Enterprises today in their digital transformation journey operate within a cloud-first framework. The cloud framework becomes inevitable to many business operations, however, brings in many security challenges. The security implementation in cloud workloads is different to securing workloads on-premises. To safeguard the cloud data enterprises should follow certain security strategies. Cloud security strategy involves implementing comprehensive measures to safeguard your data and applications in the cloud from threats and breaches.
In January 2024, the Google Cloud Platform (GCP) market alone offered an impressive 553 security solutions. This implies that there are additional choices available to enhance your cloud security, such as selecting from a variety of security tools.
The conclusions of the CrowdStrike 2024 Global Threat Report underscore the severity of this issue: Intrusions in cloud environments have surged by an alarming 75%, with a 110% year-over-year increase in “cloud-conscious” threat actors.
This blog will help you understand the basics, fundamentals, and difficulties of cloud security, making sure you are ready to safeguard your data.
What is Cloud Computing?
Cloud computing involves delivering computing services like servers, storage, databases, networking, software, analytics, and intelligence over the internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale.
You can access these services from anywhere with an internet connection, providing unprecedented flexibility and mobility. The cloud operates on various service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
As your business grows, the cloud can seamlessly support increased workloads without the need for substantial capital investment in physical infrastructure.
Now understanding what the cloud lays the foundation, but to fully harness its potential, it’s essential to get into the different types of cloud environments available.
Types of Cloud Environments
Selecting the appropriate cloud environment is essential for your company if you are seeking to streamline operations, improve security, and control costs in the rapidly changing digital world.
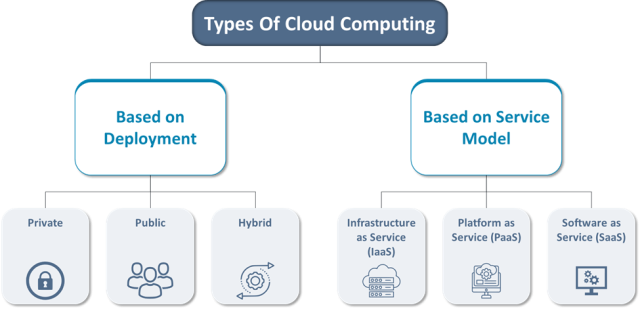
An essential part of this decision involves integrating a strong cloud security plan. Let’s examine the main categories of cloud environments before you hop onto cloud security strategy services.
The details are tabulated below.
| Types of Cloud Environment | Description | Benefits |
| Public Cloud |
|
|
| Private Cloud |
|
|
| Hybrid Cloud |
|
|
| Multi-Cloud |
|
|
With an understanding of the different cloud environments, move on to the key elements of a solid cloud security strategy. Also read the blog Private to Public Cloud Migration.
Understanding Cloud Security
A cloud security strategy protects the data. It resembles a cloud-based, advanced, secure vault built to safeguard your important data against cyber attackers and other online troublemakers.
Simply put, cloud security strategy refers to the measures and practices used to protect your data and applications stored in the cloud from various risks, such as unauthorized access, data breaches, and other security threats.
It involves ensuring that your customer’s information is secure, private, and protected from loss or theft throughout its online storage and processing.
Wondering what the benefits of a cloud security strategy are? Dive in.
Why are Cloud Security Strategies Crucial for Businesses?
Consider a cloud security strategy as the equivalent of the airbags installed in your vehicle. You may not always consider them, but they are necessary. Cloud security is crucial for businesses due to several key factors listed below. Read on!
- Regulatory Compliance: Utilizing cloud security ensures compliance, preventing penalties and legal issues. Making sure your cloud configuration adheres to regulations can prevent you from being included in that data point.
- Business Continuity: Imagine your store shut down for multiple days due to a break-in. This is how a cyberattack can affect your business. Cloud security helps ensure that operations run smoothly. Having a strong cloud security strategy is crucial to avoid expensive disruptions, as the average price of a data breach is $4.45 million as per Statista report.
- Customer Trust: Just as you wouldn’t trust a bank without a vault, customers won’t trust a company that can’t protect their data. Strong cloud security builds confidence. People are at ease when they adapt to the trust placed in them by the companies. This leads to more sales. This trust is very helpful in the management and expansion of your customer base.
- Competitive Advantage: In a world where data breaches grab attention, being able to declare “our security is excellent” can differentiate you from rivals.
According to Statista report, by 2031, the estimated value of the worldwide cloud security market is expected to hit $147.45 billion. Maintaining a lead in cloud security not only protects your customers’ data but also enhances your position in the market.
Now that you have a solid understanding of cloud security strategy, get into the various types of cloud environments.
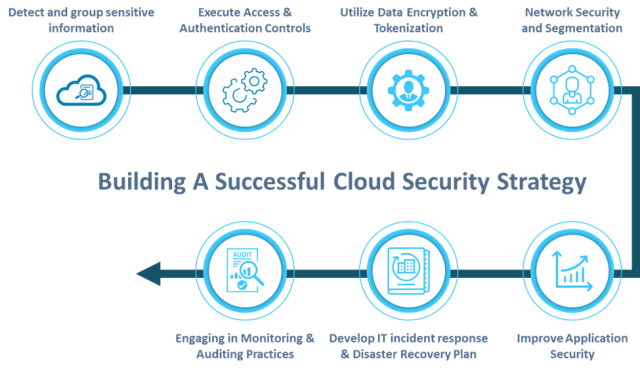
7 Steps to Building a Successful Cloud Security Strategy
To avoid events such as unauthorized access and data breaches, there is a need for a good plan for cloud security, which also comes with a defined strategy. However, the question that begs for attention is: where do you start?
This section will highlight seven ways in which one can develop a suitable cloud security strategy. Each of these steps will help to reinforce your defense, ensure you are compliant with cybersecurity rules and regulations, and protect you against new cyber threats that may arise over time.
Step 1: Detect and Group Information that is Sensitive
In the beginning, you need to find out your most important information, such as financial record information, personal data, and intellectual property. To apply appropriate security controls, classify this information according to its sensitivity and risk level.
Step 2: Execute Access and Authentication Controls
Create strong access and authentication controls that allow only authorized users to get to your cloud data and applications. These can be done through several steps, such as user rights, the use of passwords that are not easily hackable, Multi-Factor Identification (MFI), and role-based access control.
Step 3: Utilize Data Encryption and Tokenization
Safeguard your cloud information by encrypting it so that nobody can understand and tokenize it to replace sensitive data with nonsensitive tokens. These two techniques help in securing your data such that unauthorized persons cannot easily access it.
Step 4: Network Security and Segmentation
Secure your network infrastructure and enable segmentation at least on the level of securing servers from each other. Network segmentation ensures that if a breach does occur, it is contained within the isolated segments and doesn’t spread throughout the network.
Role-based and application type-based segmentation, for instance, can restrict traffic flow between workloads.
Step 5: Improve Applications Security
Protect your cloud apps from threats like SQL (Structured Query Language) injection and cross-site scripting. Adopt a security in depth model across your application lifecycle – authentication, encryption, and continuous vulnerability assessment.
Most importantly, the platform should have vulnerability scanning and penetration testing capability with code reviews to help you identify and eliminate as many potential security risks as possible.
Step 6: Develop an IT Incident Response and Disaster Recovery Plan
Protect yourself from inevitable security incidents and disasters in check by creating a Security Incident Response Team (SIRT) to handle breaches, as well.
Also, generate a Disaster Recovery Plan (DRP) to detail workflows for recovering services and data during downtime such as backing-up testing backups and deploying secondary systems in the case of business continuity affectation.
Step 7: Engaging in Monitoring and Auditing Practices
It is of paramount importance to perpetually engage in the observation of your cloud construct for any emergent threats. This should be done in conjunction with executing systematic audits periodically to ascertain adherence to established security paradigms.
This ongoing surveillance and evaluative process assists in the discernment and rectification of prospective complications prior to their manifestation as detrimental effects on your data integrity or system functionality.
Having covered the seven steps, check out the essential elements of a strong cloud security framework.
Elements of a Cloud Security Strategy
There are seven key elements to consider when crafting a strong cloud security strategy, encompassing both pre-breach and post-breach measures. Have a look at the details!
- Identity and Access Management (IAM): Use IAM systems to manage who can access your data and applications. Cloud providers offer built-in IAM solutions or allow integration with your system.
- Visibility: Maintain visibility into your cloud architecture to prevent exposure to security vulnerabilities. Monitor changes and new workloads to ensure security.
- Encryption: Ensure data is encrypted both in transit and at rest, as cloud providers may not always protect idle data. Use encryption to secure your data from unauthorized access.
- Micro-segmentation: Divide your network into distinct security segments to isolate and protect individual workloads. This limits damage if an attacker gains access.
- Automation: Automate cloud security processes, including IAM policy management and alert handling, to prevent vulnerabilities and focus on critical security events.
- Cloud Security Monitoring: Combine manual and automated processes to track and secure your cloud environment. Use tools like Cloud Security Posture Management (CSPM) to maintain compliance and identify risks.
- Secure Data Transfers: Ensure data in transit is encrypted using secure HTTP (SSL/TLS) to protect against interception and maintain data security.
Having explored the key elements of a cloud security strategy, now check out the foundational principles that underpin effective cloud security.
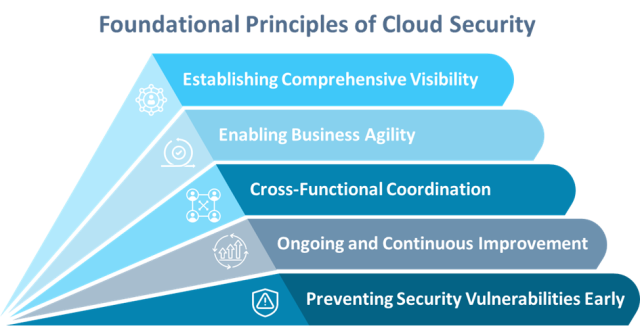
Foundational Principles of Cloud Security
Establishing security in your cloud environment necessitates a solid base founded on essential principles. Here’s a section on how a cloud security strategy can assist you in effectively implementing these basic principles. Have a look.
Establishing Comprehensive Visibility
Start with visibility to understand your cloud environment fully. By mapping data movement and processing, teams gain clear, real-time overviews of cloud assets, configurations, and data flows.
This visibility supports traceability, enabling you to track actions through your systems and observability, providing insights from system outputs.
Enabling Business Agility
Cloud’s flexibility allows rapid responses to market changes, but this requires a security framework that is both strong and adaptable. Your security strategy should integrate seamlessly with your technology, structure, and processes, supporting fast development cycles, maintaining compliance, and encouraging innovation.
This involves embedding security into the development lifecycle, automating where possible, and ensuring protocols adapt to quick service deployments.
Cross-Functional Coordination
A forward-looking security strategy integrates agility in both actions and thinking. It’s crucial to avoid assigning security responsibility solely to security teams. Instead, all stakeholders should share accountability.
Security should be embedded within DevOps and IT workflows, allowing teams to address potential threats during design and development.
Effective security involves balancing rigorous safeguards with the need to avoid disruptions in development cycles. Maintaining healthy inter-team relationships is key to adapting protocols that support rapid innovation.
Ongoing and Continuous Improvement
Embrace a “minimum viable security” approach that evolves through continuous, incremental improvements. Security should be viewed as an ongoing process, with regular evaluations against benchmarks and learning from incidents.
Cultivate a culture of experimentation and learning, using blameless postmortems to uncover root causes and drive improvements.
Preventing Security Vulnerabilities Early
Adopt a ‘shift-left’ strategy to integrate security early in the development lifecycle. Embed security tools and checks throughout the pipeline, from coding to deployment.
Develop a strategy document outlining roles, milestones, and metrics, and manage supply chain risks by scrutinizing open-source components and updating dependencies regularly.
Challenges in Cloud Security
Dealing with cloud security presents its distinct difficulties. Here is a table showing how cloud security strategy services can assist you in addressing them.
| Challenge | Problem | Solution |
| Complexity and Integration |
|
|
| Human Error and Insider Threats |
|
|
| Evolving Threat Landscape |
|
|
| Cost Management |
|
|
After examining the challenges in cloud security, read about the best practices for implementing an effective cloud security strategy.
Best Practices for Implementing a Cloud Security Strategy
In the current era of technology, businesses need to prioritize cloud security for their success. With that, it’s time to explore essential best practices to secure your cloud environment.
- Adopt a Security-First Mindset: Prioritize security in all cloud-related decisions and processes with a cloud security strategy.
- Regular Training and Awareness Programs: Educate your employees on cloud security strategies through phishing simulation exercises and cloud security workshops.
- Utilize Automation and AI: Leverage automation and AI to enhance security measures.
- Collaborate with Security Experts: Partner with experts and consultants to implement the best cloud security strategy services.
- Stay Informed and Updated: Keep up with the latest security trends and updates.
In Summary
Building a successful cloud security strategy involves a balanced approach that integrates strong protection with cloud flexibility. Challenges such as the complexity of multi-cloud environments, dynamic cloud services, and data breaches require cautious risk assessment and automation tools to enhance security without negotiating efficiency. Adhering to core principles such as data encryption, network security, and compliance with industry standards helps maintain resilience against threats. Enterprises can realize a robust cloud security framework by focusing key elements and principles and addressing challenges proactively, enabling innovative business solutions.
Calsoft leverages its 25 years of product engineering expertise and extensive domain experience to transform business operations through innovative cloud solutions. Our cloud security services help enterprises in addressing compliance concerns that delay or minimize the migration of sensitive assets into private, public, and hybrid clouds.