SDN: A complete guide – Part 2
Now we can connect a client and a server in a couple of different ways – and could be setup in a software-defined network. A Software define…
The NW Toolkit for SDN
With the advent of programmable NW concept, the possibilities of innovation within the NW has increased manifold. However, that also brings up a challenge of revamping the…
Out of the ‘Blue Cloud’: Top Cloud Stories 2014
This year, Cloud Security joined mainstream cloud conversations. Cloud storage generated many of the year’s top news stories; from advanced technology announcements to market changing acquisitions. Here…
SDN – Its Security is Inevitable!
It’s time to drive the SDN wagon further ahead! In the past, we have touched upon aspects that define SDN, understood the “openflow” connection found out what…
SDDC: Extending Virtualization Concepts
SDDC is the abbreviation for Software-Defined Data Center. SDDC is a concept wherein eventually all elements – compute, networking and storage systems in the data center will…
Why SMB3 NAS?
Microsoft has been investing quite seriously in the Network Attached Storage (NAS) protocol SMB 3. This clearly states that NAS is the way ahead. This post summarizes…
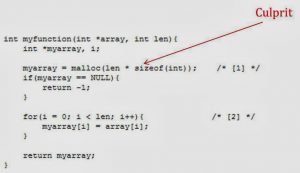
Security Holes – Part 2
In Part-1 of this post we spoke about security holes and 2 sources of vulnerabilities: Buffer Overflow and SQL Injection. We will cover next 3 sources in…
Security Holes – Part 1
Technically, ‘Vulnerability’ is a cyber-security term that refers to a flaw in a system that can leave it open to attacks. In terms of computing, a resource…
Technical Deep Dive: LSM and SELinux Internal Structure
LSM Module: OS Security is a chronic and growing problem: as more systems (and more money) go on line, the motivation to attack rises. Linux is not…
OpenStack Grizzly – 4 Key Facets
OpenStack came up with its new release called ‘OpenStack Grizzly’ earlier this April. This release is seventh in the row and is driven by users who have…
