Technically, ‘Vulnerability’ is a cyber-security term that refers to a flaw in a system that can leave it open to attacks. In terms of computing, a resource (either physical or logical) may have one or more vulnerabilities that can be exploited by a threat agent in a threat action. The result can potentially compromise the confidentiality, integrity or availability of resources belonging to an organization.
Vulnerability can exist if the system has a security flaw, an attacker has access to the flaw, and the attacker has the capability to exploit the flaw. Then comes into picture what is called a ‘Security hole’. Security holes/bugs are faults, defects, or programming errors. It is often referred to as ‘an attack surface’ in a system.
At Calsoft, we follow our internal coding conventions and practices to keep security violations at bay. These conventions are designed and managed by a highly experience team of experts that continuously thrive to making it better with each day.
We also use well known utilities like Visual Studio’s Static Code verifier and Memory checking and API call validation tools like BoundsChecker, etc. Besides that we conduct thorough cross code reviews and code explanation sessions that highlight many more defects, even design level defects.
In this post, we will elaborate on:
- Buffer Overflow
- SQL Injection
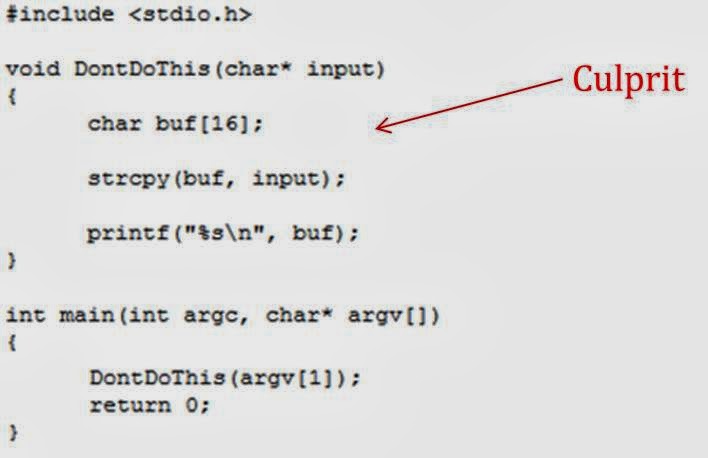
Buffer Overflow
Buffer overflows have been the most common form of security vulnerability. A buffer is said to be overflown when the data (meant to be written into memory buffer) gets written past the left or the right boundary of the buffer. This way the data gets written to a portion of memory which does not belong to the program variable that references the buffer.
Causes
- Incorrect use of buffer/string handling functions
- Incorrect arithmetic calculations with remaining buffer size,
especially in memory allocated on the heap
Redemption
- If you’re making an assumption, make sure you enforce it
- Use the Cch version of strsafe functions
- Use C++ string and container classes wherever possible
SQL Injection
A SQL Injection attack is a form of attack that comes from user input that has not been checked to see that
it is valid. The objective of the attacker is to inject their own SQL into the statement that the application will use to query the database.
Causes
- Failing to check input validity
- Unsafe usage of string concatenation in building the SQL query
Redemption
- Filter any unallowable characters like ‘ “ — ; etc.
- Never use string concatenation to build SQL statements
- Use stored procedures with parameters
Share your views with us on marketing@calsoftinc.com
Contributed by: Koushal Kawade | Calsoft Inc.