Security systems trigger alarms whenever there is a cyberattack. Your IT team is overwhelmed and needs help keeping pace with the relentless threats. You can no longer rely on traditional security measures. To adapt, you need a faster and more efficient solution. That solution is Security Orchestration, Automation, and Response (SOAR).
According to Market research reports, analysts forecast that the SOAR sector will expand significantly from US$1.3 billion to US$3.8 Billion by 2032. This anticipated expansion reflects the growing recognition of SOAR as an essential element of modern cybersecurity architecture. SOAR has transitioned from an optional enhancement to a critical necessity for safeguarding digital assets.
What is SOAR in Cybersecurity?
SOAR is the next step in defense. It represents an advanced approach to threat mitigation and incident response. Think of it like a fire drill but for cyberattacks. Except the drill puts out the fire for you. At its core, SOAR is the framework that smart organizations are adopting to protect their systems.
SOAR is a comprehensive system integrating various security tools into one orchestrated platform.
These tools may include the following:
- Threat detection software
- Incident management systems
- Threat intelligence feeds
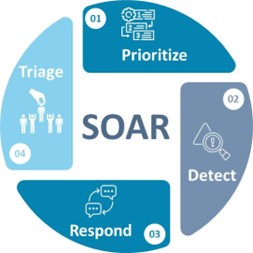
In modern security operations, time is the biggest constraint. Attackers will take advantage of your traditional defense mechanism that assesses threats manually. They will exploit any gap they can find. SOAR helps close those gaps by doing the following critical things:
Orchestration: SOAR ensures that all your security tools and processes work together. It integrates everything into a single workflow, minimizing manual intervention.
Automation: You can automate tasks that are routine, predictable, or previously handled manually. This reduces human error and frees your team to focus on more complex challenges.
Response: SOAR enables fast, automated responses. When your system identifies a security incident, it can immediately execute predefined responses. These could include isolating compromised devices, blocking malicious IP addresses, or even disabling affected user accounts.
In the cybersecurity ecosystem, SOAR is your strategy for staying proactive rather than reactive. Instead of responding to attacks after they’ve done damage, SOAR positions your team to act quickly, decisively, and—most importantly—before the threat can escalate.
How SOAR Works
SOAR is more than just another cybersecurity tool. It is a multi-layered system that transforms your entire approach to security threats. It integrates, automates, and responds faster than traditional methods. Let’s analyze the mechanisms by which SOAR achieves this:
Data Collection
SOAR is the central hub, pulling data from all your security tools. It will use data from your firewalls, endpoint detection, threat intelligence platforms, or SIEM systems. This collected data forms the foundation for everything that comes next. However, SOAR doesn’t just gather data; it does so in real-time. This means that the entire system is constantly in sync with what’s happening across your network. The most common data include the following:
- Logs
- Alerts
- Incident reports
- Threat intelligence from external sources
- Network data
- User Activity
Analysis
Once the data is collected, the system starts its analysis phase. This is where SOAR applies machine learning, predefined rules, and correlating various inputs to prioritize threats. It then identifies irregularities and tries to understand the critical issue. Furthermore, it will also highlight which incidents demand immediate attention. For example, a standalone tool might flag a suspicious login attempt. SOAR then correlates that login attempt with other network anomalies and raises the urgency level.
Automated Response
The final phase is where SOAR automates responses. Once a threat has been identified and prioritized, SOAR executes pre-defined responses without waiting for manual input. Responses can range from simple actions like isolating a compromised device to more complex workflows that involve escalating the issue to human analysts for further investigation.
The automation ensures that the system takes appropriate action when an incident occurs, with minimal delay. Some typical automated responses include the following:
- Quarantining files
- Disabling user accounts
- Blocking IP addresses
Key Components of SOAR
A fully functional SOAR platform has several elements that transform organizations’ management of security incidents. Let’s break each one down:
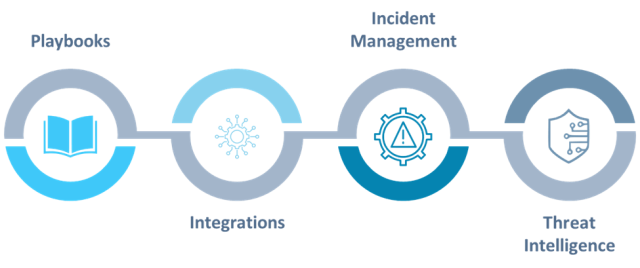
Playbooks
Playbooks in SOAR are predefined, structured workflows that automate the response to specific security incidents. Here’s how they work:
- A playbook outlines a series of steps to follow when it detects a particular type of threat. For example, in the case of a phishing attack, the playbook would dictate specific actions. These could include collecting email metadata, scanning attachments, and alerting the user.
- Once the system triggers an alert, SOAR follows the playbook to execute tasks automatically. For example, it could quarantine suspicious files or block malicious IP addresses.
- Playbooks ensure that the system handles every incident in a standardized way.
- You can customize playbooks to fit your specific policies and risk tolerance.
Integrations
Integration in SOAR is essential for connecting different security tools and systems to form a unified cybersecurity infrastructure. Here’s how SOAR integrations work:
- SOAR integrates with various security tools to collect data.
- These integrations provide a unified view of security incidents. Instead of analyzing fragmented data from separate tools, SOAR compiles everything in one dashboard, improving overall situational awareness.
- SOAR can automate responses across different systems. For instance, SOAR can instruct firewalls to block an IP if a threat is detected.
Incident Management
SOAR creates a structured and automated response to cybersecurity incidents, from detection to resolution. Let’s break down how SOAR handles this process:
- SOAR ingests the data from integrated tools when a security event is detected. This means every event, regardless of source, is processed into SOAR.
- Once the data is collected, SOAR uses predefined rules to classify each incident’s severity.
- After analyzing and prioritizing the incident, SOAR can automatically trigger a response. Playbooks guide predefined actions based on the incident’s nature.
- SOAR cannot resolve all incidents through automation. When it requires human intervention, it escalates the incident and notifies the appropriate teams.
- SOAR generates a detailed report that includes everything from detection to resolution after it revolves around the incident.
Threat Intelligence
Threat intelligence in SOAR plays a crucial role in elevating an organization’s security posture. It integrates real-time, contextual information about external threats. Here’s how SOAR handles threat intelligence:
- SOAR pulls data from multiple external threat intelligence sources. Instead of relying on internal data alone, SOAR continuously monitors global threats and brings that intelligence into your system.
- Threat intelligence enhances the system’s overall contextual awareness. SOAR will never treat every anomaly as a standalone event. It uses intelligence to understand an incident’s broader context.
- Threat intelligence is dynamic—new vulnerabilities and attack methods constantly emerge. SOAR ensures your security strategy stays up to date by continuously ingesting updated threat feeds.
Now that we have a proper understanding of the components, let’s look at the benefits of SOAR.
Benefits of SOAR

When implementing SOAR in your security operations, you gain several powerful capabilities:
- Automated Incident Response: Reduces the need for manual handling of repetitive tasks.
- Tool Integration: Centralizes your SIEM, EDR, firewalls, and other security tools in one platform.
- Playbook Automation: Ensures consistent handling of incidents with predefined, automated workflows.
- Real-Time Threat Intelligence Integration: Incorporates external threat intelligence into your security ecosystem.
- Error Reduction: Minimizes manual errors by automating key processes.
- Scalability: Scales with your infrastructure and security needs as they grow.
- Incident Prioritization: Automatically assigns priority to incidents based on predefined criteria.
- Collaboration Enhancements: Integrates with communication and ticketing systems to streamline teamwork.
- Comprehensive Reporting: Automatically logs all incident activity.
- Compliance Automation: Supports automated workflows to adhere to regulatory and industry requirements.
Now, let’s look at the difference between SOAR, SIEM, and XDR.
SOAR vs. SIEM vs. XDR
SOAR, SIEM, and XDR are vital components in modern cybersecurity. However, they serve distinct purposes, and understanding their differences will help you choose the right tool. We will now look at SIEM and XDR and how they differ from SOAR:
| Feature | SIEM | SOAR | XDR |
| Primary Function | Security Information and Event Management | Security Orchestration, Automation, and Response | Extended Detection and Response |
| Data Focus | Log and event data from various sources (firewalls, servers, etc.) | Comprehensive data from security tools, logs, and external threat intelligence | Cross-layer data from endpoints, networks, cloud, and more |
| Response Capabilities | Limited – primarily generates alerts | Automated and orchestrated responses to incidents based on playbooks | Integrated response capabilities but limited compared to SOAR |
| Automation | Minimal – mostly manual intervention needed | High – automates repetitive tasks and workflows | Moderate – more automation than SIEM but less than SOAR |
| Integration | Integrates well with a variety of security tools, but limited automation | Integrates seamlessly with SIEM, firewalls, endpoint protection, and more | Integrates across endpoint, network, and cloud tools for broader detection |
| Alert Management | Centralized logging and event correlation, but requires human analysis for responses | Automates alert triaging and handles routine responses | Manages and correlates alerts across multiple security layers, offering a unified view |
| Visibility | Focused on log data and event monitoring | Provides enhanced visibility by integrating multiple tools into one platform | Broader visibility across endpoints, network, email, and cloud security |
| Targeted Use Cases | Compliance, event monitoring, and alerting | Incident response, automation of workflows, reducing response times | Detecting advanced, multi-stage attacks across multiple domains |
| Scalability | Can scale with larger enterprises but may require significant resources | Scales well with growing security infrastructure, suited for teams overwhelmed by alerts | Scales well for organizations with complex, multi-layered infrastructures |
| Customization | Highly customizable for log management but less so for response automation | Customizable playbooks and workflows for response automation | Moderately customizable, particularly in correlating alerts across various domains |
When to Choose SIEM, SOAR, XDR
SIEM is ideal when the primary goal is to aggregate logs, monitor events, and correlate data across multiple systems in real-time. Choose SOAR when your focus is on reducing incident response times and automating repetitive security tasks. XDR is a strong choice if you’re looking for holistic visibility across your entire security environment, including endpoint, network, email, and cloud security.
Also read our latest blog on Guide to Security Automation
Use Cases of SOAR
By now, you should have a solid grasp of what SOAR is in cybersecurity and its benefits. Now, let’s look at some use cases of SOAR:

Automated Phishing Response
When a suspicious email enters the system, SOAR automatically takes action. It starts with pulling relevant data from email gateways and user inboxes. It then examines every detail and cross-references them with known phishing indicators.
SOAR then triggers predefined workflows from a playbook, such as quarantining the email and notifying the affected user. Furthermore, the system scans for similar emails across the organization. This helps to identify if there are any potential widespread phishing campaigns. If malicious content is confirmed, SOAR isolates infected endpoints to prevent any further infiltration.
Malware Detection and Containment
Upon detecting malware on an endpoint, SOAR automatically gathers information from the EDR system and network logs to assess the situation. The system quickly correlates the malware signature with threat intelligence feeds. Once confirmed, SOAR uses its playbooks to initiate immediate containment, isolating the affected device from the network. At the same time, it may run automated scans to clean the malware and block associated malicious IPs.
Compliance and Audit Automation
SOAR plays a crucial role in automating compliance checks and audits in regulatory-heavy environments. SOAR continuously monitors systems, collecting logs and configurations from access control systems, encryption mechanisms, and network policies. Regular automated checks enforce and verify all security policies, flagging discrepancies or violations.
With the use cases covered, let’s look at the best practices for implementing SOAR.
Best Practices for Implementing SOAR
- Establish what you aim to achieve with SOAR (e.g., reducing response times and automating repetitive tasks).
- Align SOAR implementation with specific security goals, such as reducing Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
- Provide comprehensive training on SOAR platform management, including playbook creation and automation.
- Implement change management practices to address any resistance from teams used to manual processes.
- Continuously optimize playbooks and workflows to keep up with evolving security threats.
- Regularly update SOAR with new integrations and threat intelligence sources to enhance its effectiveness.
Conclusion
SOAR is more than just an automation tool. It is a critical framework for enhancing security operations. SOAR helps automate response workflows, centralize data, and use real-time threat intelligence. It provides a structured, scalable approach to incident management essential for modern cybersecurity infrastructures.
As cyberattacks continue to grow in complexity, investing in SOAR has become a necessity. SOAR allows you to remain resilient as it handles incidents swiftly and comprehensively views potential risks. This makes SOAR an essential tool for the future of cybersecurity.
Calsoft, as a technology-first company, supports its customers in implementing ServiceNow Security Operations. This comprehensive security solution adopts a holistic approach and is categorized under the SOAR framework—Security, Orchestration, Automation, and Response.
