Businesses across various industries increasingly depend on IoT devices to drive their daily operations, with many of these devices functioning independently in remote locations, far from direct IT support. Industries such as retail, transportation, and manufacturing are leading the charge in adopting and managing IoT technology to enhance efficiency and improve customer service.
According to a Fortune Business Insights report, the global IoT market is expected to grow by 25% annually, reaching over $1.8 trillion by 2028. This growth underscores the expanding role of IoT in modern business infrastructure. With the increasing reliance on IoT for business operations, ensuring strong security measures is essential to protect sensitive data, avoid unauthorized access, and maintain the integrity of entire networks.
You manage your network, and then one IoT device is compromised, putting the entire system at risk. Be prepared for that reality.
Most IoT devices lack adequate security remote access to IoT measures, making them highly vulnerable to cyber-attacks. These could have devastating impacts, such as data theft or a network breach.
Kaspersky’s report stated that 48% of companies have experienced an increase in cyber-attacks. On its own, that is an indication of increased threats. The problem lies at the heart of the design of IoT devices: designers create them to be connected, not secured. And as their number multiplies, so does the risk that you face.
This blog highlights security remote access IoT devices and will demystify, in detail, the challenges, strategies, and best practices necessary to keep the IoT network secure.
What is IoT Remote Access?
IoT remote access refers to managing, monitoring, and controlling IoT devices from a distant location. With IoT devices spread across various environments—homes, offices, factories, and more—remote access allows users to interact with these devices over the internet or through specific network protocols.
Why is Secure Remote Access for IoT Devices Significant?
The significance of secure remote access for IoT devices cannot be overstated. As these devices often manage sensitive data, from personal information to critical operational data in industries, they become prime targets for cyber-attacks. Ensuring secure access means that only authorized users can interact with the devices, thereby preventing unauthorized access, data breaches, and potential network disruptions. Without proper security measures, IoT devices can be easily compromised, leading to severe consequences such as data loss, operational downtime, and even safety hazards.
Benefits of Remote Access to IoT Devices
Remote Access to IoT Devices offers several key benefits:
- Convenience: It allows administrators and users to manage devices from anywhere, reducing the need for physical presence.
- Cost-Effectiveness: By reducing the need for on-site visits, companies can save on operational costs, including travel and maintenance expenses.
- Real-Time Monitoring and Control: Remote access provides real-time data, allowing immediate responses to any issues or anomalies.
- Scalability: With remote access, scaling operations across different locations becomes more straightforward, as centralized control can be maintained over a distributed network of devices.
Understanding IoT Devices and Their Security Challenges
IoT devices are physical objects that connect to the internet. They collect, transmit, and sometimes act on data. You find them everywhere—from smart home devices like thermostats to complex factory machinery with security remote access IoT risks. These devices improve efficiency by communicating with other systems and introducing significant risks.
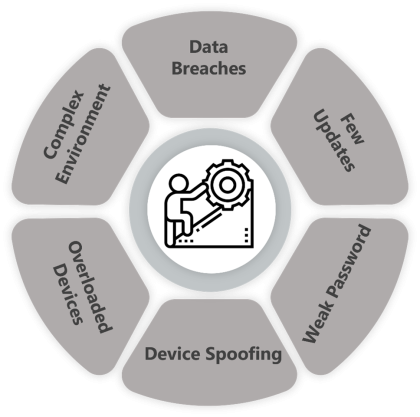
As IoT devices proliferate, they introduce significant security risks. Addressing these challenges is crucial to protecting your network from security remote access IoT vulnerabilities. Here are some common IoT security challenges you will face:
- Default Weak Passwords: Many IoT devices come with default passwords that are simple and easy to guess. If you don’t change these, your network is entirely exposed, like leaving your front door unlocked, and just about anyone can walk in.
- Few Updates: Many IoT devices do not receive consistent updates, making them more vulnerable than regularly updated smartphones and computers.
- Data Breaches: IoT devices handle a lot of data. If compromised, hackers would intercept and steal the data, which can be catastrophic to fields like health and finance.
- Device Spoofing: When hackers pose as real IoT devices, they break into a system. This allows them to manipulate data, disrupt operations, or steal anything of sensitive value.
- Overloaded devices: Most IoT devices are usually underpowered to meet the requirements of complete protection. Thus, they are more exposed to cyber-attacks using their flaws.
- Complex environments: You use IoT devices in various settings, from home networks to industrial settings. The great diversity and complexity of these settings are staggering, making it challenging to maintain uniform security and creating gaps for hackers to exploit.
These challenges underline the importance of secure remote access to Internet of Things (IoT) devices. Understanding these risks forms the first step toward protecting your network. In this section, we look at ways to mitigate those risks.
Also read the blog on Significance of IoT Security
Fundamental Strategies for Securing Remote Access to IoT Devices
Let’s discuss the key strategies for securing remote access to IoT devices. These strategies are essential for protecting your network from potential threats.
1. Network Segmentation
Let’s start with network segmentation. It means putting barriers inside your network. In other words, when you split a network into small segments, you can enclose possible breaches.
The benefit here is that even if a hacker accesses one segment, he won’t be able to move around quickly to others due to solid security remote access IoT controls. Therefore, you should piece everything off, especially when IoT devices connect to other parts of your network.
- Enable virtual LANs to segregate various IoT devices from your network’s more sensitive areas.
- Implement firewalls between network segments to control traffic and prevent unauthorized access.
- Limit who and what has access to each segment. Only allow the necessary communication between segments.
2. Implementing Zero Trust Security Models
Then, you can move to the Zero-Trust security model. This one is simple in concept: Never trust any device by default, both inside and outside your network. Every device must authenticate itself to get authorization for resource access in a security remote access IoT system. This becomes an essential point for IoT devices, which are usually weak in security characteristics and easy to compromise.
Zero Trust treats every access request as a potential threat, minimizing the risk of unauthorized access.
- Segment your network into different zones and apply strict access controls to each zone.
- Implement robust authentication mechanisms to verify the identity of every device and user.
- Limiting access to users and their devices to the minimum helps mitigate the potential impact of a breach.
3. Multi-Factor Authentication (MFA)
The next consideration is Multi-Factor Authentication (MFA). MFA requires more than one form of verification to be allowed into a system—typical scenarios involve passwords and codes sent to a mobile device. This additional level of security can be significant for IoT devices, which are often remotely accessible.
Even when a password gets stolen with MFA, the user won’t be able to access the security remote access IoT device without the second authentication factor. This adds another lock to your door, making it very hard for intruders to break in.
- Device-Specific MFA: Configure MFA for specific IoT devices, especially those with high access or control levels.
- Time-Based One-Time Passwords (TOTP): Use TOTP for devices where biometric or hardware-based MFA isn’t feasible.
- Continuous Authentication: Implement continuous authentication checks to ensure a session remains secure after initial login.
4. Regular Firmware Updates
Regular firmware updates are crucial to maintaining security remote access to IoT devices. Software providers release updates to fix security holes and improve features. If you do not take care of these updates, your devices remain open to known exploits.
It is good to update the firmware regularly. This can help keep your devices secure and functioning normally.
- Where feasible, you should automate firmware updates to ensure all devices are up to date.
- Regularly monitor manufacturer websites and security bulletins for new firmware releases.
- In critical environments, test firmware updates on a few devices before rolling them out network-wide to avoid disruptions.
5. Strong Password Policies
Finally, you should enforce strong password policies. Weak passwords are one of the easiest ways for hackers to gain access. Every IoT device should have a unique, complex password. Avoid using simple passwords like “admin” or “12345.” Instead, create passwords that are hard to guess and change them regularly.
Critical Elements of Strong Password Policies:
- Passwords should include upper- and lowercase letters, numbers, and special characters.
- Ensure passwords are unique for each device and not reused across different systems.
- Mandate regular password changes and enforce expiration policies to minimize risk.
Implementing these strategies strengthens your IoT security. However, securing remote access is an ongoing process. Next, we’ll look at continuous monitoring and how it helps maintain security over time.
Understanding Remote Access Solutions for IoT Devices
Securing remote access to IoT devices is the best way to keep your network and data safe. These devices need a robust solution so that they are not the entry point for a cyber threat. Here is your primary and effective tool for remote access security:
VPNs for IoT
You can open a Virtual Private Network (VPN) to secure security remote access to IoT devices. It forms a safe channel between your devices and the network, encrypting all your data from possible threats.
Also, VPNs obscure the device’s IP addresses, making it challenging for hackers to target and identify them. VPNs provide secure communications from all locations when managing your IoT devices across locations.
Secure Tunneling Protocols
Other security added to tunneling protocols include Secure Shell (SSH) or Transport Layer Security (TLS). These protocols create a safe tunnel for data to pass safely from your security remote access IoT devices to the network. Even if an individual intercepts the data, they cannot read it since it is encrypted.
Secure IoT Platforms
The platform combines the benefits of Virtual Private Networks and tunneling protocols with real-time monitoring tools, making it easy to manage all IoT devices from a single dashboard.
The solutions mentioned above function collaboratively to safeguard against potential threats. They guarantee the security of your IoT devices, even with remote access.
Monitoring and Incident Management in IoT Devices
To effectively secure your IoT environment, you need more than primary defenses. You must actively monitor and manage potential incidents to keep your network safe. This involves continuous monitoring, solid incident response plans, and advanced tools to stay ahead of threats. These elements work together to help you detect issues in real-time and respond swiftly, minimizing potential damage.
Continuous Monitoring
In an IoT environment, devices are always active, constantly sending and receiving data. Continuous monitoring is vital in a security remote access IoT environment, where devices are always active. You need to know immediately if something unusual happens—like an unexpected surge in data or an unfamiliar connection.
Incident Response Planning
You need a clear plan for when things go wrong. It is imperative to tailor your incident response plan for your IoT environment. Here are a few of the steps you can follow:
- Begin by identifying the most critical assets and potential vulnerabilities in your network.
- Then, outline the specific steps to take when a security incident occurs.
- Assign clear roles on who will respond and what actions they should take.
- Test and update your plan regularly to ensure it remains effective. This way, you can act quickly and minimize potential damage when an incident occurs.
Role of Advanced Tools
While it is critical to avoid buzzwords, some advanced tools can enhance your security game. Tools that analyze the volumes of data generated by IoT devices can understand patterns that could indicate a potential threat. You can use these tools to go from reacting to threats after they happen to stopping them proactively before they occur.
Continuous monitoring, incident response planning, and advanced tools are crucial to securing your IoT environment. They help you avoid threats and prepare for rapid action when something goes wrong.
Best Practices for IoT Devices Remote Monitoring
Follow these best practices to keep your IoT devices secure and efficient:
- Keep an eye on your devices 24/7. Get alerts for unusual activity immediately.
- Set up instant alerts for unauthorized access or device issues. Act fast to fix problems.
- Always encrypt data during transmission. Protect your information from being intercepted.
- Update your monitoring tools often. New updates fix security gaps and improve performance.
- Isolate your IoT devices on separate network segments. Limit the impact of any breaches.
- Audit your monitoring processes regularly. Find and fix security gaps.
- Use backup systems to ensure continuous monitoring. Regularly back up your monitoring data.
- Spot potential issues early. Stay ahead of problems with regular checks.
- Have a clear plan for responding to issues. Ensure your team knows how to act quickly.
By following these steps, you’ll keep your IoT devices secure and running smoothly.
Conclusion
Securing remote access to IoT devices is critical for maintaining the integrity and confidentiality of data in an increasingly connected world. As industries integrate more IoT devices into their operations—whether for managing inventory, tracking goods, or enhancing customer experiences—ensuring that these devices are protected from unauthorized access becomes paramount. By focusing on best security practices, organizations can prevent data breaches, protect sensitive information, and maintain operational efficiency. Ultimately, securing remote IoT access not only enhances the reliability of technological systems but also builds trust with customers and partners by demonstrating a commitment to protecting their data and privacy.
Calsoft’s IoT services portfolio is comprehensive and designed to cater to the diverse needs of our customers. We offer offers intelligent frameworks and digital services to deliver IoT-powered solutions.