In Part-1 of this post we spoke about security holes and 2 sources of vulnerabilities: Buffer Overflow and SQL Injection. We will cover next 3 sources in this post.
Integer Overflow
Integer overflow is the result of an attempt by a CPU to arithmetically generate a number larger than what can fit in the devoted memory storage space. The most common result in these cases is for the least significant representable bits of the result to be stored (the result is said to wrap).
Causes
- Poor validation of arithmetic operations
- Lack of awareness of casting order and implicit casts from operators
- Failing to enforce the assumptions made
Redemption
- Choose your datatypes carefully
- Do not rely on implicit typecasts
- Enforce your assumptions by using proper validations and appropriate variable datatypes
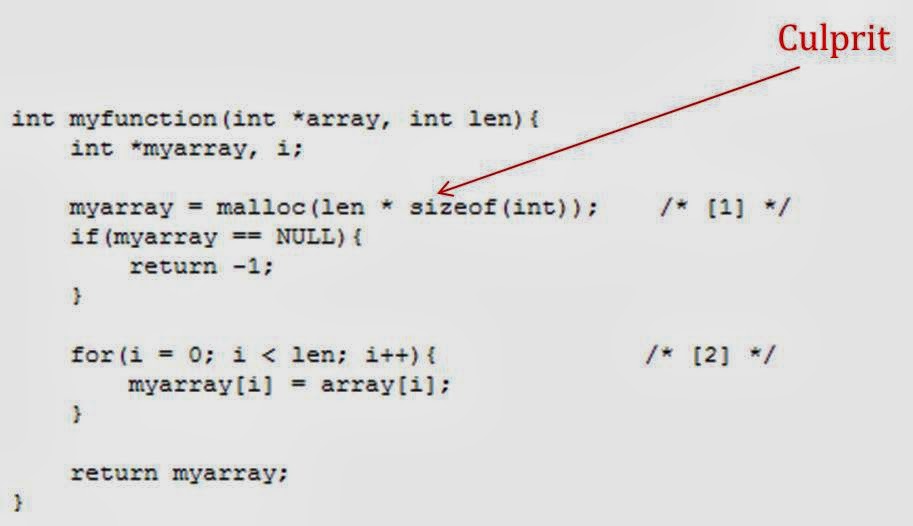
Error Handling
Error handling refers to the anticipation, finding, and resolve of programming errors. An example is the lack of sufficient memory to run an application or a memory conflict with another program.
Redemption
- Never leave a return value of a function unexamined against its respective failure values
- Use conditional compilation blocks for Debugging messages
- When showing error messages to the user, make sure you convey the proper message without leaking out too much of information
Race Conditions
A race condition occurs when two threads access a shared variable at the same time. If an attacker can take advantage of the situation to insert malicious code, change a filename, or otherwise interfere with the normal operation of the program, the race condition is security vulnerability.
The result may be one or more of the following: a computer crash, an “illegal operation,” notification and shutdown of the program, errors reading the old data, or errors writing the new data.
Share your views with us on marketing@calsoftinc.com
Contributed by: Koushal Kawade | Calsoft Inc.