Do you think your data is secure, where no one can get in without permission? What if your security was more like leaving doors open, where anyone could walk in and cause harm?
Many businesses are operating with these issues. They need to keep their development secure while moving fast. In fact, as per IBM Threat Intelligence Report, there has been a 71% year-over-year increase in cyberattacks that used stolen or compromised credentials, highlighting the challenge’s severity.
When you try to add security to fast-paced development, challenges in DevOps and security are common. Getting this right boost security smooths out your entire process. Therefore, you must understand these challenges and apply the best practices to overcome them.
Best practices in DevOps and security guarantee solid security at every step. This approach protects your software and keeps your process strong. Your key is using these best practices to solve your challenges.
So, let’s get started and aim to strengthen IT infrastructure.
What is DevSecOps Security?
DevSecOps is all about integrating security into every stage of the DevOps process. DevOps and security must be a part of every decision, every line of code, and every deployment. DevSecOps mergers automated IT technologies with project management workflows.
Traditionally, security might have been something that were considered at the end, almost like an afterthought. However, that approach becomes vulnerable to threats and attacks.
With DevOps cyber security, security becomes your primary responsibility. Every developer start thinking about security from the start. Here are some additional benefits of implementing DevSecOps security.
- You can catch and fix exposures before they reach production using security protocols.
- When DevOps and security are built-in, you don’t have to do lengthy security reviews at the end. This means your software gets to market faster.
- You react to threats immediately and continuously monitor and improve your security.
- Fixing issues early on is far less expensive than dealing with them after your software is live.
- With shared responsibility for security, teams are more likely to collaborate closely.
Without DevOps cyber security, you fix problems after they’ve already caused damage. This reactive approach leaves your software and your business vulnerable.
DevOps and security are an ongoing process where you always look for methods to enhance and stay ahead of threats.
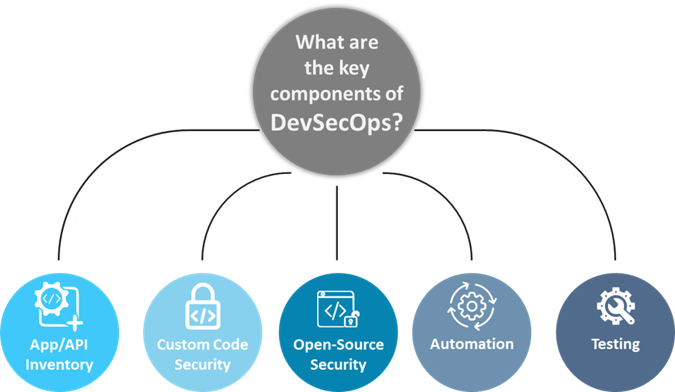
Effective DevSecOps combines automation, custom code security, and open-source security into the development process. Automating the discovery, profiling, and continuous monitoring of Application Programming Interface (APIs) and code across all layers—network, host, application, container, and API—ensures comprehensive coverage. Testing is performed at every development stage, with advanced techniques like penetration testing and Threat Modeling, ensuring secure software without impeding innovation.
That said, implementing DevSecOps isn’t without its challenges. But with exemplary commitment, you can overcome these challenges. With it, you can create a more secure, efficient development process. So, let’s look at the various challenges that you can face.
Challenges in DevSecOps Security
When you implement DevSecOps, several challenges can threaten the security of your development process. Let’s review some of the most significant ones you must address.
1. Targeting of Privileged Credentials by Cyber Attackers
Privileged credentials function like keys to access the most sensitive areas of your system. These credentials grant access to critical infrastructure and data. This makes them highly attractive to cyber attackers. If attackers gain access to these credentials, they can:
- Move through your system undetected.
- Access and steal sensitive information.
- Deploy malware or cause significant damage.
Hence, securing these credentials is crucial. You need to limit access to only those who absolutely need it and continuously monitor that access. Additionally, you should also implement multi-factor authentication and regularly rotate credentials.
2. Developer Focus on Speed Over Security
In many cases, you may face pressure to deliver new features quickly. When you put more focus on speed, it can lead to security lapses. When speed takes precedence over security, you might:
- Skip critical security reviews.
- Fail to test for potential security issues thoroughly.
This approach leaves your software exposed to attacks. To prevent this, you must integrate security into every step of the development process. Once you address these security concerns early, you can focus on delivering the software quickly.
3. Tool-Centric Security Gaps
If you rely too heavily on automated tools for DevOps and security management, it can create gaps in your security. While you can use tools to identify potential security issues, they can:
- Generate false positives.
- Miss vulnerabilities that require a deeper understanding of the system’s context.
You can complement tools with solid security practices and human oversight to address this. Furthermore, you should regularly review the results you get from your tools. This will help you catch what the tools might miss.
4. Managing Security Policies and Governance
Managing DevOps, security policies, and governance across different teams is complex. As your organization grows, tracking who has access to what gets tricky. Therefore, ensuring everyone follows the correct security protocols is impossible.
Inconsistent policies and governance can lead to lapses in security. To maintain robust security governance across DevOps practices:
- Establish clear, enforceable guidelines.
- Conduct regular audits to ensure compliance.
- Implement automated enforcement where possible.
- Provide ongoing training to keep your teams up to date.
Addressing these challenges will help you reduce the risk of security breaches. To do that, you must ensure that your DevSecOps practices are robust and reliable. So, now, let’s look at some of the best practices in DevSecOps security.
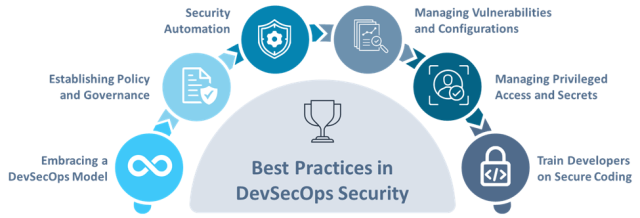
Best Practices in DevSecOps Security
When you’re integrating best practices into your DevSecOps approach, it’s vital to ensure your process is secure, efficient, and resilient. Let’s break down some critical practices you need to embrace.
Embracing a DevSecOps Model
To thoroughly embed DevOps and security into your development process, you must adopt DevSecOps principles from the start. This means security should be your priority task, and you should focus on integrating it into every stage of the software development lifecycle.
When you embrace DevSecOps, you make security a shared responsibility across all teams. To adopt a DevSecOps model, you need to follow these key steps:
- You should integrate DevOps and security checks from the beginning of your development process.
- Make sure your development, operations, and security teams are collaborating closely.
- Use automated tools to handle security testing and checks throughout your pipeline.
- Continuously monitor your systems for any threats in real time.
- Implement and enforce clear security policies and review them regularly.
- Regularly revamp yourself and your team on the latest security practices and threats.
- You should cultivate a culture where DevOps and security are their priority.
Establishing Policy and Governance
Implementing strong security policies and maintaining governance is essential for guaranteeing your DevSecOps practices are consistent and effective. Security policies provide a framework that guides your team’s actions and decisions, helping to ensure that everyone follows best practices.
Once you establish policies and governance, you will get the following benefits:
- You get everyone on your team to follow the same security practices.
- You and your team know exactly what to do to reduce errors.
- It’s clear who’s responsible for what, making it easier to fix issues.
- Regular updates help you stay ahead of new security threats.
- Policies and governance will better equip you to handle and mitigate security risks.
- It lets you keep in line with industry regulations, protecting your organization’s reputation.
Automating Security Processes
Another best practice for DevOps and security is automating the security process. It is critical to streamline the efficiency of your security processes. You can free up your team to concentrate on more critical initiatives.
Here are some best practices for automating security processes:
- You can automatically check for vulnerabilities during every build.
- Set up constantly scanning your code and deployments to catch security issues early.
- Ensure your software meets standards without manual effort on your part.
- Use automated systems to detect threats in real time, so you’re always on top of potential risks.
- Automatically update software to fix vulnerabilities, keeping your systems secure.
- Automate log collection and set up alerts to quickly identify suspicious activities.
- Use automated feeds to keep you updated on the latest threats.
Also Read: DevSecOps on Product Security
Managing Vulnerabilities and Configurations
Managing vulnerabilities and ensuring secure configurations are critical to a robust DevSecOps strategy. Vulnerabilities can expose your system to attacks, while misconfigurations can create security gaps. Any hacker can easily exploit these vulnerabilities in your system. To manage vulnerabilities and configuration, follow these best practices:
- Conduct regular vulnerability scans to recognize and manage potential security risks before hackers can exploit them.
- Ensure that you set up all systems and applications according to best practices. This includes turning off unnecessary services, enforcing strong access controls, and regularly updating software to fix known vulnerabilities.
Managing Privileged Access and Secrets
Managing access controls and protecting sensitive information is essential for maintaining DevOps and security. You must carefully manage privileged access and secrets, such as passwords and keys. If you fail to manage
If you overlook the importance of managing privileged access and secrets, the consequences can be severe:
- Attackers could gain access to sensitive systems, leading to data breaches.
- Hackers could steal critical data, compromising your business.
- Hackers might exploit weak access controls to take over your systems.
- Failure to protect privileged access can result in non-compliance with regulations, leading to hefty fines.
- Security breaches can severely damage your organization’s prestige, leading to customer and partner loss of confidence.
To avoid the risks of poorly managing privileged access and secrets, follow these best practices:
- Only give access to those who need it. Review permissions often and adjust as necessary.
- Adopt multiple forms of verification practice to access privileged accounts.
- Always store passwords, API keys, and other sensitive information in encrypted formats.
- Change passwords and API keys frequently to minimize the risk of compromise.
- Monitor who accesses privileged accounts and regularly audit these activities to catch suspicious behavior early.
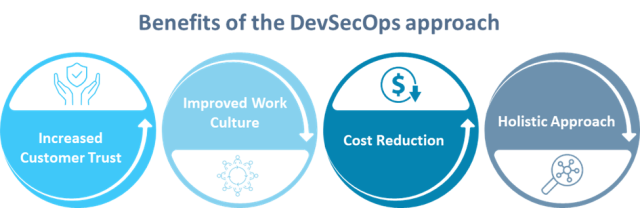
DevSecOps brings in several benefits as shown in the image below:
Implementing DevSecOps offers key advantages, such as building customer trust through reliable security measures that prevent breaches and user loss. Internally, it fosters better communication and teamwork by aligning everyone with the company’s security values. It also reduces costs by catching security issues early in development, which accelerates product delivery. Moreover, DevSecOps ensures a comprehensive security by integrating security throughout the pipeline, securing the entire production environment.
These best practices and benefits can help you build a secure, efficient, resilient DevSecOps process. This will help you reduce risk and increase the effectiveness of your security efforts.
Conclusion
Implementing DevSecOps will evolve the software development and delivery to the next stage of DevOps culture. In DevSecOps, security links the collaborative model shared by operations and development. The implementation of security start at the early stages of development. Developers, infrastructure engineers, and operations are all enabled to take responsibility of security issues. The integration of DevOps and security from the start and setting up of solid policies, includes automating key security steps and effectively managing vulnerabilities. This will protect the software and streamline the workflow.
Calsoft support the customers with DevSecOps implementation to integrate security in their DevOps pipelines. Calsoft facilitates organizations looking to embed security in their DevOps pipeline with best practices and helps them integrate their processes with the right security solutions.