RBAC is a way to provide an access to the logged in user in vCenter server. The administrator user can create roles and assign privileges to the user for role based access control.
In vCenter plugin, we can manage RBAC by creating specific privileges, like read only snapshot dashboard, Limited access to Datastore operations.
Here, In this case, we need to create privileges on vCenter server and assign these to some role. After this, we can create a user and add it to the role which we have created to manage the VCP.
We can add tag inside the plugin.xml. Using this tag, we can add particular permissions to vCenter entities like Datastore, Hostsystem, VM etc. Once tag is added in plugin.xml file and user has this privilege then he can perform the operation on vCenter entity.
There can be multiple privileges per entity. This privilege will be very specific to vCenter plugin.
In this scenario, we have to deal with only vCenter server user. Storage user will not come into the picture.
There is one more way to manage RBAC, using directory services (AD, LDAP). In this scenarios. AD server has to be bind with vCetner SSO (Single Sign On) and Storage.
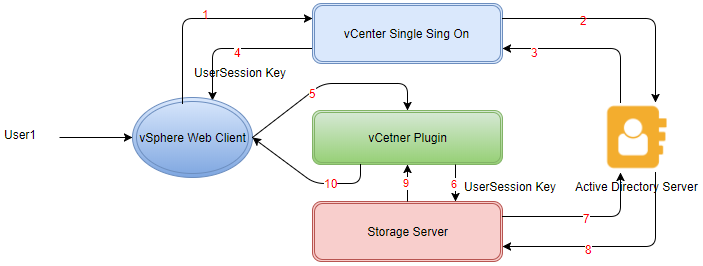
Let’s go through the diagram mentioned below,
In diagram, please follow the numbers
Here User1 is logged in vsphere web client which will be passed to SSO and then to the AD server for authentication. Once the user is authenticated, we can land up to VCP dashboard from which we can perform operations on the Storage server. While executing REST APIs of Storage, we have to get the user session key from vsphere web client and pass it to REST API through authorization header. Storage server will validate the user against AD server and then execute the REST API.
Here we need to configure our storage and SSO with the AD server. Unless there is not a connection between the AD and Storage server we will not be able to authenticate the user which is logged in vsphere web client.