Cyber-attacks are not new. They have occurred in the past and will continue to surface in the future. Since such incidents are regularly getting featured in the top news, it indeed is a clear sign that cyber security needs to be taken seriously more than ever. With the proliferation of digital technologies, online connectivity expansion, and the precision and upgradation of notorious tactics by cybercriminals, staying safe in the virtual world has become inevitable.
Incidents like data leaks, to ransomware attacks occurring regularly make it evident that no one is completely safe, and damage can happen at any time. So, what are enterprises doing to tackle this? Do they have a contingency plan in place to deal with the challenge head-on and not hamper business continuity?
Well, this is where getting to the depth of understanding the intersection between cyber security and business continuity comes into play. Remember, having a robust and resilient cybersecurity plan is not plan B but a necessity to keep up the survival instinct of any business. Be it small, large, private, or public, cyber threats have the potential to have a cascading effect on data security and business operations and bring them to a standstill along with various other consequences. In this blog, we plan to help you foolproof your business with the best cybersecurity information essential to maintaining healthy business continuity and tips to quickly bounce back from potential cyber threats.
Is Your Workplace Cyber-Secure for Uninterrupted Business Continuity
Enterprises often play safe by having in place a disaster recovery plan as well as a security recovery plan to keep their business away from the cascading aftereffects of a natural disaster or a cyberattack.
The table below will help you a get better idea about the four main areas covered and the thin line of difference between the two.
| Preparedness Components | Disaster Recovery Plan | Security Recovery Plan |
| Primary Objective
|
Ensures operational resilience post-disruption caused by human or natural disasters | Safeguards data assets in the event of a security breach |
| Response Requirements | Transparent communication with stakeholders for swift and faster operational recovery | Covert actions for evidence preservation, analysis, and future prevention |
| Tactical Difference | Emphasizes rapid restoration of operations | Focuses on strengthening protective measures to prevent recurrence |
| Plan Management | A team dedicated to refining recovery strategies based on past experiences | The team constantly updates protocols to address evolving cyber threats |
Cybersecurity is an extremely crucial aspect that businesses cannot afford to overlook. Gartner states, that since the outbreak of Covid, 61% of organizations have experienced a 25% increase in cyber threats or alerts. These numbers indeed are alarming and along with a resilient plan of action in place, businesses require the right information on cybersecurity.
According to Mordor Intelligence, the cyber security market size is estimated at USD 234.01 billion in 2025, and is expected to reach USD 424.14 billion by 2030, at a CAGR of 12.63% during the forecast period (2025-2030).
So, what is cybersecurity, and how can it complement business continuity are two questions of great importance. Let’s unfold!
Given the value data can bring to a business, it is not wrong to say that data is the new gold. This is the primary reason why data protection and security has become an international agenda. Data leaks, destructive cyber intrusions, and security failures have the potential to put the world economy at risk, putting the spotlight on heightened security measures.
Cybersecurity secures digital systems, networks, and data against cyber threats like hacking, malware, and data breaches. This concept is woven with a wide range of practices and technologies directed toward saving businesses from possible damage of the virtual world. In terms of business continuity, cybersecurity ensures critical business systems continue to operate even during disruptions. By adding a defense mechanism against cyber-attacks and data security, the integration of cybersecurity helps maintain business operations, reputation, and customer trust, particularly in the digital age.
However, for businesses to put cybersecurity into action they need to have a Framework in place.
Cybersecurity Framework:
Frameworks primarily are a structure of guidelines or standards used to work out complex problems. In cybersecurity, frameworks offer a systematic approach that can be utilized by organizations to effectively manage risks, exercise control, and strengthen the security landscape.
The US National Institute of Standards and Technology or NIST has built on a Cybersecurity Framework as shown in Figure 1, to help organizations mitigate cyber risks.
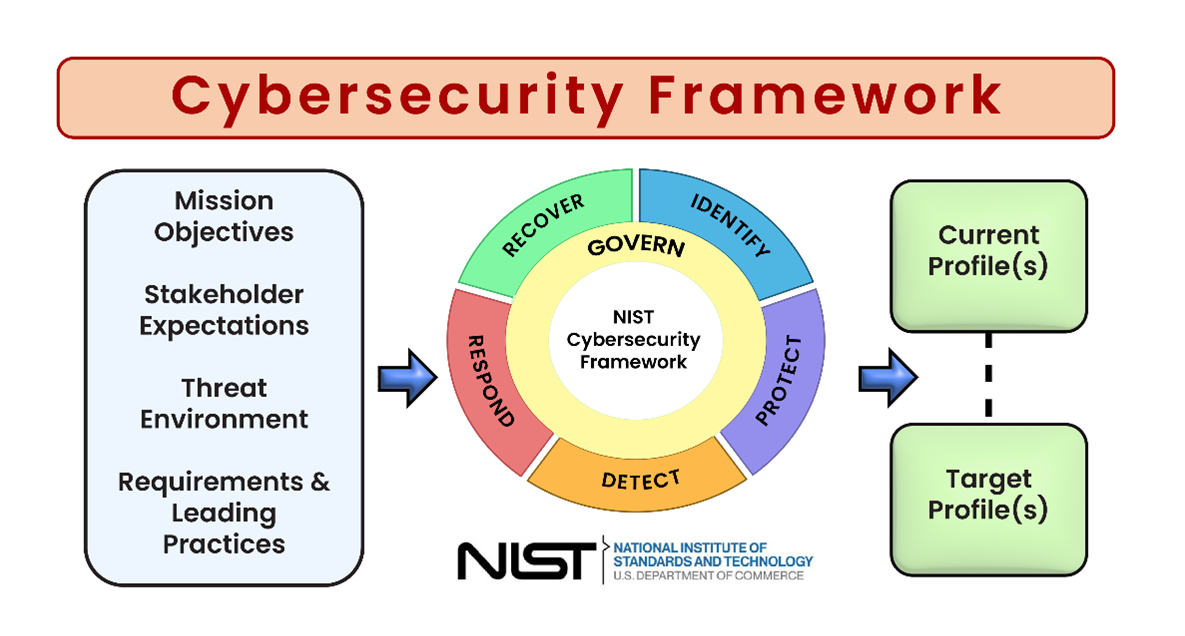
Here is what the diagram represents:
The diagram above displays six crucial elements prescribed by NIST for cybersecurity risk management. It aims to provide a high-level taxonomy of cybersecurity outcomes and the mechanism to manage them.
1.Govern
Governance is a cross-functional element that helps get a fair enough understanding of how a business can achieve the next five. This is the latest stage and is essential to rationally integrate cybersecurity into the organization’s overall risk management strategy.
2.Identify
In this stage, as prescribed in the NIST Framework, organizations must conduct an audit to get a fair idea about which systems are truly critical for business operations. Once done, this audit helps get a good understanding of the core systems, informing businesses to align the cybersecurity strategy to prioritize the protection of these processes.
3.Protect
After taking stock of the core systems and making a strategy to up the guard and prioritize their defenses, businesses must implement cybersecurity safeguards and practices in real-time. Simultaneously, it is essential to include awareness and training, identity management, access control, platform security, data security, and more so, that organizations can reduce the chances of malicious cybersecurity incidences.
4.Detect
What is the use of implementing a strategy if you cannot detect the issue? A resilient cybersecurity strategy must be constantly monitored. As cyberattacks often are silent killers and can ambush your system out of nowhere, businesses need to have a force of cybersecurity professionals, who can gauge the threat beforehand, making remediation and mitigation of potential threats easier.
5.Respond
In case a cyber threat is identified, it is the decision of the cybersecurity team on how to respond. This needs a mix of elements like communication, isolation, damage mitigation, and event analysis. The response element is a mix of the above-mentioned points.
6.Recover
Last but not least, recovery is an essential component of the NIST cybersecurity framework, that involves a strong business continuity strategy to be marked as an important element of the broader cybersecurity strategy. Remember, business continuity and disaster recovery plans have the potential to keep your business prepared for the worst. However, having a robust plan of action to combat unforeseen cyber threats or attacks is a must.
A cybersecurity framework is essential for enterprises to build a protective layer for data security. But is that enough to have your business up and running even during a crisis? Well, cybersecurity strategies or cybersecurity frameworks are extremely essential, but having them intersect with the business continuity model is inevitable to have your business function even in the event of a cyberattack. But to make the combination of cybersecurity and business continuity work, we must know it from the ground up. So, without any ado, let’s find out what business continuity is.
Understanding Business Continuity
Businesses can fall prey to a host of risks leading to a series of consequences such as financial loss, reputational damage, legal liabilities, data loss, and most of all operational disruption. To keep such uncertainties at bay, businesses need to put together a logical business continuity plan.
Definition of Business Continuity Plan (BCP) and its Significance
Business continuity planning in layman’s terms is a process designed for a quick and smooth revival of operations after the occurrence of any unpredicted or unplanned event like natural disasters, cyber-attacks, etc. Broadly it is one of the most critical components of risk management for any business. It includes a process for identification of the organization’s vulnerability toward exposure to internal and external threats, building a protective layer, and providing efficient prevention and recovery while maintaining a competitive edge and value system integrity.
BCPs are significant for businesses. It is not wise for businesses to only rely on insurance because it cannot cover every aspect and cannot promote restoration of operations to foster business continuity. It is the process that is conceived in advance to keep threats controlled and be ready to respond to unforeseen events with prior inputs from stakeholders.
Decoding the Much-Needed Intersection of Cybersecurity and Business Continuity
A ransomware attack can bring systems that are mission-critical for the smooth operation of your business to a standstill. Whereas a cybersecurity business continuity plan can feel like an oasis to quickly recover from shocking events. Such plans help stay well prepared for the day when a cyberattack ambush takes place, preserve access to data and systems reduce the aftereffects, and get back to work faster.
As mentioned in the beginning, data security is an international concern and there are several international cybersecurity principles and standards like ISO 22301, ISO/IEC 27001, NIST SP 800-34 – and more laid to address the question of business continuity.
Calsoft has helped a leading tech company based out of the US, involved in secure cloud hosting, business continuity, Disaster Recovery (DR), and Workspace-as-a-Service (WaaS) solutions monitor HA/DR capabilities for its data centers. Download our success story to get more insights.
Highlighting Cybersecurity Measures for Business Continuity
We live in an era where most of our information is available on the virtual platform. Businesses often deal with large amounts of data making them vulnerable to cyber threats that are a paramount reason for interrupted business operations. So, let’s delve into key strategies that ensure your business remains resilient in the face of potential cyberattacks.
The figure 2 talks about four key elements that are essential to form foundation of a business continuity plan.
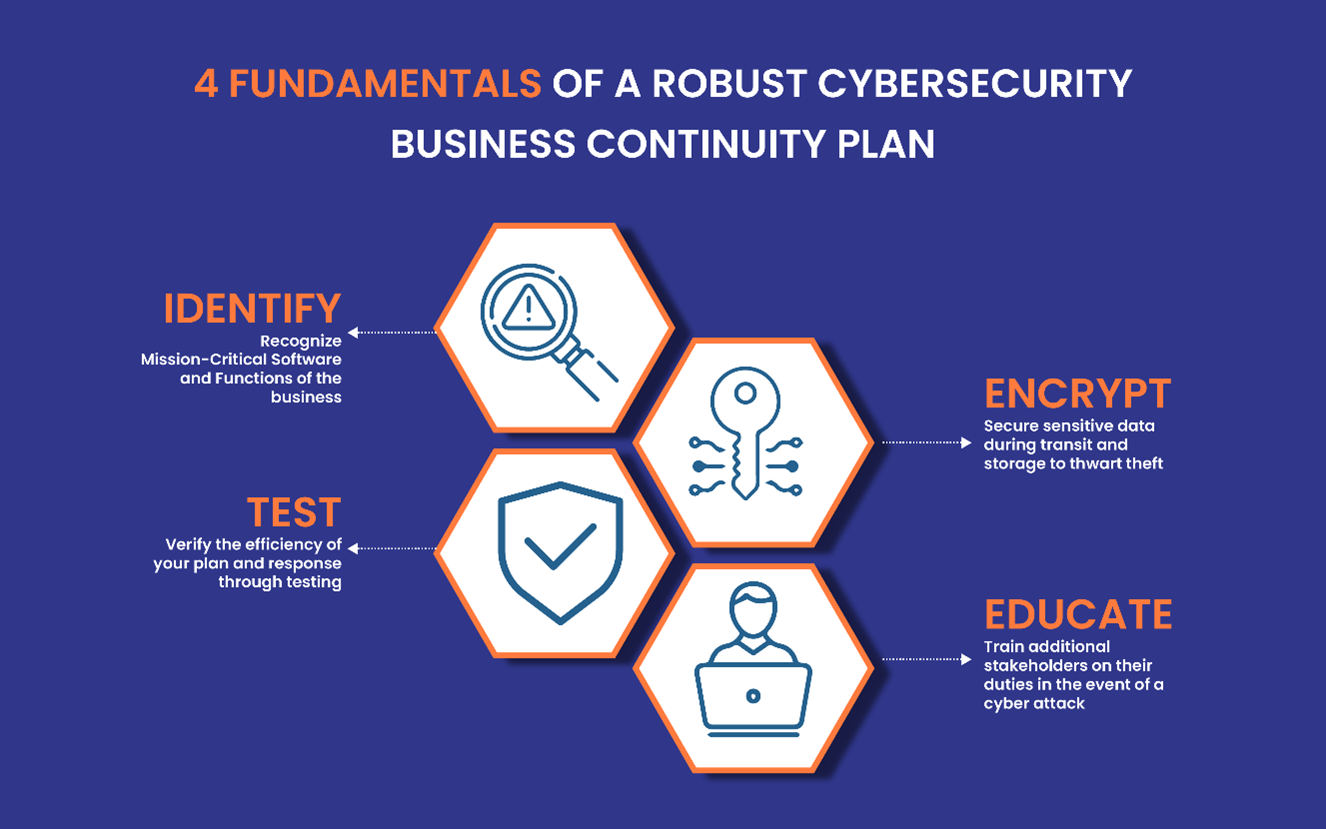
Risk Assessment and Management
Regular risk assessments are one of the strongest pillars extremely inevitable to building a robust cybersecurity framework. By detecting vulnerabilities and potential threats, businesses can implement risk management strategies without wasting any time. These strategies cover a variety of measures, right from software patching and system updates to employee training on cybersecurity best practices. It is equally important to understand that mitigating risks not only protect sensitive data but potentially fortifies a business against financial losses and reputational damage.
Data Backup and Recovery
The importance of regular data backups is not unknown. Everybody does it, even on an individual level. Be it taking backup on the cloud or an external hard disc. Therefore, the importance of regular backups for corporates that deal with huge amounts of data cannot be denied. In case of an event of data loss or corruption, having up-to-date backups ensures swift recovery and minimizes downtime. To not let such an event create complete chaos, businesses must prescribe comprehensive backup protocols, including offsite storage and cloud-based solutions. Pairing data backups with robust recovery strategies is likely to enhance data availability and add a protective layer against data breaches or ransomware attacks.
Network Security
Network security is an extremely essential component when it comes to safeguarding client data and sensitive information, ensuring the security of shared data, reliable access, and keeping up the network performance. Measures like network access control (NAC), firewalls, intrusion detection systems, and encryption protocols can be deployed to bolster the defense of your network infrastructure. Securing networks not only prevents cyber intrusions but also promotes trust among clients and partners, strengthening the reputation quotient.
Incident Response and Contingency Planning
Having a strong foundation of incident response protocols is essential for smooth and decisive action in the face of a cybersecurity breach. Businesses must lay a set of clear escalation procedures, assign response teams, and perform regular exercises to ensure readiness. Contingency planning goes hand in hand with incident response by outlining alternative processes and resources to sustain business operations during disruptions. By staying vigilant and prepared, businesses can navigate cyber threats with resilience and confidence.
Parting Thoughts
Modern technology is lucrative, comes forth with a plethora of opportunities, and works incessantly toward adding ease to human lives. But whilst modern technology presents conveniences and benefits, some people pose a threat to businesses through malicious activities, resulting in stalled business operations, data loss, reputational losses, and a lot more.
In the past big names in the corporate world such as Adobe, Yahoo, NASA, and several others have also fallen prey to cyber-attacks. To not let this happen to your business, it is essential to actively combine cybersecurity with business continuity planning.
Calsoft dedicatedly has been working toward saving businesses from the fate of cyber-attacks by delivering services like, risk assessment, identity/access management, email security & phishing training to business continuity. Our AI/ML-based cyber security solutions help ensure data security. We are adept at running simulations through security policies and technology infrastructure to identify vulnerabilities and secure the entire ecosystem.






