Security Holes – Part 2
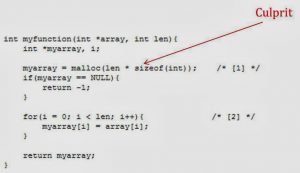
In Part-1 of this post we spoke about security holes and 2 sources of vulnerabilities: Buffer Overflow and SQL Injection. We will cover next 3 sources in…
Security Holes – Part 1
Technically, ‘Vulnerability’ is a cyber-security term that refers to a flaw in a system that can leave it open to attacks. In terms of computing, a resource…
