Enterprises across the world are harnessing cloud capabilities to achieve elasticity, flexibility, scalability, innovation, automation and much more. Though cloud brings innovative opportunities to modernize businesses, transform and innovate, security risks remain the most pertinent challenge to cloud adoption. Complexity of multi-cloud and hybrid cloud environments bring in more intricacy and makes it complex to transition to cloud decision.
Security is often envisioned as the major obstacle to cloud adoption, however in reality, it can act as a major accelerator when combined with automation. Automating cloud security equips organizations to proficiently gather the critical information needed to protect their cloud workloads. It is the use of automated tools and processes to enhance and manage the security of cloud environments efficiently. Gartner says over 85% of companies will adopt a cloud-first strategy by 2025. This trend enables you to implement their digital plans using cloud-native designs and technologies, underscoring the growing importance of cloud security.
With that, dive into cloud security automation — its advantages, best practices, strategies, and top tips — which enterprises can embrace to realize benefits to businesses.
What is Cloud Security Automation?
Cloud security automation uses automated tools and processes like continuous monitoring, automated compliance checks, vulnerability scanning, and Identity and Access Management (IAM) to manage and boost security in cloud environments.
As more companies move to cloud-first plans, their cloud operations grow more complex and larger. This calls for strong security measures that can keep pace with ever-changing cloud services.
Automation comes in handy here, offering consistent, reliable, and scalable security answers.
The Business Wire also reported that the cloud computing market is projected to reach $1,251.09 billion by 2028, growing at a compound annual rate of 19.1% during the forecast period. This quick expansion shows how crucial it is to find good ways to protect the cloud.
Cloud security automation is applicable to various types of businesses for security management. Here are a few to name.
- Small and Medium Enterprises (SMEs): Streamline security operations without needing extensive in-house know-how.
- Large Enterprises: Handle huge and intricate cloud setups with uniform and expandable security steps.
- E-commerce Companies: Guard delicate customer info and make sure transactions stay secure.
- Financial Institutions: Keep vital financial data safe and stick to tough regulatory rules.
- Healthcare Organizations: Shield patient records and follow health information privacy laws.
- Tech Startups: Put energy into new ideas while keeping strong security practices from the start.
- Retail Businesses: Keep customer data and transaction details safe, boosting trust and dependability.
- Government Agencies: Keep sensitive information safe and follow national security rules.
- Educational Institutions: Keep student and teacher information secure, making sure the online learning space is safe and follows the rules.
- Non-profit Organizations: Keep donor and work information safe to stay honest and trustworthy.
Now that you’ve understood what Cloud security automation entails, explore its numerous benefits.
Benefits of Cloud Security Automation
Picture security automation as your trusty copilot guiding you through the maze of cloud security while you keep your eyes on growing your business. Much like how autopilot eases the job for pilots, security automation cuts down on your IT team’s workload.
This lets them zero in on big-picture plans instead of doing the same tasks over and over. Here’s what you get when you bring in security automation.
- Less Time Spent on Security Operations: Automated processes handle routine security tasks. This frees up your team to focus on higher-value activities and strategic planning.
- Consistent Security Operations: Automation makes sure that security measures apply across your entire cloud environment. This cuts down on the variability and inconsistency that often come with manual efforts.
- Reduction in Manual Errors: By automating security tasks, you lower the risk of human error. This boosts the overall reliability and effectiveness of your security operations.
- Advanced Security Measures: You can set up and deploy complex security protocols and measures without manual intervention. This ensures that your security stays up-to-date and strong.
- Better Compliance: Automation has an impact on keeping up with regulatory standards. It keeps an eye on and enforces compliance rules non-stop. It also creates audit reports and sends out alerts right away if something’s off.
- Quick Spotting and Fixing of Security Problems: Systems that run on their own can spot and deal with security threats quickly. This means less time to respond and less damage from possible security issues.
Now that you know the benefits of Cloud security automation, get into the 5 steps for implementing it successfully. Also read latest blog on Cloud Security Strategies
5 Steps for Successful Implementation of Cloud Security Automation
As you rely more on cloud services, the number and complexity of potential weak spots can feel daunting. That’s where Cloud security automation steps in, acting like a trusted helper to assist you in managing and protecting your cloud setup.
By using machines to handle routine security jobs and make sure rules are followed, you can zero in on what you excel at — coming up with new ideas and expanding your company — without always fretting about security threats.
Here is an overview of the top five ways to set up cloud security automation to keep your online assets protected and maintain a strong defense against attacks.
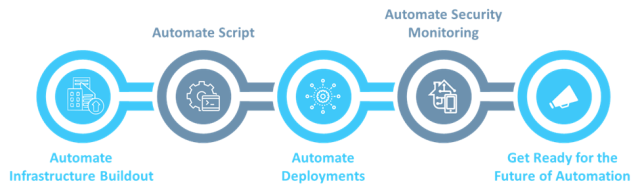
Automate Infrastructure Buildout
Automating infrastructure buildout frees engineers from setting up security groups, networks, user access, firewalls, DNS (Domain Name System), and log shipping by hand. This cuts down the chances for engineers to make security errors.
Also, automation means the security team doesn’t have to think about best practices every time they start a new instance. They just need to change the scripts, not the instances, to make updates.
Automate Script
In old-school IT, when a zero-day bug or any big security workflow problem pops up, an organization’s tech team must work hard to fix every server by hand. But with automation scripts, you just need to change one line in the setup files to make sure the newest version is up and running.
These automation script tools are straightforward management resources that set up instances of virtual servers or even physical servers.
When a new instance starts up, these scripts get it ready for use right away. They handle security setup tasks like setting up central login, putting in systems to spot intruders, and turning on two-step verification.
Automate Deployments
While making deployments automatic is a top DevOps practice, it also has a positive impact on an organization’s security stance. When a zero-day vulnerability strikes, automatic deployment ensures that any changes to the DevOps tool script get rolled out to every instance or server right away. This allows one system engineer to tackle threats quickly.
Automate Security Monitoring
In the rising popularity of hybrid and multi-cloud environments that support individual applications, engineers need to monitor the entire infrastructure in a single interface. When security attacks and downtime occur, finding and fixing the problem can drain resources and take up time.
Automatic security monitoring gives engineers the right information to tackle threats and protect critical assets.
Prepare for Automation’s Future
Data balloons and hybrid setups are set to become common in the next few years, which will make manual security methods less effective. So, now is the right time to build or hire an internal team for automation.
While it might take months or even years to automate processes across hybrid setups, it will turn out to be far more useful than teaching staff to make fewer mistakes.
With the steps for successful cloud security automation in mind, time to determine if it’s essential for your business.
Is Cloud Security Automation Important for Your Business?
Think about running a busy café with hundreds of customers each day. If you tried to keep track of orders, payments, and stock by hand, it would be messy, and you’d make lots of mistakes. Instead, you’d use a computer system to make these jobs easier, so everything works well.
In the same way, cloud security that runs by itself keeps your cloud setup safe, working well, and following rules without needing people to check on it all the time.
Here’s why cloud security automation matters so much for today’s big companies.
- Better spotting and handling of threats.
- Applying security rules and setups the same way everywhere.
- Ability to grow with the ever-changing cloud world.
- Staying in line with rules and regulations.
- Cutting down on costs by needing less human work.
- Setting up systems to find, analyze, and deal with issues on their own.
- Finding and fixing weak spots before they become problems.
- Making it easier to manage who can access what (IAM).
Understanding the importance of cloud security automation for your business, explore the stages of its framework.
Stages of Cloud Security Automation Framework
In today’s digital world it is crucial to take a planned and forward-thinking approach to keeping the cloud safe. That’s where the Cloud security automation framework comes in.
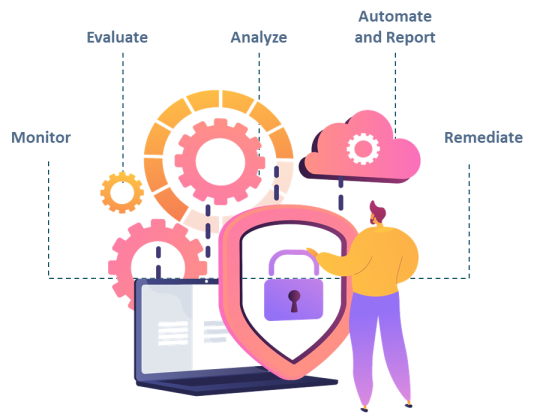
It’s a clear, step-by-step guide that helps strengthen your cloud setup against all kinds of threats. This framework doesn’t just make your security work smoother – it also shows how to bring automation into every part of your cloud safety plan.
Here is an overview of the stages of the cloud security automation framework.
Monitor
The cloud capacity will always grow or scale to meet all operational needs. Keeping tabs on the workflow of all tasks in the cloud security automation operations is crucial. This helps to grasp how each workflow happens.
Evaluate
When it comes to cloud security automation infrastructure, figuring out and ranking the tasks to automate is the key first move. Keeping a close eye on the work processes helps to assess tasks that need automation, such as repetitive jobs, cloud deployments that run on their own, setting up resources, and making security rules that work.
For instance, Let’s say your team spends a lot of time setting up resources for new apps by hand. By looking at this process, you spot that automating resource setup with tools like Terraform or Ansible can save time and cut down on mistakes. These tools let you define infrastructure as code speeding up and standardizing the creation of new environments.
Analyze
Analyze the gathered data to categorize it into low, medium, or high-risk severity. Start with low-risk cloud security automation processes, then move on to medium and high-risk ones. This detailed analysis also allows you to perform controlled automation and examine its effect on your infrastructure.
After the monitor and evaluate stages, you might discover that your system produces many low-severity security alerts, such as failed login attempts.
By examining these alerts with a tool like Splunk, you can set up automatic responses to low-risk incidents, like blocking suspicious IPs after several failed attempts. This approach lets your team concentrate on more serious threats while ensuring quick handling of less critical issues.
Automate and Report
The analyzed data can now be sent to connected systems to streamline the workflows. Next, set up the automation processes to create reports that provide a summary of the changes before or after.
Remediate
At this point, you’ll have a good grasp of cloud security automation whether you began with easy or tricky workflows. This allows you to put fixes in place and boost your overall automation security setup.
For example, after a few months of automating your cloud security tasks, you spot a problem that keeps coming back. Your first set of automation rules didn’t quite solve it. Using tools like AWS Config and AWS Lambda, you create automated fix-it plans.
These plans find and solve these weak spots as soon as they pop up. This might mean updating software or tweaking security group settings to block possible attack routes.
Having explored the stages of the framework, it’s crucial to address the challenges specific to cloud security automation.
Cloud Security Automation Challenges
Cloud security automation promises enhanced efficiency and robust protection, allowing organizations to stay ahead of cyber threats. However, the path to fully automated cloud security is fraught with challenges.
Here are the main challenges organizations face on this journey.
| Challenge | Description |
| Integration Complexity | Complex integration of various tools and systems like SIEM (Security Information and Event Management) and IAM (Identity and Access Management). |
| Managing False Positives | Filtering false alarms without missing real threats. |
| Ensuring Compliance | Aligning with diverse regulatory standards like GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act). |
| Scalability Issues | Scaling security measures for growing infrastructure. |
| Skill Gap and Expertise | Shortage of qualified personnel for management. |
| Cost Management | High initial setup and maintenance costs. |
| Maintaining Human Oversight | Balancing automation with human intervention. |
| Dynamic Threat Landscape | Adapting to evolving security threats like zero-day exploits and advanced persistent threats. |
Having identified the key challenges in cloud security automation, it’s now time to explore effective strategies to overcome these obstacles and strengthen your security posture.
Cloud Security Automation Strategies
Managing cloud security isn’t easy. It needs a well-thought-out plan. When you use cloud security automation, you protect your data better, work smarter, and follow the rules.
Learn about these strategies and how they can make your cloud setup stronger.
| Stage | Description |
| Use Infrastructure as Code (IaC) |
|
| Security Automation with CI/CD Pipeline |
|
| Policy-as-Code to Automate Enforcement of Policies |
|
| Auto Remediation in Incident Response |
|
| Adapt Security Orchestration |
|
The Future of Cloud Security Automation
As cloud computing keeps changing, the scene of cloud security changes, too. Cloud security automation’s future is causing a revolution in how companies keep their digital stuff safe.
As AI gets better, threat info comes in real-time, and rules get easier to follow, cloud security automation will get smarter, work better, and stay ahead of problems more often.
The future of cloud security automation promises the following.
- Enhanced AI Integration: Using Artificial Intelligence for smarter threat detection and response.
- Advanced Threat Intelligence: Real-time data analysis to preemptively address potential threats.
- Seamless Compliance: Automated compliance checks integrated into the development lifecycle.
- Greater Scalability: Effortless adaptation to growing and evolving cloud environments.
- Proactive Incident Response: Immediate automated remediation for faster threat mitigation.
Parting Thoughts
Automating cloud security offers numerous business advantages, yet it’s important to recognize that it can be more complicated and expensive than traditional, non-automated security measures. The necessary technology comes with costs and requires considerable time to implement. Additionally, establishing and maintaining effective security automation necessitates a high level of expertise.
Cloud Security services help enterprises in addressing compliance concerns that delay or minimize the migration of sensitive assets into private, public, and hybrid clouds. Calsoft supports its customers with automation of legacy processes to improve efficiency. With analytics and a touch of Artificial Intelligence, it facilitates digital transformation in an enterprise.






