With the cloud, individuals and small businesses can make advanced services easily accessible. You can quickly set up these services without needing expensive hardware. It’s like having powerful IT tools available instantly, no matter your business size.
Virtualization networks play a crucial role in this. They allow you to run multiple virtual networks on the same physical infrastructure, giving you flexibility and control. You can scale your services and optimize resources without buying more hardware.
Understanding the virtualization network is vital. It helps you better manage your cloud environment, saving costs, improving scalability, and enhancing performance.
This article will examine Virtualization networks and their benefits, challenges, and best practices. So, let’s get started!
What is a Virtualization Network in Cloud Computing?
Virtualization networks let you separate network resources from physical hardware. The software allows you to create virtual networks that run independently but share the same physical infrastructure.
This flexibility is crucial in cloud computing. You can quickly create, modify, and manage networks, adjusting resources as needed without requiring additional hardware.
Over time, the Virtualization network has evolved. Initially, networking depended on physical devices, which made it rigid and challenging to manage. As cloud computing grew, flexible solutions became necessary. Technologies like NFV (Network Functions Virtualization) and SDN (Software-Defined Networking) emerged to meet this need.
Here’s the difference between NFV and SDN:
| Feature | NFV (Network Functions Virtualization) | SDN (Software-Defined Networking) |
| Purpose | Virtualizes network functions like routing, firewalls, and load balancing | Centralizes network control and traffic management |
| Function | Runs network functions as software on standard hardware | Separates network control plane from data plane |
| Hardware Dependency | Reduces the need for specialized hardware | Reduces reliance on traditional network hardware |
| Scalability | Scales-specific network functions as needed | Provides scalable and flexible network management |
| Flexibility | Allows quick deployment of network services | Enables dynamic adjustment of network configurations |
| Implementation Focus | Focuses on virtualizing individual network functions | Focuses on overall network architecture and traffic control |
Also read the blog NFV vs VNF
Next, we’ll look at the different types of network virtualization.
Different Types of Network Virtualization
You can divide virtualization networks into two main types: External and internal network virtualization. Each type serves a different purpose and in distinct scenarios.
External virtualization networks allow you to manage multiple physical networks as a single virtual network or divide a physical network into several virtual ones. It’s ideal for large environments where network management needs to be simplified.
Internal Virtualization network occurs within a single host. It simulates a network environment using virtual machines or containers, optimizing the performance within that single physical server.
Here are the differences between the two types of virtualization networks:
| Feature | External Network Virtualization | Internal Network Virtualization |
| Scope | Combines or segments multiple physical networks | Operates within a single server or host |
| Purpose | Simplifies management of large network environments | Optimizes performance and resource use within a single host |
| Example Use | Virtual LANs (VLANs) in large data centers | VMs communicating within a single physical server |
| Management Focus | Centralized management of multiple networks | Internal efficiency and workload isolation |
| Complexity | Higher, involves multiple physical networks | Lower, confined to one server |
Next, we’ll discuss how Virtualization networks work.
How Virtualization Network Works
Virtualization networks allow you to decouple network services from physical hardware. This helps you manage network resources in a flexible, scalable, and efficient way. You create virtual versions of network components, like switches and routers, and integrate them into a software-controlled abstraction layer.
Next, we’ll explore the core components that enable network virtualization.
Core Components of Network Virtualization
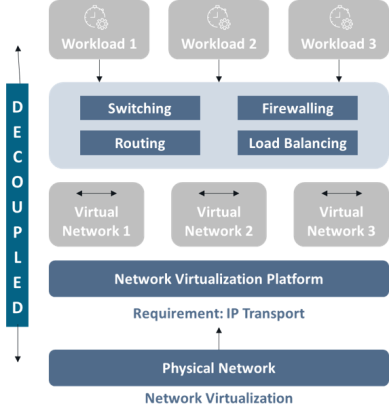
Some of the characteristics of virtualization networks are a combination of core components that work together in creating, managing, and optimizing virtual networks. The NFV architecture is shown in the image below.
Here’s a dissection of these components:
- Network Hypervisor: This is the basis for abstracting the physical hardware from the virtual network. Resources can also manage every virtual network.
- Virtual Switches and Routers: Virtual switches and routers manage the flow between VMs, allowing them to communicate with each other and other networks. Because they base on software, virtual switches are very similar to physical ones.
- Host Protocols: Host protocols of the type VXLAN (Virtual Extensible LAN) encapsulate network traffic and provide the illusion that the VMs on physically separated hosts are on the same network. With VXLAN, can effectively support many isolated virtual networks.
- Controller Software: It is the core to producing the behavior of the virtualized network. It manages the configurations, policies, and general operation of the virtualized network components. The controller ensures the virtual networks’ behavior and adjusts the system to optimize performance and security.
- Management Tools: They allow interfaces for monitoring, configuring, and overseeing your virtual networks. Dashboards, embedded with analytics and sometimes automation fundamentals, give you control over the virtual environment. They are necessary to guarantee your virtual networks run effectively and deliver to expected performance baselines.
Let’s look at how these components work together.
Abstraction Layer and Network Hypervisor
The network hypervisor is the core of network virtualization. It creates an abstraction layer that separates the physical network infrastructure from the virtual networks. This layer allows you to run multiple virtual networks on the same physical hardware without interference.
The hypervisor controls allocating resources such as CPU, memory, and storage to each virtual network, ensuring optimal performance and isolation.
Resource Control and Bandwidth Management
Effective resource control is vital in network virtualization. The hypervisor manages how resources like bandwidth are distributed among virtual networks. This guarantees that each virtual network has the resources to function efficiently without straining the physical infrastructure.
Furthermore, the bandwidth management tools within the hypervisor allow you to prioritize traffic, allocate bandwidth dynamically, and monitor usage to prevent bottlenecks.
Let’s say you’re running multiple applications on different virtual networks. The hypervisor ensures that each application gets the required bandwidth, helping to prevent any one application from dominating the network resources.
Security and Isolation in Virtual Networks
Security is a significant concern in virtualized environments. Virtualization networks enhance security by isolating virtual networks from each other. This isolation ensures that the others remain secure if one network is compromised.
Furthermore, micro-segmentation allows you to create smaller, isolated segments within a virtual network, each with its security policies. This approach minimizes the attack surface and enhances overall network security.
List of Security Measures:
- Micro segmentation
- Virtual firewalls
- Intrusion detection systems (IDS)
- Network access control (NAC)
Communication within Virtual Networks
Virtual switches and routers handle communication between virtual networks. These virtual components direct data traffic within and between virtual networks.
Encapsulation protocols like VXLAN (Virtual Extensible LAN) allow virtual machines (VMs) on different physical hosts to communicate as if they were on the same network. This capability is essential for large-scale cloud environments.
With a solid understanding of how Virtualization networks work, we can now explore the key challenges involved in virtualization.
Challenges of Network Virtualization
While virtualization networks have many benefits, they also present many challenges to network management. If appropriately addressed, these may ensure the network’s performance, security, and efficiency. Let’s look at some of the challenges:
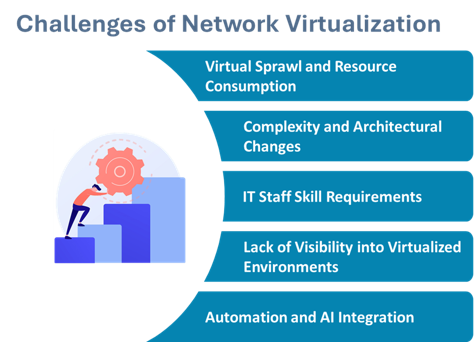
- Virtual Sprawl and Resource Consumption: Virtual sprawl occurs when too many virtual machines or networks are created without proper controls. This leads to extra resource consumption, high costs, and difficulty in management. Stringent governance and monitoring can prevent virtual sprawl.
- Complexity and Architectural Changes: Virtualization networks add more complexity to your IT infrastructure. Handling virtual networks requires new skills and tools and may require significant changes in your network architecture. This extra layer of complexity makes troubleshooting and maintenance more challenging.
- IT Staff Skill Requirements: Your IT staff must be knowledgeable about virtualization technologies. This typically entails additional training and sometimes recruiting specialized personnel, which is time-consuming and expensive. Ensuring that your staff has the latest virtualization skills is very important.
- Lack of Visibility into Virtualized Environments: Traditional network monitoring tools can only provide so much visibility into a virtualized environment. Now, monitoring and managing network performance over several virtual networks becomes a question, increasing the identification and resolution of problems.
- Automation and AI Integration: Integrating automation and AI into your virtualized network can be tricky. While these technologies can bring dramatic efficiency improvements, they also come with problems regarding compatibility and managing the increased computational requirements.
Grasping these challenges allows better preparation for the complexities of network virtualization. The next topic of discussion will be the best practices for implementing a virtualization network that can mitigate these issues and get the best efficiency from your network.
Best Practices for Virtualization Network Implementation
Implementing a Virtualization network requires a systematic approach emphasizing planning, integration, and continuous monitoring. These best practices ensure your network is efficient, scalable, and secure, laying a solid foundation for your cloud infrastructure.
Planning and Assessment
Thorough planning is the first step in a successful Virtualization network project. You must assess your current infrastructure, identify needed resources, and define clear goals. This preparation helps you anticipate challenges and align your strategy with your business objectives.
- Resource Evaluation: Understand your current hardware and software capabilities.
- Define Goals: Set clear, measurable objectives for your virtualization efforts.
- Risk Mitigation: Develop strategies to address potential challenges.
Integration with Existing Systems
Integrating a Virtualization network into your infrastructure can be complex. You must ensure that the new virtual networks are compatible with your legacy systems and that the integration process is smooth and minimally disruptive.
- Check Compatibility: Verify that your current systems can support the new virtualization technology.
- Phased Integration: Implement virtualization in stages to test and refine each step.
- Legacy System Considerations: Upgrade or replace outdated components as necessary.
Monitoring and Optimization
Continuous and regular optimization is critical to maintaining network performance. Use advanced tools to track network health, detect issues early, and adjust configurations to ensure efficient resource use.
- Advanced Monitoring Tools: Deploy tools that provide real-time insights into network performance.
- Regular Adjustments: Periodically review and optimize network configurations.
- Security Vigilance: Monitor for potential security threats and respond swiftly.
By following these best practices, you ensure a successful Virtualization network implementation. This approach supports immediate performance and security needs and prepares your network for future growth and challenges.
Importance and Use Cases of Virtualization Network in Cloud Computing
Virtualization networks are vital for optimizing cloud environments. These benefits make it indispensable for managing modern cloud infrastructures.
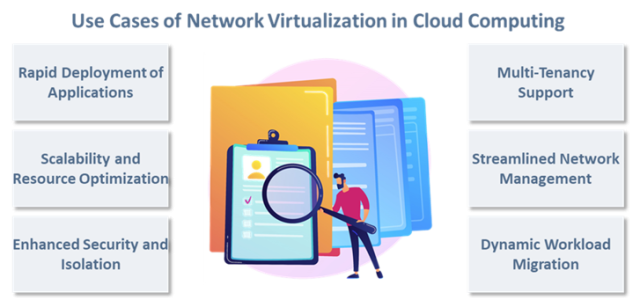
- Multi-tenancy becomes achievable, as you can isolate resources for different clients on the same physical infrastructure.
- Dynamic workload movement is supported, allowing network resources to follow applications across the cloud.
- Facilitating disaster recovery becomes more straightforward, with the ability to replicate and restore network configurations quickly.
- Operational efficiency improves significantly by automating routine network management tasks, reducing manual effort.
- Thanks to automation, network provisioning time is drastically reduced from weeks to minutes.
- Application performance is enhanced through optimized network traffic, which also helps reduce latency.
- Troubleshooting is simplified, as centralized monitoring and diagnostic tools provide a clearer view of network issues.
- Seamless integration with existing IT infrastructure is enabled without significant changes, preserving your investment.
- Hybrid cloud environments are better supported, ensuring consistent network management across both on-premises and cloud settings.
- Energy consumption decreases as the Virtualization network optimizes physical hardware, leading to more sustainable operations.
Network virtualization transforms cloud operations by facilitating rapid instantiation and configuration of virtual networks, reducing deployment times from weeks to minutes. It efficiently scales resources by sharing physical infrastructure among multiple virtual machines, meeting demand without manual intervention. By creating isolated virtual networks, it enhances security, safeguarding sensitive data. Network virtualization also simplifies management through centralized management tools and supports multi-tenancy by securely separating client environments on the same infrastructure. It ensures seamless workload mobility, with network services and security policies automatically adapting as workloads move across hosts. Additionally, it strengthens disaster recovery by enabling quick replication and recovery of virtual networks and policies, ensuring the resilience of cloud-based applications and data.
Conclusion
Picture a robust, flexible, scalable, and secure network while using resources efficiently and reducing costs. That’s the potential of network virtualization, a technology that has revolutionized modern IT systems. Network Virtualization allows to scale quickly, centralize control, optimize resources, and improve security.
With over 25 years of experience, Calsoft provides network virtualization services that improve performance and scalability. Calsoft helps global ISVs to develop and build a product across a range of virtual environments and assists in end-to-end management of virtualized resources.