceptible due to their incompatibility with existing tools and the absence of basic security features. Conventional cybersecurity defenses frequently fall short. Continue reading the blog to know about IoT cloud security for your business.
What is IoT Cloud Security Exactly?
The methods and tools known as IoT Cloud Security are created to safeguard the information and functions of Internet of Things devices that are hosted, controlled, or stored on cloud infrastructure. For companies, this means protecting the cloud infrastructure that is used to gather, handle, and evaluate IoT data. The following image shows the IoT cloud architecture highlighting the significance of end-to-end security in the framework.
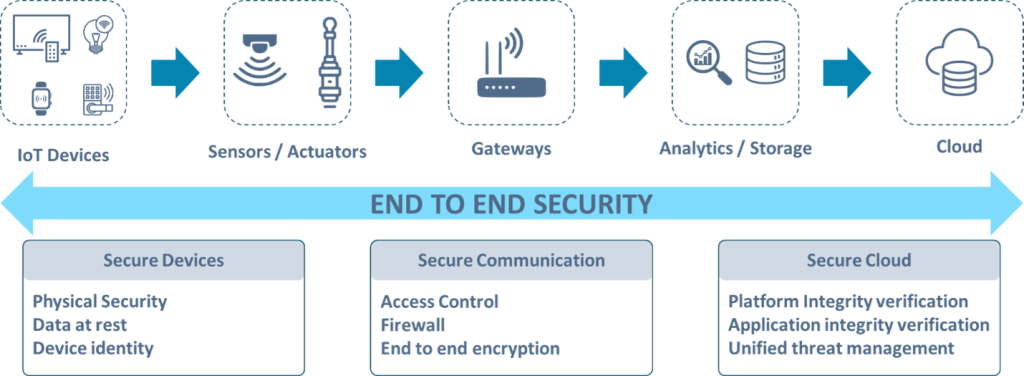
Picture your IoT cloud security as a high-tech digital safe system. Your IoT cloud setup needs strong security steps to protect against attacks and keep out unwanted visitors like how a real safe needs tough locks, cameras, and strict rules about who can get in to keep valuable things safe.
Understanding IoT cloud security is essential, but it’s just as critical to understand how these precautions help your company. So, it’s time to examine how a strong IoT cloud security system improves operations and gives you a competitive advantage.
The Importance and Benefits of IoT Cloud Security
Due to their continual connectivity, IoT devices might invite cybercriminals to breach your networks and obtain private information. These devices can be misused if appropriate IoT cloud security precautions aren’t taken, which could result in serious data breaches and harm to one’s finances or reputation.
Good monitoring gives you visibility into the security state of your IoT fleet and acts as if it were a security guard patrolling your property.
For instance, compromised smart home gadgets that spy on users or medical equipment that malfunctions and puts lives in danger. These are examples of Distributed Denial of Service (DDoS) assaults that compromised devices can launch.
Look at the advantages of putting good cloud security strategy services into practice.
- Your data gets encrypted while moving and when stored using IoT cloud security. This cuts down the chances of data leaks and unwanted access. As per Statista reports, U.S. is set to bring in $342.50bn in IoT revenue by the end of 2024, making these devices more important than ever.
- It ensures the functionality and integrity of a variety of devices that are monitored, secured, and upgraded from one central place.
- Cloud security strategy services ensure you can add new devices without compromising security. This scalability adapts to your changing business needs and technological advancements.
- IoT cloud security minimizes the risk of cyberattacks that cause system outages. A survey by Statista found that 40% of U.S. CISOs cited significant downtime as the top cybersecurity concern for their board. This underscores the need for robust IoT security.
- It helps you comply with strict data protection regulations such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) by maintaining detailed audit trails and protecting against legal repercussions.
- IoT cloud security protects your customer data, enhancing their confidence in your business. Demonstrating strong data privacy measures differentiates your brand in the market.
- Cloud security strategies position your business as a leader in the industry, attracting clients and partners who value solid security measures.
It’s time to dive into the different types of IoT cloud security.
Types of IoT Cloud Security
It’s more difficult than ever to guarantee the security of your linked devices in the rapidly growing IoT space. This requires several levels of protection, in which IoT cloud security strategies use a range of techniques and tools to safeguard the information and services.
Every aspect of IoT cloud security, from advanced threat detection and network segmentation to encryption and authentication, is crucial to safeguarding the digital ecosystem.
Time to explore the key components of security for IoT cloud security systems. Here is an overview before you get into the details.
| Aspect | Focus | IoT Cloud Security Solutions |
| Network Security | Protects the network IoT devices connect to. |
|
| Embedded Security | Security within the IoT device itself. |
|
| Firmware Assessment | Security of the device’s low-level software. |
|
Network Security
Network security for IoT focuses on safeguarding the network that connects IoT devices. This includes securing communication channels both between devices and the network and among the devices themselves. Key measures involve using firewalls, intrusion detection systems, and encryption.
It also includes monitoring network traffic to spot and address unusual activities, often employing AI and machine learning to detect potential threats. When a threat is identified, prompt action is taken to minimize its effects.
Embedded Security
Embedded security focuses on safeguarding the IoT device itself, including its hardware and software. Measures include secure booting, hardware-based authentication, tamper detection, and solutions integrated directly into the device.
It also involves encrypting stored data, ensuring secure data deletion, and protecting interfaces and APIs used for communication.
Firmware Assessment
Firmware, the low-level software controlling IoT hardware, can be vulnerable to attacks that may compromise the device and network. Firmware assessment involves analyzing for vulnerabilities using static and dynamic techniques, and fuzz testing.
Identified issues should be promptly addressed through patching and additional security measures, with regular updates being essential for maintaining device security.
Now that you’ve covered the types of IoT cloud security, it’s time to check the concerns and challenges that come with securing these systems.
IoT Cloud Security Concerns and Challenges
Although utilizing connected devices and cloud technologies has many advantages, the route is not without its hazards. The maze needs careful navigation which avoids the dead ends and traps. Similarly, IoT cloud security demands vigilance to tackle various concerns and challenges effectively.
Getting to know these challenges is very important for guaranteeing that the IoT cloud security infrastructure is good and will resist emerging threats. Here are a few challenges you need to keep in mind.
Weak Authentication and Authorization
Due to their default, easily guessed credentials and lack of support for multi-factor authentication or difficult passwords, many IoT devices are open to unwanted access. Additionally, weak permission might provide attackers access to private data or the ability to carry out illegal actions.
Memory and Processing Power Limitations
Limited memory and processing power in IoT devices can hinder the implementation of strong security measures and regular updates. To address these challenges, lightweight encryption, secure coding practices, and specialized on-device security solutions can enhance protection.
Insecure Communications Protocols and Channels
Data breaches and network assaults are possible when devices and networks transmit data in an insecure manner, which leaves room for eavesdropping and manipulation.
These dangers can be reduced in the following two ways:
- By encrypting data both in transit and at rest
- By using secure communication protocols like TLS (Transport Layer Security) or IPSec (Internet Protocol Security).
Difficulty in Patching and Updating Devices
The heterogeneity and lack of standards among IoT devices complicate regular updates and patching. It is advised to patch update-supporting devices on a regular basis, and to isolate non-updating devices from the network or employ other security measures.
Also Read: Understanding the Potential of Storage and Security in IoT
To better understand these challenges, examine the types of attacks to which IoT devices are most vulnerable.
What Attacks are IoT Devices Most Susceptible To?
As you know by now, IoT devices, by nature, are not the most secure. This compromises the safety and security of the devices they are routed with. If you’ve been wondering what kind of attacks these devices are susceptible to, this section has you covered.
We’ve chalked out the most common yet lethal attacks that IoT devices are prone to. Have a look.
- Botnets: IoT devices, lacking robust security and resources, are prime targets for malware. Once infected, they can be used to form botnets, which flood networks with traffic or send spam, allowing attackers to execute large-scale attacks.
- Ransomware: IoT devices, while not storing valuable data, can still be targeted by ransomware. Attacks may block core functionalities, such as shutting down critical industrial devices or disabling cameras and microphones, disrupting essential business operations.
- Convergence: IT and IoT (or OT) departments face challenges due to differing priorities and skill sets.
– While IT focuses on securing users and data, IoT prioritizes device and network security, with a stronger emphasis on uptime. This gap necessitates rapid evolution and collaboration to address security concerns effectively.
- Invisibility: The rapid growth of IoT device connections often outpaces asset inventories, making it difficult to track and secure devices. Enhanced visibility is crucial for monitoring traffic, detecting abnormal patterns, and identifying potential threats and attacks.
- Legacy & Rogue Devices: IoT installations can introduce rogue devices that replace legitimate ones or are added to systems to operate undetected. These devices enable attackers to create unauthorized access points, compromising network security by controlling ingress and egress traffic.
Now that you know the challenges, it’s time to learn about the main IoT cloud security frameworks and standards created to stop these kinds of problems.
Key IoT Cloud Security Standards and Frameworks
It’s critical to concentrate on important IoT security frameworks and standards in response to this spike since they are vital for preventing such threats and guaranteeing the safety of connected devices.
Here are some frameworks and industry standards that can help you ensure the IoT cloud security devices and systems.
The NIST Framework
The National Institute of Standards and Technology (NIST) has developed an outstanding framework for cybersecurity. This framework provides comprehensive best practices and guidance on managing cybersecurity risks, especially for critical infrastructures. It is versatile and can be adopted by any country or organization, regardless of its size or the level of cyber threat it faces.
Here are more details on this IoT cloud security framework.
| Function | Description |
| Identify | Assists in understanding the cybersecurity risks to systems, assets, data, and capabilities. |
| Protect | Focuses on safeguards to ensure the delivery of critical infrastructure services. |
| Detect | Emphasizes the need to identify cybersecurity events in a timely manner. |
| Respond | Stresses the importance of acting regarding a detected cybersecurity incident. |
| Recover | Aims to maintain plans for resilience and restore any impaired capabilities due to a cybersecurity incident. |
IoT Security Foundation Compliance Framework
The Compliance Framework of the IoT Security Foundation (IoTSF) offers detailed guidance to enhance the security and integrity of IoT systems. It addresses every aspect of IoT security, from physical design to management, ensuring a comprehensive approach to protecting Internet of Things (IoT) environments.
Here are more details on this IoT cloud security framework.
| Aspect | Description |
| Process | Focuses on the overall governance and processes to manage IoT security effectively. |
| Software | Covers software considerations crucial for maintaining the security and integrity of IoT systems. |
| Physical | Addresses physical aspects of IoT devices, including hardware design considerations. |
| Communication | Outlines security considerations for communication between IoT devices and systems. |
Industrial Internet Consortium (IIC)
The Industrial Internet Consortium (IIC) has come up with a complete IoT Security Framework to tackle the unique security problems that IoT devices face in industrial environments. This framework provides security guidelines and best practices for the entire lifespan of an IoT system.
Here are more details on this IoT cloud security framework.
| Aspect | Description |
| Risk Assessment | Zeroes in on spotting and evaluating possible cyber threats. |
| Architectural Considerations | Guides the secure design and deployment of IoT systems. |
| Implementation | Details specific strategies for implementing security controls. |
| Evaluation | Stresses how crucial it is to keep checking and boosting the safety of IoT setups. |
With these key standards and frameworks in mind, explore six effective strategies for managing IoT cloud security.
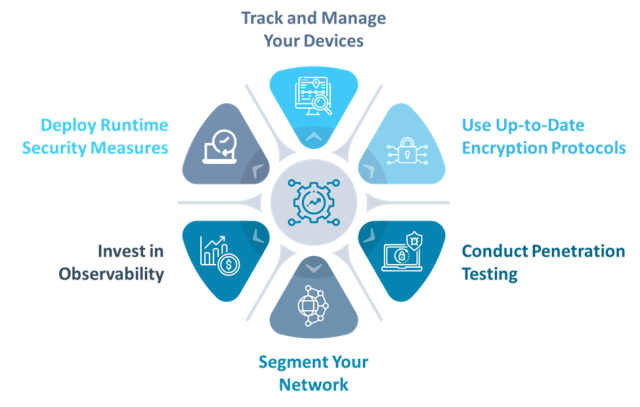
6 Effective Strategies for Managing IoT Cloud Security
Now that you have a firm grasp of the fundamental frameworks and standards pertaining to IoT cloud security, you may investigate practical methods for protecting IoT cloud environments. The most noteworthy ones have been discussed below.
Track and Manage Your Devices
Maintain an up-to-date inventory of your IoT devices, including their configurations and statuses. Understanding the connectivity between these devices is essential, as each connection can pose a security risk. Therefore, having a clear map of your IoT network and how devices interact is crucial.
Effective management also includes regularly applying updates and patches. Manufacturers frequently release updates to fix vulnerabilities, but these are only useful if applied promptly. Regularly checking for and implementing these updates is vital for maintaining IoT cloud security.
Use Up-to-Date Encryption Protocols
Encrypting data plays a crucial role in IoT cloud security. It has an impact on protecting data from unauthorized access even if someone intercepts it.
Put current encryption protocols into action for both data at rest and in transit. Choose Advanced Encryption Standard (AES) when you can, as it strikes a balance between security and performance. Additionally, use strong, unique encryption keys and update them regularly to maintain robust protection.
Conduct Penetration Testing
Regular penetration testing is crucial for identifying vulnerabilities in your IoT cloud environment. This process involves simulating attacks to detect weaknesses in devices, networks, and applications.
Document and address any issues found and perform these tests after significant network changes or the addition of new IoT devices to ensure ongoing security.
Segment Your Network
Network segmentation involves splitting your network into smaller, isolated segments to enhance IoT cloud security. This limits the impact of potential breaches by containing them within individual segments.
To enhance your network security, consider these key practices:
- Place IoT devices on separate segments from critical systems.
- Use firewalls and access controls to manage traffic between segments.
- Regularly update segmentation rules to address new threats and network changes.
- Isolate devices with known vulnerabilities to prevent them from affecting the broader network.
Invest in Observability
Observability in IoT cloud security provides a comprehensive view of your infrastructure for real-time monitoring and analysis. This involves logging and analyzing data from devices, networks, and applications.
A robust observability platform helps detect suspicious activities early. Invest in tools that offer real-time alerts, dashboards, and advanced analytics and ensure they can scale to manage the large volume of data from IoT devices.
Deploy Runtime Security Measures
Runtime security involves protecting IoT devices and applications while they are active. Use behavior analytics tools to identify unusual device activity that might signal a compromise.
Implement runtime security tools that integrate with IoT devices to detect and block threats in real time. Ensure secure communication with control servers for timely threat mitigation instructions.
Parting Thoughts
With more and more IoT devices popping up everywhere, making sure they’re secure isn’t just a good idea — it’s a must. From weak passwords to insecure communication, the challenges are real. But with the right strategies and practices, you can keep data safe and systems running smoothly.
Calsoft develops enterprise-class, highly available, high-performance, secured, and intelligent systems to help our customers – large entities, mid-sized players, and startups in their IoT adoption strategies. Enhance your IoT cloud security to safeguard against potential breaches. Discover Calsoft’s advanced IoT Cloud Security solutions designed to protect your data, ensure compliance, and maintain system integrity.