As the name indicates, a blockchain is a chain of blocks that contain information.
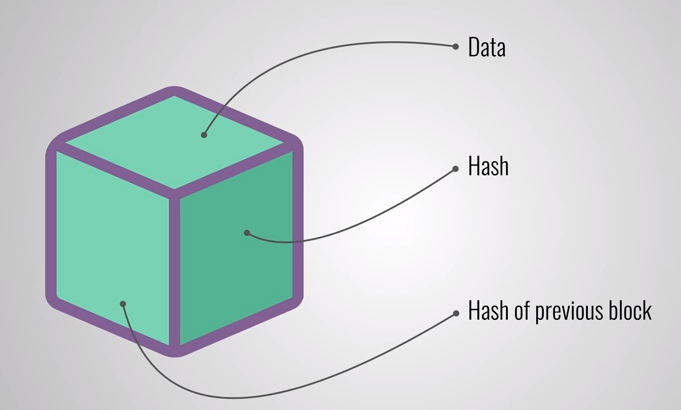
The blockchain is a distributed ledger that is completely open to anyone. They have an interesting property: once some data is written in the blockchain it becomes very difficult to change it. So how does that work? Well, let us take a closer look at a block. Each block contains some data, the hash of the block and the hash of the previous block.
Picture Source: https://youtu.be/SSo_EIwHSd4
Is it secure? : Yes. How does blockchain achieve this? It uses hash, hash of the previous block, proof of work and a decentralized system. Let us see the how.
Hash: A block has hash and hash of the previous block in the chain. Whenever a new block is created, its hash is calculated and stored in the block. If there is any change in the block, the hash will change too, so the block will be different than the original.
Picture Source: https://youtu.be/SSo_EIwHSd4
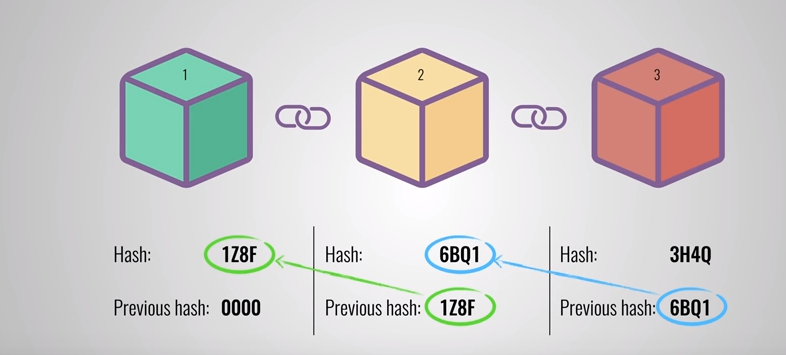
Hash of previous block: It also has a hash of a previous block. The first block is a special one called Genesis block. So if anyone tries to change any of the block in between, it is going to change the hash and thus hash in all the following blocks(as the hash of the previous block changes) is going to be invalid.
E.g. In the above diagram, if I change the 2nd block, its hash will change, which in turn will cause the “hash of the previous block” to change for 3rd and so on.
Proof of work: So say, hacker calculated hash and hash of the previous block also, now can he submit his new block? No, this is prevented using a mechanism called Proof of Work. It basically slows down the creation of any block. A complex problem is normally given to solve which takes some time to solve and then the block is added. In bitcoins case, it takes about 10 minutes to calculate the required proof of work and add a new block to the chain. So if anyone wants to hack and add their own block, they will have to solve the problem for each block and then add the block, which will make the process almost impossible.
Distributed storage: One more thing makes blockchain more secure is distributed storage. This is a peer-to-peer network and everyone is allowed to join. Whoever joins this network gets a full copy of the blockchain. These are called nodes. The nodes can check their copy to verify that everything is still in order. When anyone wants to create a new block, it is sent to everyone in the network, when each node verifies that the block is genuine and not tampered, they reach a consensus, then it is added to the blockchain. Distributed storage also makes the system decentralized by removing the bottleneck of a centralized system having all the control.
Types of blockchains
3 Types of blockchain networks exist 1. Public 2. Private 3. Consortium blockchains.
Public blockchains
A public blockchain has absolutely no access restrictions. Anyone with an internet connection can send transactions to it as well as validate the transactions by creating consensus. These type of blockchains offer incentives to people who secure the transactions. Bitcoin and Ethereum are the popular examples of this type.
Private blockchains
A private blockchain is permissioned. A user needs an invitation from the network administrators to join this network. Participant and validator access is restricted. Use of such blockchain can be in companies who want to use the technology but don’t want it on public networks e.g. in accounting and record-keeping.
Consortium blockchains
This type of blockchain is said to be semi-decentralized. This is also permissioned like private but instead of the single organization controlling it, multiple companies might work as a node on such a network. Only limited trusted nodes are allowed to execute the consensus which is decided by administrators of the consortium blockchain.
[Tweet “Getting Started with Blockchain Technology ~ via @CalsoftInc”]
Want help in implementing blockchain technology for your business?