Security testing is not just an option; it’s a necessity in today’s evolving digital landscape. Cyber threats are progressively complex, making it critical for enterprises to implement robust security measures throughout the Software Development Lifecycle (SDLC).
It is more important to follow proactive practice to tackle security threats and achieve effective software security. This involves integrating security considerations from the initial design phase throughout to deployment and maintenance. Software security includes a set of methodologies that are incorporated in software testing. It ensures a reduction in data breaches and greater software protection from potential threats and cyber-attacks. Best practices for software security testing and development are essential for mitigating risks, protecting sensitive data, and maintaining trust of users and stakeholders.
CrowdStrike’s 2024 Global Threat Report emphasizes the increasing speed and stealth of cyberattacks. Do you feel that your software is more exposed? Let’s tighten up that code and keep your programs secure with the best practices!
Organizations need to be very careful when it comes to cybersecurity. This can be achieved by implementing software security practices and strategies. This blog aims to discuss the ways of protecting software, the best practices in security testing for software development, and the use of innovative approaches to improve the security of digital properties. Keep reading to know more.
Importance of Security in Software Development
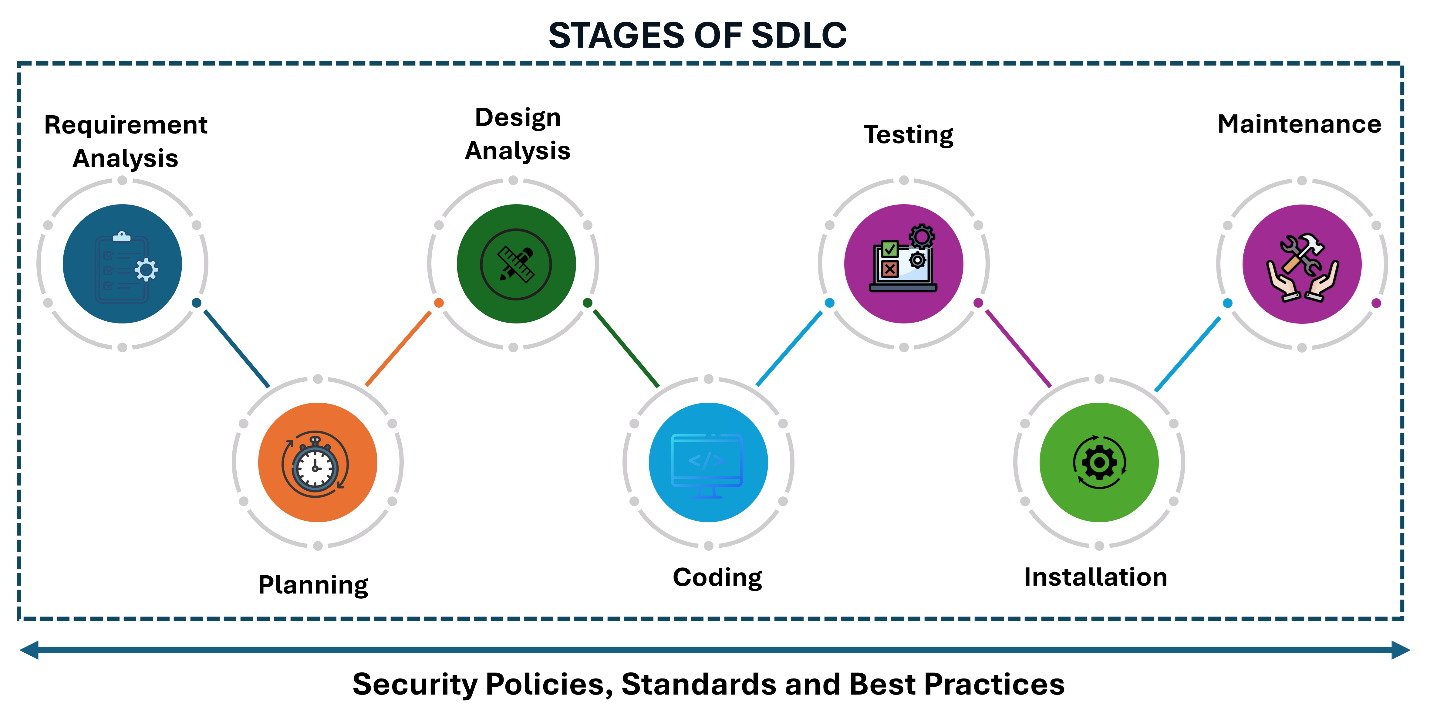
It is not a secret that security has become mandatory in software development, not something that is an add-on or extra. To expand the efficacy of security testing, security testing for software should be integrated into all the 7 stages of the SDLC, beginning from the requirements gathering stage to design, development, testing, deployment, and maintenance as shown in the image below. This confirms that security is not a second thought but an essential facet of the development process. Early detection and addressing helps to mitigate potential vulnerabilities before they become expensive and time-consuming.
Do you Know?
The global average cost of a data breach increased 10% over the previous year, reaching $4.88 million in 2024 (from $4.45 million in 2023), the biggest jump since the pandemic,” said the annual Cost of a Data Breach Report.
The implementation of security solutions and tools at every developmental stage of the software is, therefore, critical for preserving identities and reputative user data. It ensures the stability of companies’ functioning.
Now that you know about the importance of security in software development, let’s understand what the best practices of security testing in software development are.
15 Best Practices in Security Testing for Software Development
Best practices in security testing not only help identify and mitigate potential vulnerabilities but also ensure compliance with industry regulations, safeguard sensitive data, and increase the overall trustworthiness of software applications.
According to a report by Cybersecurity Ventures, global cybercrime costs are projected to reach $10.5 trillion annually by 2025, highlighting the urgent need for robust security practices in software development.
Additionally, a study by the National Cybersecurity Alliance reveals that 60% of small companies go out of business within six months of a cyberattack, highlighting the importance of proactive security measures.
Here are the 15 best practices in security testing for software development.
Now let us explore the best practices in software security testing:
1. Use Multiple Testing Techniques
The complexities involved in application security demonstrate that using different testing techniques gives a wider appreciation of an application’s security situation.
The following multi-faceted approach is more effective in defining a broader variety of weaknesses than other sorts of hypothetical threats. Employ diverse testing methods as follows.
- Black-box testing: Evaluate the application without knowledge of internal workings
- White-box testing: Analyze the application with full access to the source code
- Gray-box testing: Combine elements of both black-box and white-box approaches
Let’s compare these testing approaches.
| Testing Type | Knowledge of Internals | Access to Source Code | Approach |
| Black box | None | No | External perspective, focuses on inputs and outputs |
| White box | Full | Yes | Internal analysis, examines code structure and logic |
| Gray-box | Partial | Limited | Combines external testing with some internal knowledge |
Benefits of Diverse Testing Approaches
The benefits of diverse testing approaches are immense – few being a reduction in time and cost of production and reducing security threats.
- Identify a wider range of vulnerabilities
- Simulate different types of potential attacks
- Provide a more holistic view of the application’s security
2. Conduct Regular Security Testing
Consistent security audits are particularly important in preventing new attacks that have not been seen before. It is recommended that tests should be conducted frequently since this will assist an organization in identifying exploitable loopholes. Some suggestions are listed below.
Perform Continuous Security Assessments
Cybersecurity involves frequent security auditing, which is the pillar of any strong security measure. Similarly, various evaluations can be done, and the organization can prevent new threats prone to emergence.
The organization will be able to fix the threats as quickly as possible. Please keep the following points in mind.
- Implement automated security scans as part of the development pipeline
- Conduct periodic manual security audits
- Respond promptly to newly discovered vulnerabilities
Regular Scanning and Testing Throughout the Development Lifecycle
Incorporating security checks in every phase of the development process will help in the detection and elimination of weaknesses. This systematic approach is very powerful and efficient in delivering cybersecurity. It is integrated into the product at the lowest level.
Security scanning and testing, particularly if carried out during the lifecycle of the systems, will significantly decrease the number of resources required to correct the security flaws.
See to it that you do not forget the points listed below.
- Integrate security checks into daily build processes
- Perform comprehensive security tests before major releases
- Monitor production environments for potential security issues
3. Integrate Testing into the Development Process
Seamlessly incorporating security testing into the development workflow ensures consistent and efficient security practices. This integration can lead to faster issue resolution and improved overall security posture.
Here are the key points you need to consider while integrating testing into the development process.
Integrate Security Testing Within the Development Workflow
Embedding security testing directly into the development process creates a seamless security-first approach.
This integration allows for immediate feedback on potential vulnerabilities, enabling developers to address issues as they code. The result is a more secure product and a more efficient development process. The suggestions are listed below.
- Implement security checks as part of code commit processes
- Automate security testing in continuous integration pipelines
- Provide immediate feedback to developers on security issues
Utilize Continuous Integration and Continuous Testing Tools
Utilizing automated tools for continuous integration and testing streamlines the cybersecurity process.
These tools can consistently apply security checks, freeing developers to focus on writing secure code. By automating repetitive tasks, organizations can achieve more thorough and frequent security testing.
4. Threat Modeling
Threat modeling is a process of threat identification and threat probability assessment. This proactive technique is specifically used to let the teams think like attackers – to look for weaknesses that could be later exploited by cybercriminals.
The list given below states how understanding the threat scenario helps to create more adequate security strategies within the organization.
- A Systematic process for identifying and prioritizing potential threats
- Helps in designing security measures tailored to specific risks
Process: Planning, Identification, Mitigation, and Remediation
Threat modeling is really a systematic methodology of security.
It includes coordination when defining boundaries, methodical search for risks, elaboration of specific measures, and efficient treatment of defined problems. This structured process helps guarantee the absence of any weakness in security protection.
The steps are listed below.
- Planning: Define the scope and objectives of the threat model
- Identification: Identify potential threats and vulnerabilities
- Mitigation: Develop strategies to address identified risks
- Remediation: Implement and validate security measures
Some of the famous threat modeling tools are Microsoft Threat Modeling Tool, OWASP Threat Dragon, and IriusRisk.
Want to enhance your threat modeling process? Discover how Calsoft’s DevSecOps services can help you identify and mitigate potential security threats effectively.
5. Code Reviews and Static Analysis
Code reviews and static analysis help in eliminating major flaws in a code, before integration with another segment of code. Research reveals that between 70% and 90% of security violations stem from attacks targeted at flaws present in a program’s architecture or source code.
Explore all key details below, starting with the basics – the importance of code reviews!
Why Conduct Code Reviews and Static Analysis?
Code reviews and static analysis form a critical line of defense in software security. These practices allow teams to identify potential vulnerabilities and coding errors before they make it into production.
By catching issues early, organizations can significantly reduce the cost and risk associated with security flaws, as given below.
- Detect security flaws before they reach production
- Improve overall code quality and maintainability
- Promote a culture of security awareness among developers
6. Dynamic Application Security Testing (DAST)
DAST (Dynamic Application Security Testing) is a method of testing applications in their running state. It simulates attacks from malicious users to identify security vulnerabilities in web applications.
DAST helps to identify the weak points pertinent to an application’s security because DAST tests are carried out when the application is running. This approach can identify over 50% of security issues that static analysis might miss.
Analyzing the Application’s Runtime Behavior
DAST is minimally invasive and can reveal weaknesses such as SQL injection and cross-site scripting that may not be traced at all through code analysis.
While DAST covers the aspects that static testing cannot address, it also simulates real-life conditions and exposes key runtime vulnerabilities, as listed below.
- Simulate real-world attacks on running applications
- Identify vulnerabilities, such as authentication flaws, that emerge during execution
- Test the application in its deployed environment
Identification of Vulnerabilities During Execution
Runtime analysis is key to detecting certain types of vulnerabilities. By observing the application in action, DAST can identify issues that might evade static analysis. This approach is essential for a thorough security assessment. The issues detected are listed below.
- SQL injection
- Cross-site scripting (XSS)
- Authentication and session management flaws
7. Penetration Testing
Penetration testing is a simulated cyberattack against a computer system to check for exploitable vulnerabilities. It involves attempting to breach application systems, APIs, servers, and other potential points of exposure.
When performing pen testing or a penetration test, a set of tactics is modeled with the intention of gauging injurious flaws in the system. This adaptive approach can reveal very crucial issues that might have been left unnoticed by automatic scanning tools.
Let’s explore the details of pen testing, starting with simulated cyber-attacks.
Simulated Cyber-Attacks to Identify Exploitable Weaknesses
In penetration testing, the approach is to exploit identified weaknesses. Performed by professionals who think like attackers, penetration testing reveals several issues that would otherwise remain unnoticed, as listed below.
- Evaluate the effectiveness of existing security measures
- Identify vulnerabilities that automated tools may miss
- Provide a real-world perspective on potential attack vectors
Types and Stages of Penetration Testing
There are various approaches to penetration testing, each offering unique benefits. From external and internal testing to blind testing, these different methodologies allow a comprehensive evaluation of an application’s security.
Understanding the types listed below helps organizations tailor their testing strategy to their specific needs.
- External testing: Assess externally facing systems
- Internal testing: Evaluate internal network security
- Blind testing: Simulate attacks with minimal prior information
Let’s examine the different penetration testing methods.
| Testing Method | Description | Scope |
| External Testing | Assesses externally facing systems | Focuses on assets visible from outside the organization |
| Internal Testing | Evaluates internal network security | Simulates an attack by a malicious insider or compromised internal system |
| Blind Testing | Simulates attacks with minimal prior information | Tester has little to no information about the target systems |
8. Test Third-Party Components
Third-party libraries and components, such as OpenSSL and jQuery present in your software should be tested extensively to avoid incorporation of vulnerability.
Third-party components can introduce significant vulnerabilities into otherwise secure applications. Rigorous testing of these elements is crucial to maintain overall security.
By thoroughly vetting external dependencies as listed below, organizations can prevent potential backdoors into their systems.
- Conduct security audits of external dependencies
- Monitor for known vulnerabilities in third-party components
- Implement a process for regularly updating external libraries
Mitigation of Vulnerabilities in External Dependencies
Security checks of third-party components must be conducted beforehand and should not be delayed till problems appear.
To control risks related to external dependencies, one should update the system more often, have versions under control, and monitor the system constantly. It is, therefore, important to have proper strategies as listed below to secure these elements.
- Use tools like OWASP Dependency-Check to identify vulnerable components
- Implement version pinning to control dependency updates
- Maintain an inventory of third-party components and their versions
9. Perform Regular Updates and Patching
Keeping the software components updated is important in ensuring the organization’s security is boosted. Most updates contain fixes for fresh threats. Therefore, updates are critical for guarding against new threats.
This reinforces the need for a consistent update strategy to sustain a good security position. To maintain a solid security posture, consider the following points.
- Address known vulnerabilities, such as updating outdated software promptly
- Benefit from the latest security enhancements, such as implementing new encryption algorithms
- Maintain compliance with security standards and regulations
Addressing Newly Discovered Vulnerabilities Through Patches
Quick action on new threats, when they are found, is highly necessary. Patch management is a process of managing all the updates and making sure that all crucial security patches are implemented.
By doing this, an organization can greatly minimize its vulnerability to various possible attacks. To detect the latest patches, consider the following points.
Implement a robust patch management process
- Prioritize critical security updates
- Test patches thoroughly before deployment to production
10. Document and Communicate Findings
Thorough documentation of security testing results is essential for maintaining a comprehensive security strategy.
Detailed reports provide valuable insights for future improvements and serve as a historical record of an application’s security journey. Good documentation practices ensure that no valuable information is lost.
To ensure good documentation of findings, consider the following points.
Create detailed reports of identified vulnerabilities
- Provide clear remediation steps for each issue
- Maintain a historical record of security assessments
Communicate with Stakeholders to Ensure Proper Handling of Identified Issues
Security findings should be communicated properly to stakeholders to mitigate problems effectively. This is crucial in sustaining the organization’s sound security policy at every level.
To ensure proper communication with stakeholders, keep these points in mind.
Share results with relevant teams (development, operations, management)
- Prioritize vulnerabilities based on risk and impact
- Establish clear timelines for addressing security issues
11. Security Testing for APIs
Criticality of API Security
Application programming interfaces are widely used in today’s applications. Hence, it is essential to secure them. API is the primary entry point through which access to the core functionalities and sensitive data is granted. So, API is one of the most favorite targets for attackers.
The negligence of API security can have the following serious ramifications.
- Insecure APIs can lead to data breaches and system compromises.
- API vulnerabilities can impact multiple applications and services.
Focus on Authentication, Authorization, Input Validation, and Output Encoding
The fundamentals of API security involve strict procedures in the areas of authentication and authorization, together with validation of inputs and encoding of outputs. These practices help prevent common attack vectors and protect sensitive data.
A description of the fundamentals of API testing is given below.
| Security Concept | Description |
| Authentication | Verifies the identity of users or systems attempting to access resources. |
| Authorization | Determines what actions or resources an authenticated user or system can access. |
| Input Validation | Ensures that incoming data is properly formatted and safe before processing. |
| Output Encoding | Converts special characters into their display equivalents to prevent injection attacks. |
To ensure proper API Testing, consider the following recommendations.
- Implement strong authentication mechanisms.
- Enforce proper authorization checks for API endpoints.
- Validate and sanitize all input data to prevent injection attacks.
- Encode output to prevent cross-site scripting and other injection vulnerabilities.
12. Automate Security Testing
Documentation is necessary to make sure that all the security tests conducted in the development life cycle are consistent and effective. Automated security testing tools have transformed the scenario of application security.
They can carry out efficient and exhaustive scanning in a short time and, in turn, improve security assessment activities. It ensures strict monitoring so that human resources may be employed in other important tasks in the organization.
The benefits of automated security testing are given below.
- Perform repetitive tests quickly and consistently
- Cover a wide range of potential vulnerabilities
- Integrate seamlessly with development workflows
Integration of Automated Testing in Development Workflows
The continuous enforcement of security processes is achieved by the integration of automated testing into the development of lifecycles. This integration ensures that there are regular checks on securities.
As the development process proceeds, the vulnerability can be easily spotted and dealt with. To ensure proper integration of automated testing in development workflows, consider the following recommendations.
- Implement security checks in continuous integration pipelines
- Use pre-commit hooks to catch security issues before the code is committed
- Automate vulnerability scans as part of the build process
13. Integrate Multiple Tools for Comprehensive Security
Combining different security testing tools provides a more thorough and well-rounded security assessment. This multi-tool approach can increase vulnerability detection rates.
No single tool can provide complete security coverage. When different security testing tools are incorporated, the assessment of the organization’s application undergoes a thorough process.
This uncovers a broad spectrum of risks compared to the one-tool-at-a-time approach that gives a distorted picture of the application’s security.
Please keep the following points in mind to ensure proper integration of multiple tools.
- Use static analysis tools to catch coding errors
- Employ dynamic testing tools to identify runtime vulnerabilities
- Implement vulnerability scanners to detect known security issues
14. Ensure Secure Data Storage and Transmission
Preserving confidentiality is crucial in gaining users’ trust and adhering to data protection laws. Protecting data is the foundation of all methods applied in application security.
Data breaches are now faster, cheaper, and more damaging than before. Thus, it is important that data is stored and transmitted in a secure manner. Adequate protection of data not only preserves users but also keeps the organization out of legal violations.
To ensure secure data storage and transmission, consider the following recommendations.
- Prevent unauthorized access to confidential information
- Maintain compliance with data protection laws, including GDPR and CCPA
- Safeguard user privacy and build trust
Data encryption, the use of secure protocol, and proper data elimination act as the core of data security. The following techniques assist in the security of data that is in storage and the data that is on the move.
- Encryption: Use strong encryption algorithms for data at rest and in transit
- Secure protocols: Implement HTTPS for all data transmissions
- Data sanitization: Properly sanitize user inputs to prevent injection attacks
Calsoft cloud backup offerings ensure that our customers get user-friendly access to all their backed-up data anytime and anywhere; their data is secured using enterprise-grade encryption, and all this at minimal cost & effort.
Enjoy Anytime, Secure Backups on Cloud – our solutions provide flexibility, security, and cost-efficiency. Make the smart choice for your data protection needs.
15. Continuous Monitoring and Improvement
Security is not an event that takes place at a particular time but a process that is continuous because of innovation and new threats. Continuous monitoring allows organizations to stay ahead of emerging threats and adapt their security measures accordingly. The process of monitoring and improving the state of security is one of the most continuous processes because of innovation and new threats.
To ensure continuous monitoring and improvement of system security, consider the following recommendations.
- Implement real-time security monitoring systems
- Regularly review and update security policies and procedures
- Stay informed about emerging threats and vulnerabilities
Continuous Monitoring, Regular Assessments, and Iterative Security Upgrades
Security upgrades let organizations monitor the threat level constantly, staying ahead of newly emerged threats and adjusting their security measures. This is a very proactive approach, one that is crucial for keeping security high in the light of a constantly shifting threat profile.
To ensure iterative security upgrades, kindly consider the following points.
- Use security information and event management (SIEM) tools
- Conduct periodic security audits and penetration tests
- Implement a feedback loop to continuously improve security practices
Comparison of Security Testing Approaches
Understanding the strengths and limitations of various security testing approaches is crucial for developing a comprehensive security strategy. Each method offers unique benefits and is suited to different stages of the development lifecycle or types of vulnerabilities.
The following table provides a concise overview of the main security testing approaches, highlighting their pros, cons, and ideal use cases. This comparison can help organizations select the most appropriate techniques for their specific security needs and resources.
| Approach | Pros | Cons | Best For |
| Static Analysis | ● Early detection
● Low cost |
● False positive
● Limited to source code |
● Finding coding errors
● Enforcing standards |
| Dynamic Analysis | ● Detects runtime issues
● Simulates real attacks |
● Resource-intensive
● May miss some vulnerabilities |
● Identifying complex vulnerabilities
● Testing deployed applications |
| Penetration Testing | ● Comprehensive
● Simulates real-world attacks |
● Time-consuming
● Expensive |
● Assessing overall security posture
● Identifying hard-to-find vulnerabilities |
| Automated Scanning | ● Fast
● Consistent ● Scalable |
May miss complex vulnerabilities | ● Continuous integration
● Regular security checks |
| Manual Code Review | ● In-depth analysis
● Context-aware |
● Time-consuming
● Relies on reviewer expertise |
● Critical systems
● Complex logic review |
Implementation of a Comprehensive Security Testing Strategy
A secure testing principle is the basic principle of software protection. The goal of credible security coverage is achieved when organizations apply a blend of automated and manual testing strategies.
You should keep in mind the following points as best practices in security testing for software development.
- Integrate security testing at every stage, from design to deployment
- Ensure continuous feedback and improvement loops
- Align testing with business objectives and risk tolerance
- Combine automated and manual testing methods. For example, static analysis is used to examine source code without execution; dynamic analysis is used for testing running applications for vulnerabilities, and penetration testing is used to simulate real-world attacks to identify weaknesses
Unsure about how to develop a thorough security testing strategy? Explore how our managed testing services can provide comprehensive, end-to-end testing solutions.
Involve Security Experts Early On
It may cost a lot of money and time to work with the security specialists if one does not involve them from the beginning. Research shows that it is up to 15 times cheaper to fix a security issue in the testing phase than in the deployment phase.
Here are the key points to keep in mind while security testing for software development.
- Consult security experts from the project’s inception
- Identify potential vulnerabilities early in the development process
- Provide guidance on secure coding practices and architecture
- Offer insights into emerging threats and mitigation strategies
Benefits of Deploying Best Practices
Implementing the best practices in security testing for software development offers numerous advantages that extend beyond mere compliance. Here’s why adhering to these practices is crucial.
- Enhanced Security Posture: Identify and mitigate vulnerabilities early, reducing breach risks and building trust.
- Cost Savings: Address security flaws during development to minimize financial impact.
- Regulatory Compliance: Ensure compliance with GDPR, CCPA, and other data protection laws, avoiding fines and legal issues.
- Improved Product Quality: Enhance software robustness and performance by resolving security and code issues.
- Faster Time-to-Market: Streamline workflows and reduce time spent fixing vulnerabilities, allowing quicker releases.
- Increased Customer Confidence: Boost customer trust by demonstrating a commitment to data security.
- Adaptability to Emerging Threats: Continuously monitor and update security measures to respond swiftly to new vulnerabilities.
Wrapping Up
Software protection is a difficult and continuous process that demands sincerity, professional competency, and strategy. Thus, by employing the best practices mentioned in this blog, organizations can advance their security level and safeguard their important assets. It must be noted that cybersecurity threats are dynamic. Therefore, the security measures in organizations must also be agile. Be aware, be wise, and always be safe while developing your software.
Looking for a platform that adheres to best practices in testing solutions? Look no further than Calsoft! With a focus on accelerating our customers’ digital transformation journey, we provide timely quality checks for products to ensure an efficient adoption process. Calsoft is a leading technology-first partner with over 25 years of experience, offering digital and product engineering services.
Don’t leave your business exposed to the downpour of cyber threats. For a strong security shield that keeps your software safe and sound, contact us. We’re your reliable partner in safeguarding against digital deluge!
