
Guide to Network Security Key Considerations
We have been hearing a lot lately about the impact of COVID-19 and how it has altered the way businesses are working.

[Infoblog] Network Security
Covid-19 has dramatically increased our dependency on the internet. People are working from home and collaborating digitally, exposing a larger surface to a risk of cyber attack

IA, a Palindrome to AI, also means Infrastructure Agility
With new technologies disrupting the market, customer preferences evolving like never before and market dynamics changing all the time, keeping pace with change is vital.

Cloud Security: Watch out for the Pandemic-spawned Viruses!
Cloud technology provides immense opportunities to scale up and respond to opportunities that the business world presents, but security must not be relegated to a knee-jerk response.
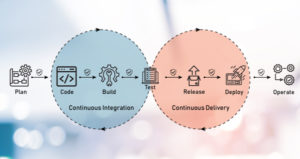
Injecting Security into CICD Pipelines
The CI/CD pipeline was built considering the speed and agility that it provided, but security was never taken into account.

[Infoblog] Cloud Security
Cloud security is assuming prime importance due to the wide adoption of cloud-based applications and software. Here’s an overview of cloud security and how it’s faring in the market.

An Introduction to DevSecOps
With DevSecOps, we can witness a sudden shift in the software development landscape—that of ‘shifting security left’ and making it seamlessly aligned with the development process itself to boost innovation, but securely.

Kubernetes Security: Key Factors to Consider
Here are six ways organizations can increase their Kubernetes security

What You Must Know About Endpoint Protection Challenges
Despite advances in security technologies, the risk organizations face from hackers and insider threats never seems to diminish.

Key Properties of Endpoint Security Solutions
For decades, organizations had considered the antivirus to be the best (and probably the only) solution for securing endpoints. Although antivirus solutions indeed help detect and remove malware, they fall short when it comes to tackling new-age security loopholes.
