
The Network Effect – Edge Dimension
The worldwide Edge computing market is growing exponentially, and is on track to unlock brand-new avenues of innovation. Do you know how it can help your business grow?

It’s Time for VPs of Engineering to Embed Analytics into their Products
The world is transforming rapidly. Customer needs and market trends are evolving faster than ever. The onus is on organizations to be nimble, pacy, and data-driven. This is impacting the tools and technologies they use too.

How to recognize the product engineer hidden inside yourself
A product engineer is like a Michelin-starred chef. They maintain an extremely high standard of work, using their skills creatively to please their customers. By understanding the market and the tools at their disposal, product engineers create software that leaves an impact. Are you one of them?

How Product Development Approaches Must Evolve as The Company Matures
ISVs need to tailor the approaches based on maturity assessments and business needs. Let’s explore how product development approaches must evolve as the company matures in this article.

Data – The Raw Material for Industry 4.0
Data is crucial for companies to build products & meet customer demands in the age of smart manufacturing. Read this article to learn how companies are utilizing data for better business benefits.
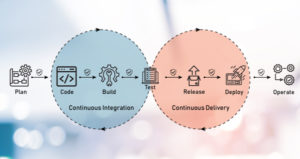
Injecting Security into CICD Pipelines
The CI/CD pipeline was built considering the speed and agility that it provided, but security was never taken into account.
Calsoft – Making Work Fun, and Staying Safe Too
The mandatory remote working has, in fact, served to bring the entire Calsoft family together in more ways than one. Here is a glimpse into our fun meetings:

The Rise of Cognitive QA in the IT Industry
In the future, the delivery cycles will continue to shrink and the pressure on testing will increase. Continuous testing in such times might not be able to keep pace with this.

What You Must Know About Endpoint Protection Challenges
Despite advances in security technologies, the risk organizations face from hackers and insider threats never seems to diminish.

Key Properties of Endpoint Security Solutions
For decades, organizations had considered the antivirus to be the best (and probably the only) solution for securing endpoints. Although antivirus solutions indeed help detect and remove malware, they fall short when it comes to tackling new-age security loopholes.
